Safely use sensitive data with online tools. Browser extension to cut-off network access to a website to prevent it from phoning home. This allows you to input sensitive data into a website without worrying about it being stolen.
Do use this to convert/parse sensitive data:
- Parse a live JWT token in https://jwt.io
- Decode a Base64 Authorization header
- Hash a password for /etc/shadow
- Parse a Protobuf message
Do not use this extension to generate sensitive data:
- Generate a strong password online
- Generate a Bitcoin wallet online
- Generate a PGP key online
A malicious website may show you pre-generated data which may seem random to you, but is actually known to the attacker even before you load the website. Cutting off network access will not prevent this situation.
I would recommend to review the code, build the extension yourself and install it manually.
If you simply install the extension from the Firefox Add-ons store, you are implicitly trusting me that the extension does what it says it does.
You were warned: Get it from the Firefox Add-ons store
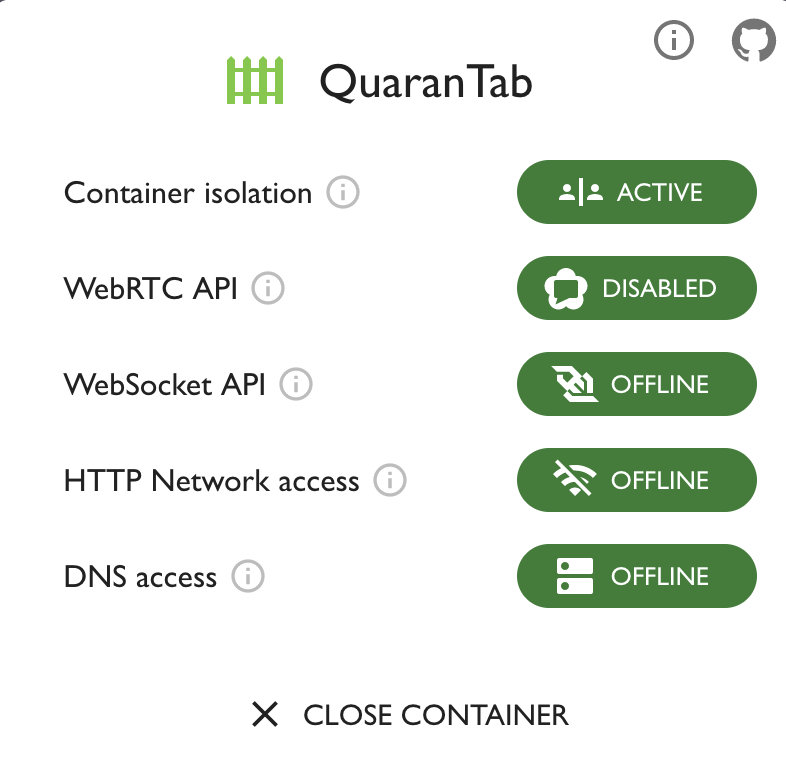
There are two steps to put a website under quarantine. One is to isolate it from all other website running in your browser using a temporary Container. The second is to cut-off network access to the website.
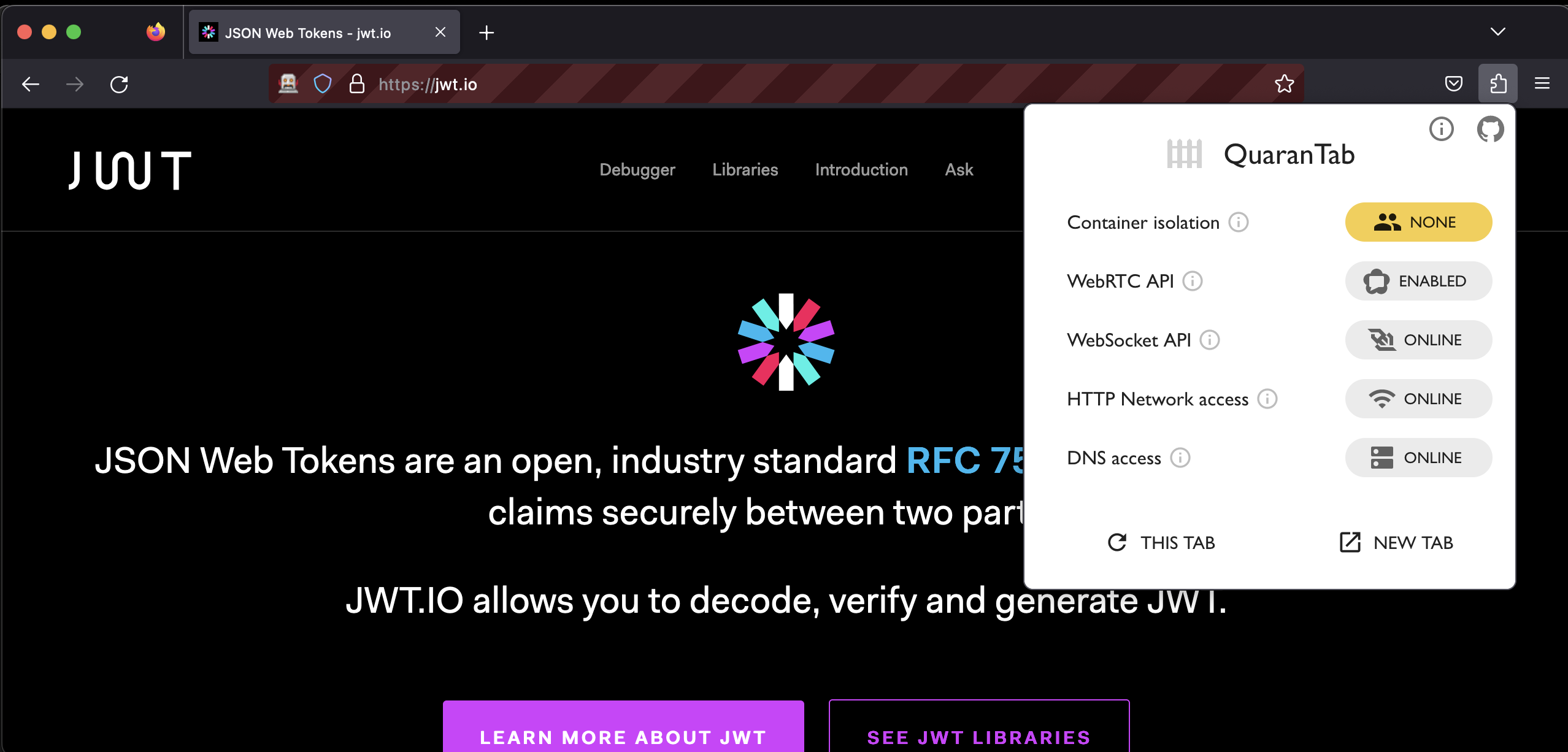
You may re-open your current tab or a new tab in a temporary container. This will isolate the website from all other websites running in your browser.
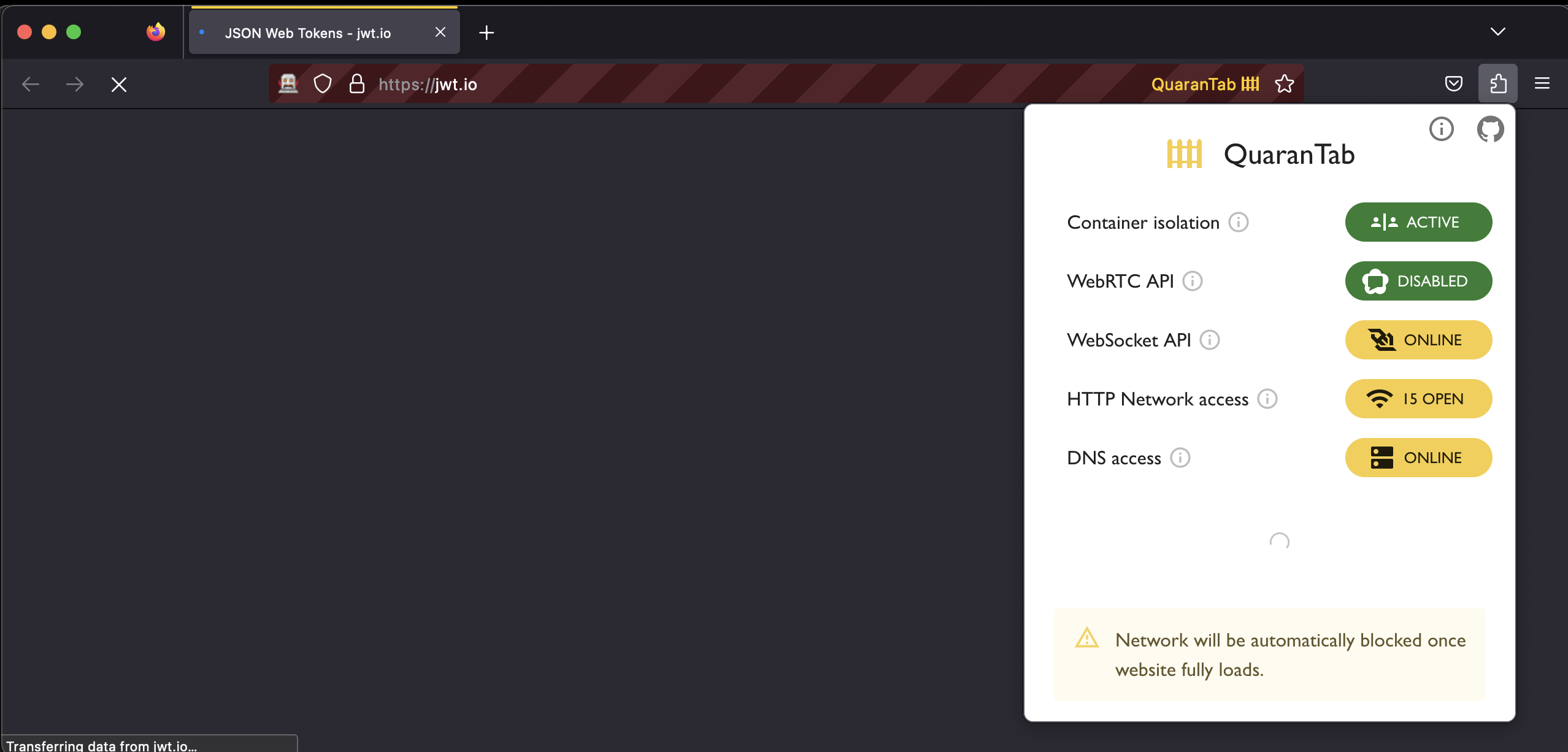
Next step is to cut-off network access to the website. This will prevent the website from phoning home and sending your sensitive data to a malicious server.
If you are re-opening your current tab, this step is automatic once the page fully loads.
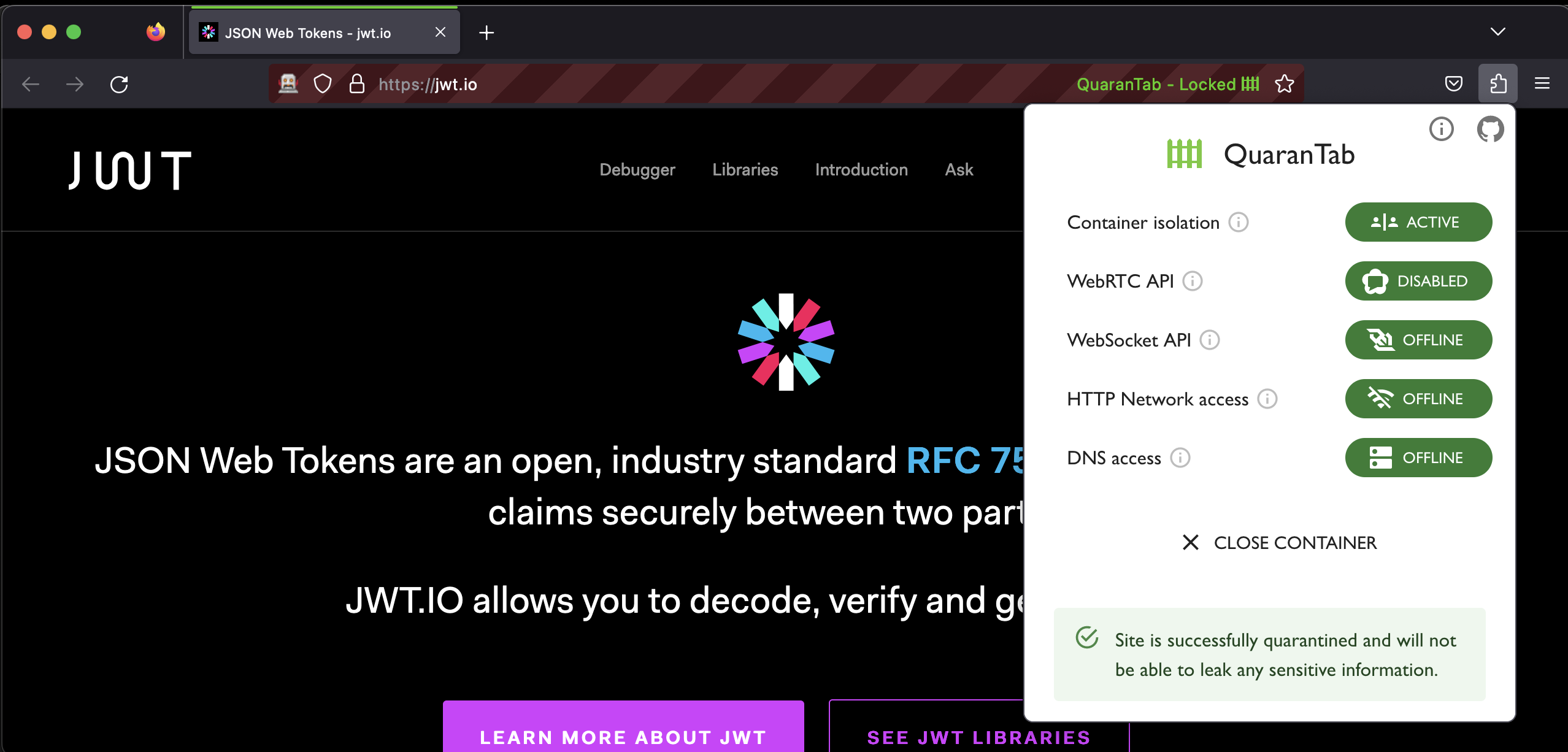
At this point, the website is completely locked down. You can now safely use the website and input sensitive data. No data will leak out of the website.
If a website stops working, it probably means that it depends on additional resources that it cannot fetch anymore because network access is cut-off.
Some tools actually work by sending your data to a server for processing, so they will not work with this extension by design.
When you are done using the site, simply close it and all browser data will be automatically deleted.
This extension takes advantage of Mozilla Firefox's contextualIdentities API to create temporary Containers in order to:
- Isolate a website from the rest of the browser
- Cut-off network access to just this Container
- Easily delete all data when you are done using the website
Interesting part is that the API semi-functions even without the Multi-Account Containers extension installed with a caveat:
- When calling
browser.contextualIdentities.remove, the Container is removed, but open tabs continue to be open and seem to be using a zombie-leftover of this container. The container cannot be referenced, but the site continues to operates as if it exists. This is a bug in Firefox. To solve this, I explicitly close all remaining tabs in that Container.
Attacks this extension protects against:
- Network access: Container is routed to a non-existent Socks proxy pointing to 127.0.0.1
- DNS leaks by routing DNS requests via Socks: site could try to resolve my-sensitive-info.badsite.com
- Storing sensitive data in Storage and Cookies
- Communicating with other websites
Out of scope attacks:
- Malicious other extensions communicating with the website
- Socks proxy running on localhost allowing communication with the website
- Container exploits
- Pre-generated data (e.g. using a Bitcoin Wallet Generator that shows you one of 100 pre-generated wallets)
Potential implementation in Chromium (Would love feedback here):
- Use private window as a temporary container
Due to the nature of this extension, it requires a lot of permissions. Ideally Firefox would allow extensions to enable offline-mode. Instead, we have to disable each possible network access individually.
- "proxy" - Required to cut-off network access to the website by routing requests to a non-existent Socks proxy
- "tabs" - Required to re-open a tab in a new container
- "cookies" - Required for manipulating Container data and clearing browser data for temporary containers
- "contextualIdentities" - Required for creating/deleting Containers
- "privacy" - Required for temporarily disabling WebRTC globally
- "webRequest" - Required for monitoring active connections to determine when it's safe to use
- "webRequestBlocking" - Required for blocking active connections and to redirect blocked page loads to an informational page
- "scripting" - Required for injecting a content script for shutting down active connections
- "storage" - Required for keeping track of WebRTC initial enable state
- "<all_urls>" - Required to intercept proxy web requests for all sites
If you find a bug, please report it to me. A bug bounty is available for this project as long as it meets the following criteria:
- The bug shows an exploit to exfiltrate data out of a website that is under a locked-down quarantine.
- You are the first person to report the bug.
- There are funds available in the bug bounty.
- The amount is proportional to the severity of the bug at our discretion.
- For an exploit that leaks any data under all circumstances, the bounty would be 100 USD.
- The bug exists in this extension or the design of it. It excludes explots in the browser itself, the contextualIdentities implementation or isolation guarantees.
Available: 100 USD
the amount will grow in the future proportionally to my confidence
- +100 USD Initial pool by @matusfaro (2023-09-10)
- -100 USD to @dz2742 for Established WebSocket session remains open (2023-09-11)
- +100 USD Replenished by @matusfaro (2023-09-11)
# Install packages
npm install
# Live Dev
npm run start firefox-
Clean up first
rm -fr dist node_modules tmp -
Upgrade dependencies with
npm update -
Bump version in
package.json -
Run
npm installto update lockfile -
Test extension with
npm run start firefox -
Commit changes
-
Build extension with
npm run build firefox(Call it twice as first time always fails) -
Upload
dist/firefox.xpito Firefox Add-ons store