Leverage AMSI (Antimalware Scan Interface) technology to aid your analysis.
This tool saves all buffers (scripts, .NET assemblies, etc) passed into AMSI during dynamic execution.
AMSI is (originally) intended for application & AV vendors to interact with one another through a standard interface. Out of the box, it is integrated into the following Windows components for scanning:
- Powershell/JScript/VBScript (scripts, interactive use, and dynamic code evaluation)
- Office macros
- .NET Framework 4.8 (in-memory loading via Assembly.Load)
- Windows Management Instrumentation (WMI)
- ...
As malware (Windows) usually depend on one of these components within their execution chain, especially early on (e.g. downloader/dropper via maldoc), we can leverage this tool while dynamically analyzing a malware to unearth obfuscated code execution, dump assemblies that are dynamically loaded, and more.
This tool is an alternative solution to using event tracing (ETW) to get AMSI events, which may be cumbersome and not easily integrable into automated pipelines (e.g. sandboxes).
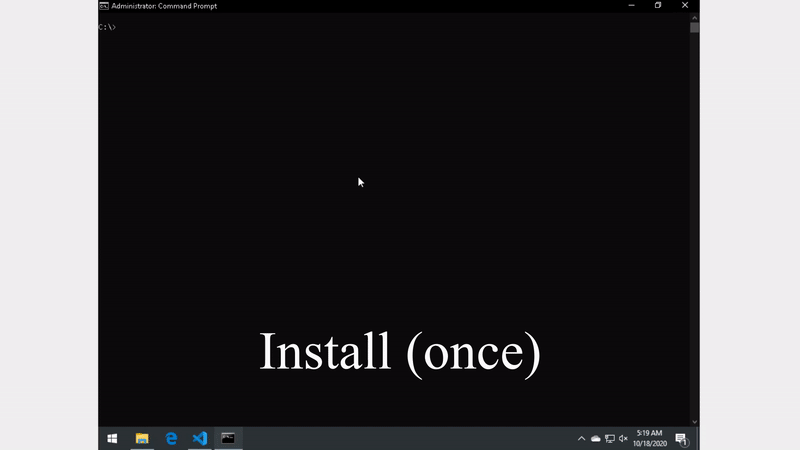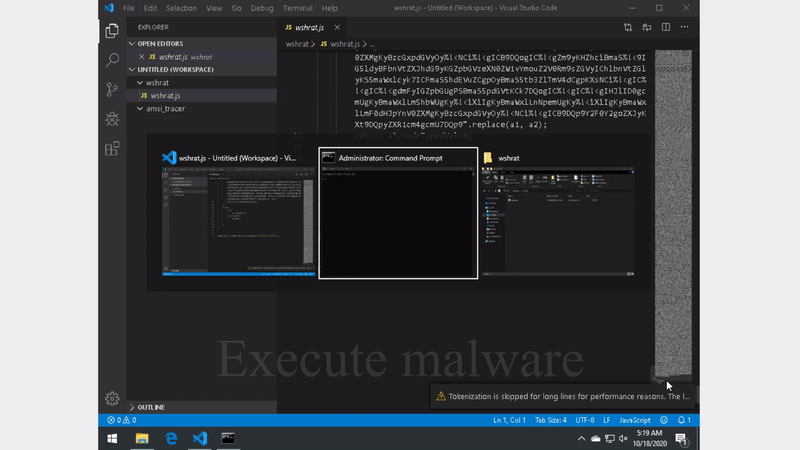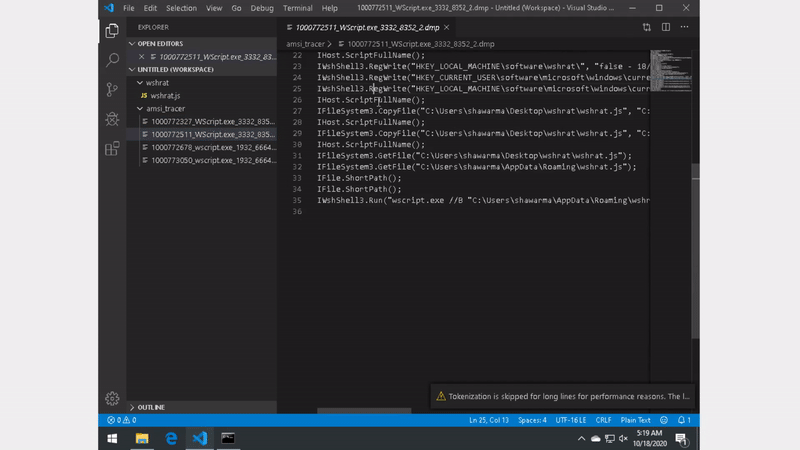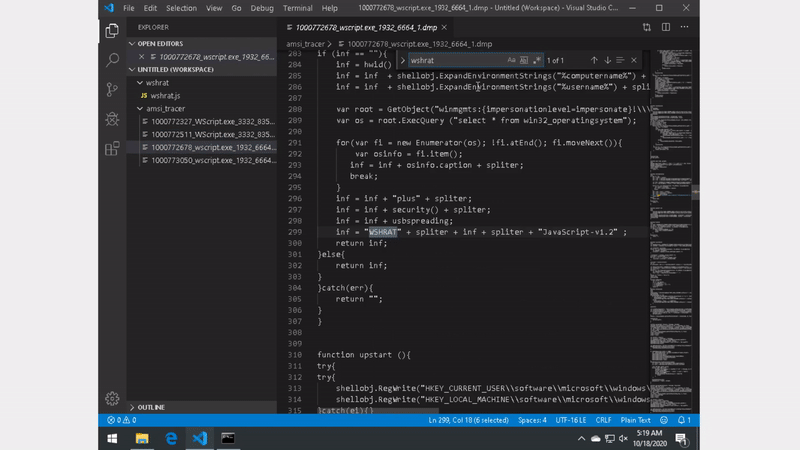
Once installed, the dumps are found at C:\amsi_tracer and have the following naming convention <epoch>_<processName>_<processId>_<threadId>_<counter>.dmp
AMSI is only available on Windows 10 / Server 2016 and above
Either modify/build the project from scratch or download the latest (x86/x64) builds to get the AMSI provider dll.
Ensure Visual C++ redist packages (2015-2019) are installed (x86 | x64).
Register the AMSI provider:
(elevated cmd) $ regsvr32.exe amsi-tracer.dllTo uninstall:
(elevated cmd) $ regsvr32.exe /u amsi-tracer.dllYou need to have Office 2016 (and above) or Office 365 installed.
Enable AMSI for all documents by setting the following registry key (Office 2016 example):
[HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Security]
"MacroRuntimeScanScope": (dword) 0x00000002
Here are some sample outputs:
Babax/Osno Stealer/Ransomware (XLS -> Powershell -> .NET)
Password: infected