IoT Edge v2 is made up of several independent services instead of one monolithic iotedged
-
Edge Identity Service
Handles provisioning.
-
Keys Service
Stores keys and allows callers to perform operations with those keys like encrypt, decrypt, sign.
-
Certificates Service
Stores certificates and allows callers to import and export them.
-
Module Runtime
Runs Edge modules, like
iotedgedtoday, though not necessarily specifically Docker containers.
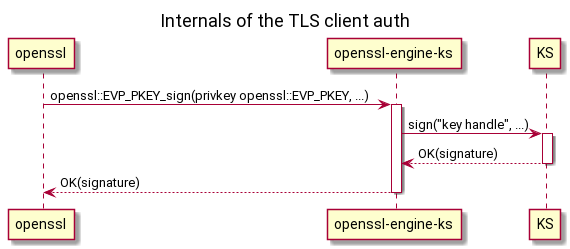
Each component talks to the other components over RPC of some sort (TODO: HTTP-over-UDS? gRPC-over-UDS? D-Bus? Something else?)
-
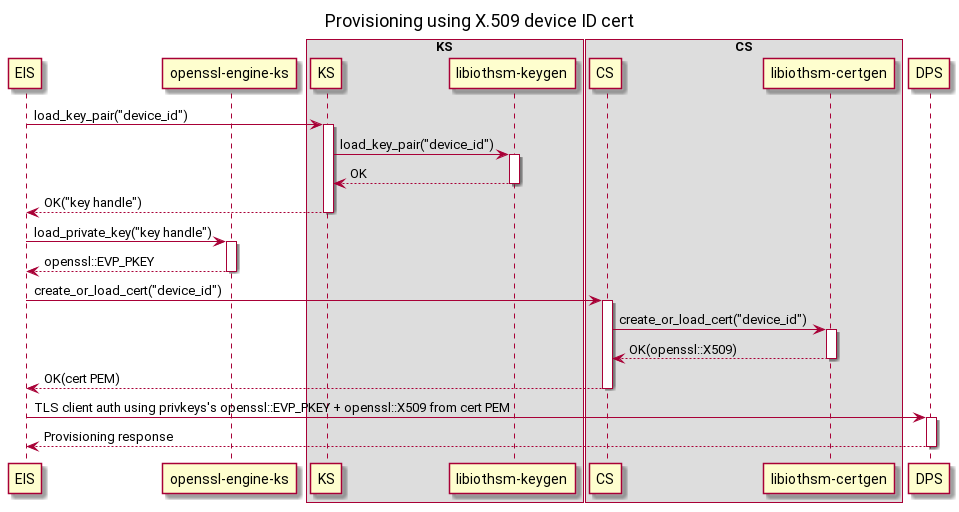
User preloads the device ID cert's privkey into their device's HSM and installs the PKCS#11 library to access it.
-
User configures KS to use PKCS#11 and preloads the device ID cert's privkey.
pkcs11_lib_path: '/usr/lib/softhsm.so' pkcs11_base_slot: 'pkcs11:slot-id=0?pin-value=1234' 'preloaded_key:device-id': 'pkcs11:slot-id=0;object=device%20id?pin-value=1234'
-
User configures CS to preload the device ID cert.
homedir_path: '/var/lib/iotedge/cs' 'preloaded_cert:device-id': '/var/secrets/device-id.cer'
-
User configures EIS with provisioning info.
provisioning: source: 'dps' scope_id: '...' attestation: method: 'x509' # TODO: If we decide certs and keys *must* come from KS and CS, then the URI is redundant and it could directly be the respective IDs. # Otherwise using a URI allows the scheme to determine other options for the source, like file:// for files. identity_cert: 'cert://device-id' identity_pk: 'key://device-id'
-
User starts KS, CS, EIS.
-
EIS performs provisioning.
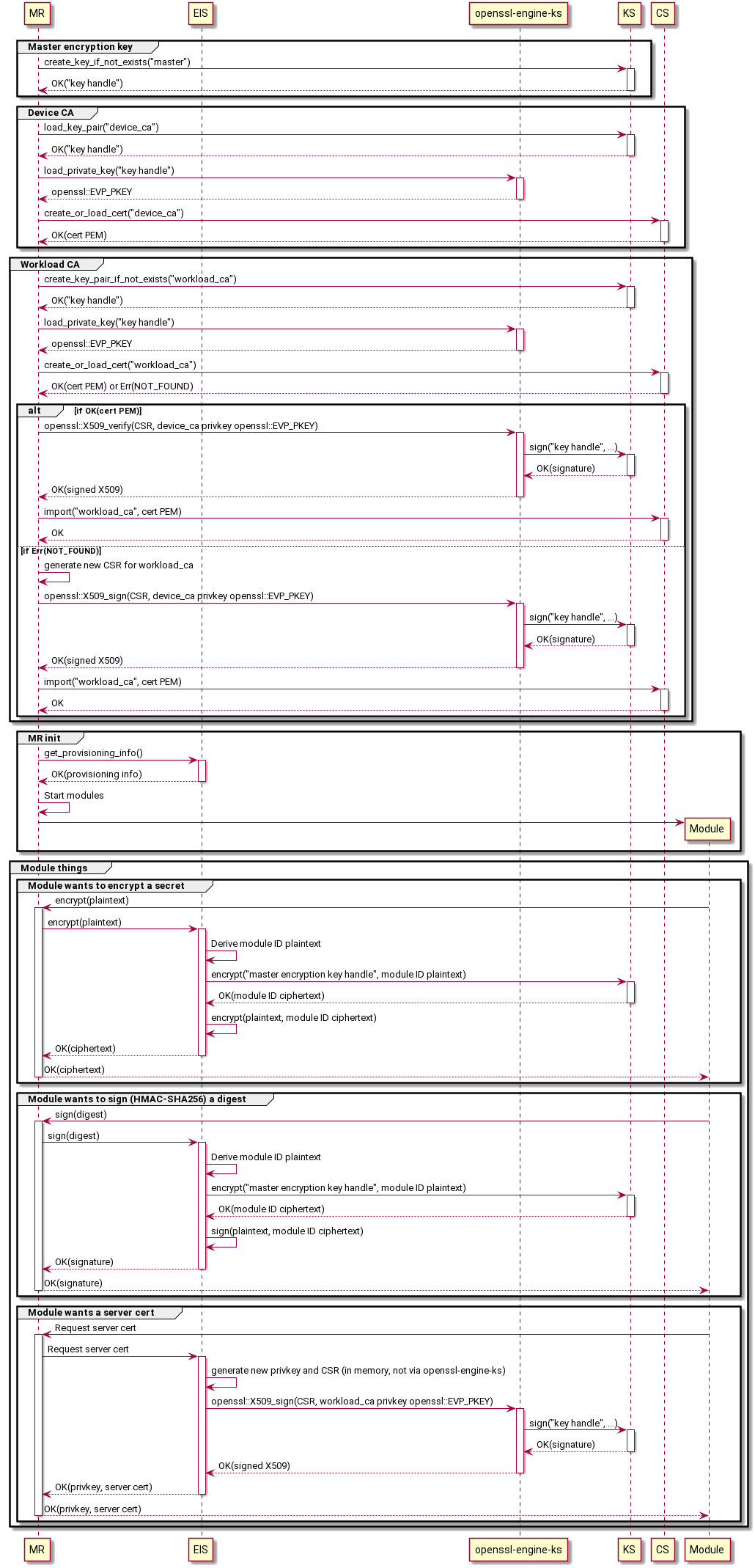
(This assumes device CA + workload CA are being used. For DPS-as-a-CA mode, ignore the device CA steps.)
-
User preloads the device CA cert's privkey into their device's HSM.
-
User configures KS to preload the device CA cert's privkey.
'preloaded_key:device-ca': 'pkcs11:slot-id=0;object=device%20ca?pin-value=1234'
-
User configures CS to preload the device ID cert and trusted CA cert.
'preloaded_cert:device-ca': '/var/secrets/device-ca.cer' 'preloaded_cert:trusted-ca': '/var/secrets/trusted-ca.cer'
-
User configures MR.
certificates: # TODO: Same point about URIs vs IDs as above applies here. device_ca_cert: 'cert://device-ca' device_ca_pk: 'key://device-ca' trusted_ca_certs: 'cert://trusted-ca' agent: name: 'edgeAgent' type: 'docker' config: {...} hostname: '...' connect: management_uri: 'unix:///var/lib/iotedge/mgmt.sock' workload_uri: 'unix:///var/lib/iotedge/workload.sock' listen: management_uri: 'unix:///var/lib/iotedge/mgmt.sock' workload_uri: 'unix:///var/lib/iotedge/workload.sock' homedir: '/var/lib/iotedge/iotedged' moby_runtime: uri: 'unix:///var/run/docker.sock'
-
User configures CS to preload the device ID cert.
homedir_path: '/var/lib/iotedge/cs' 'preloaded_cert:device-id': '/var/secrets/device-id.cer'
-
User starts MR.
-
MR does its work.