https://django-real-idm.herokuapp.com/admin
user: demo
password: demodemo
- python3.6 or newer
- Latest Ubuntu preferred. Tested with Ubuntu 20.04
- Install requirements
pip install -r requirements/dev.txt
- Initiate Django
# run in folder with manage.py
python manage.py makemigrations
python manage.py makemigrations djangorealidm
python manage.py migrate
python manage.py createsuperuser
- Load demo data (optional)
# run in folder with manage.py
python manage.py loaddata */fixtures/*.json
- Run
# run in folder with manage.py
python manage.py runserver
-
install docker-compose
-
Run docker-compose build
-
Initiate Django
docker exec django-real-open-idm-demo_djangorealopenidmdemo_1 python manage.py makemigrations
docker exec django-real-open-idm-demo_djangorealopenidmdemo_1 python manage.py makemigrations djangorealidm
docker exec django-real-open-idm-demo_djangorealopenidmdemo_1 python manage.py migrate
docker exec -it django-real-open-idm-demo_djangorealopenidmdemo_1 python manage.py createsuperuser
- docker-compose up -d
-
Go to
http://localhost:8000/admin/auth/user/and add your account (which you created usingcreatesuperuserto django existing groupapprover -
Navigate to
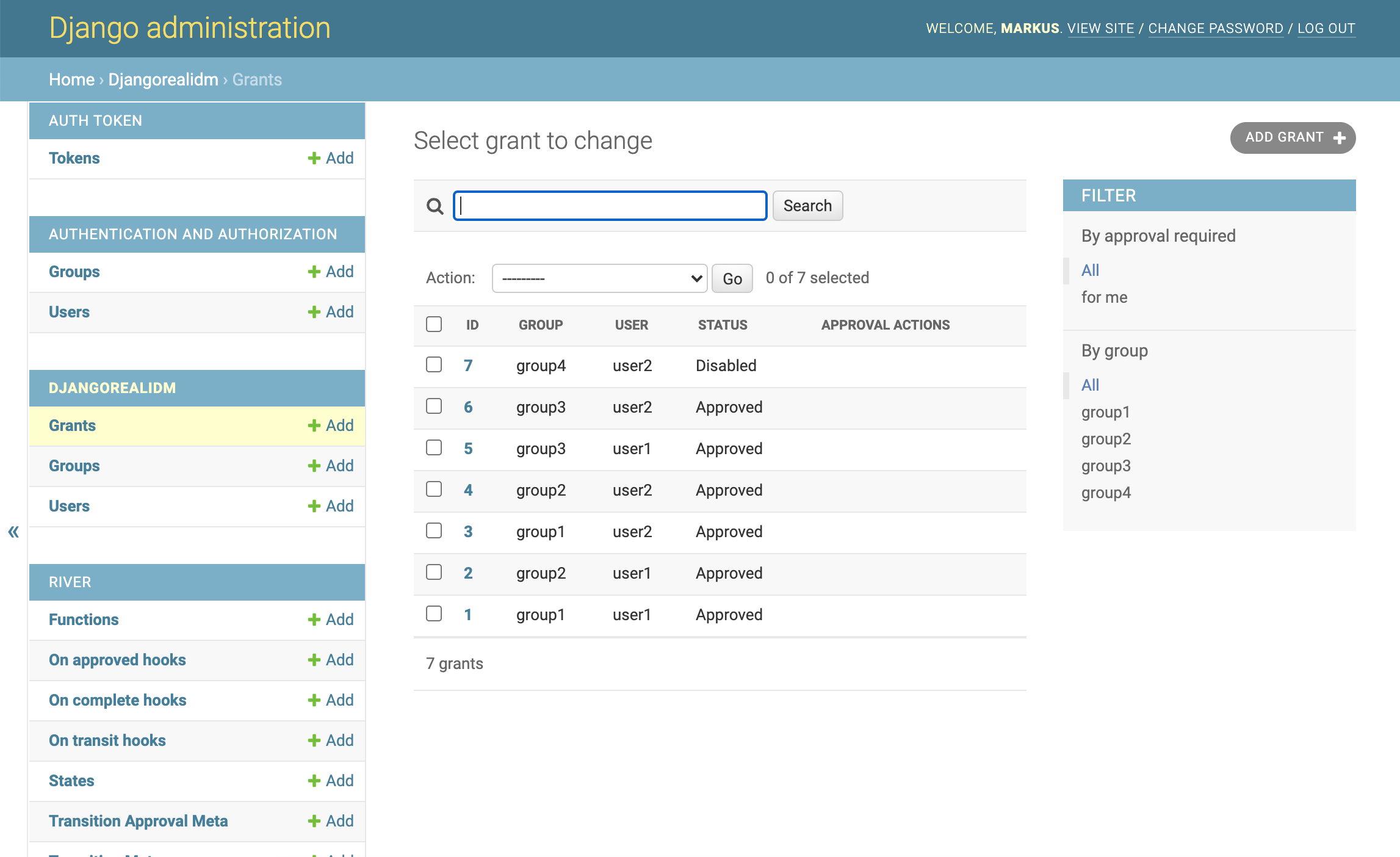
http://localhost:8000/admin/djangorealidm/grant/and try to create a new grant.
Example
Create new function in the admin-ui e.g. function name: sync-ad
from djangorealidm.utils import Sync
from djangorealidm.models import Group, User, Grant
from river.models import State
def handle(context):
s = Sync()
# TODO: Add role sync
approved_status = status=State.objects.get(slug="approved")
groups = [group.name for group in Group.objects.all()]
for group in groups:
users = []
for grant in Grant.objects.filter(
status=approved_status,
group__name=group,
status_transition_approvals__isnull=False # Retrieve grants for which approval has been explicitly granted. Prevents creating grant objects with 'approved' status
):
if grant.is_valid:
users.append(grant.user.username)
s.sync_users_groups(users, [group])Add LDAP configuration parameters in settings.py
REAL_IDM = {
'LDAP_SERVER': "", # required, server address e.g. '192.168.1.1'
'SEARCH_BASE': "", # required, where the groups and users are located e.g. 'dc=win,dc=local'
'BIND_USER': "", # optional, bind user e.g. bind@win.local
'BIND_PASSWD': "", # optional
'LDAP_USER_ATTRIBUTE': "" # optional, mapping for User.username and AD attribute name used to search the user from AD. Defaults to 'sAMAccountName'
}
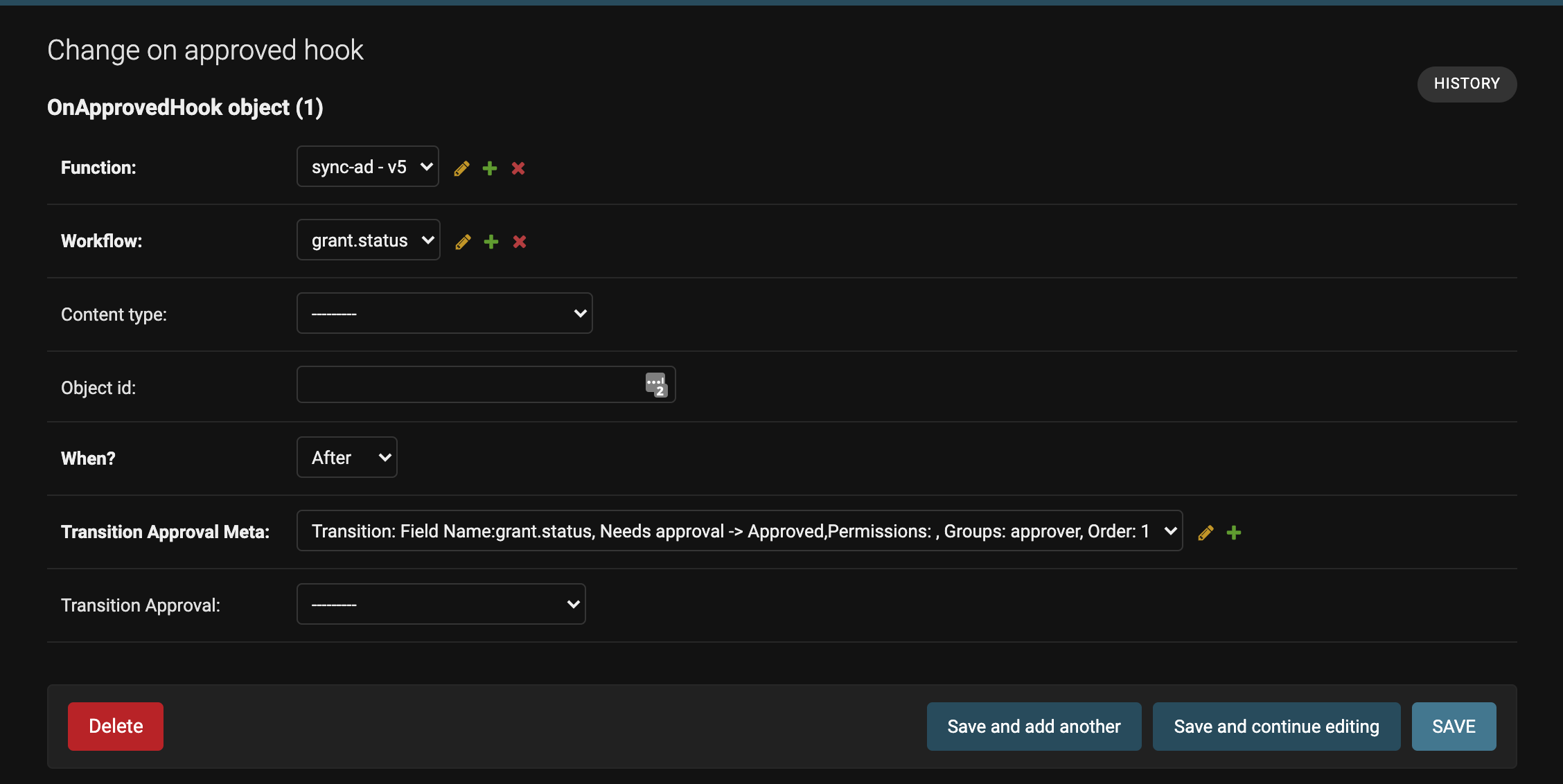
Create a new On-approved hook to sync group membership status after new approvals have been made and attach it to your workflow.
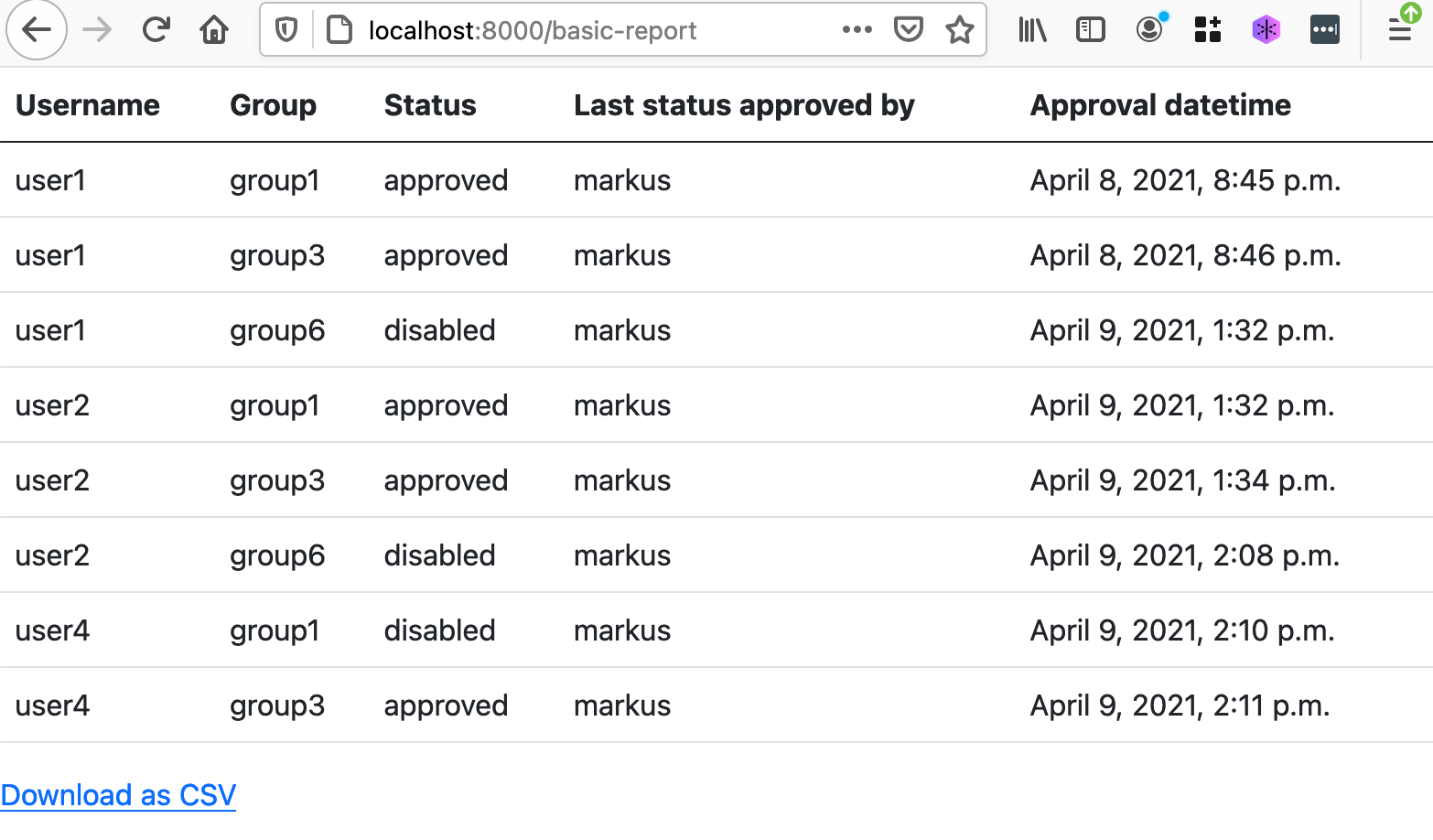
Go to http://localhost:8000/ for full list of reports available. Currently you are able to:
- View a basic report about current grants
- View a report about past approvals (history-report)
- Export reports to CSV
Roles are collections of groups which can be assigned to users if needed to ensure similar level of access to multiple users.
Note: role grants and group grants can exist simultaneously. Always consider that more specific grants should override less specific ones. E.g. user1 with disabled group grant in group1 should override an approved role grant which contains group1.