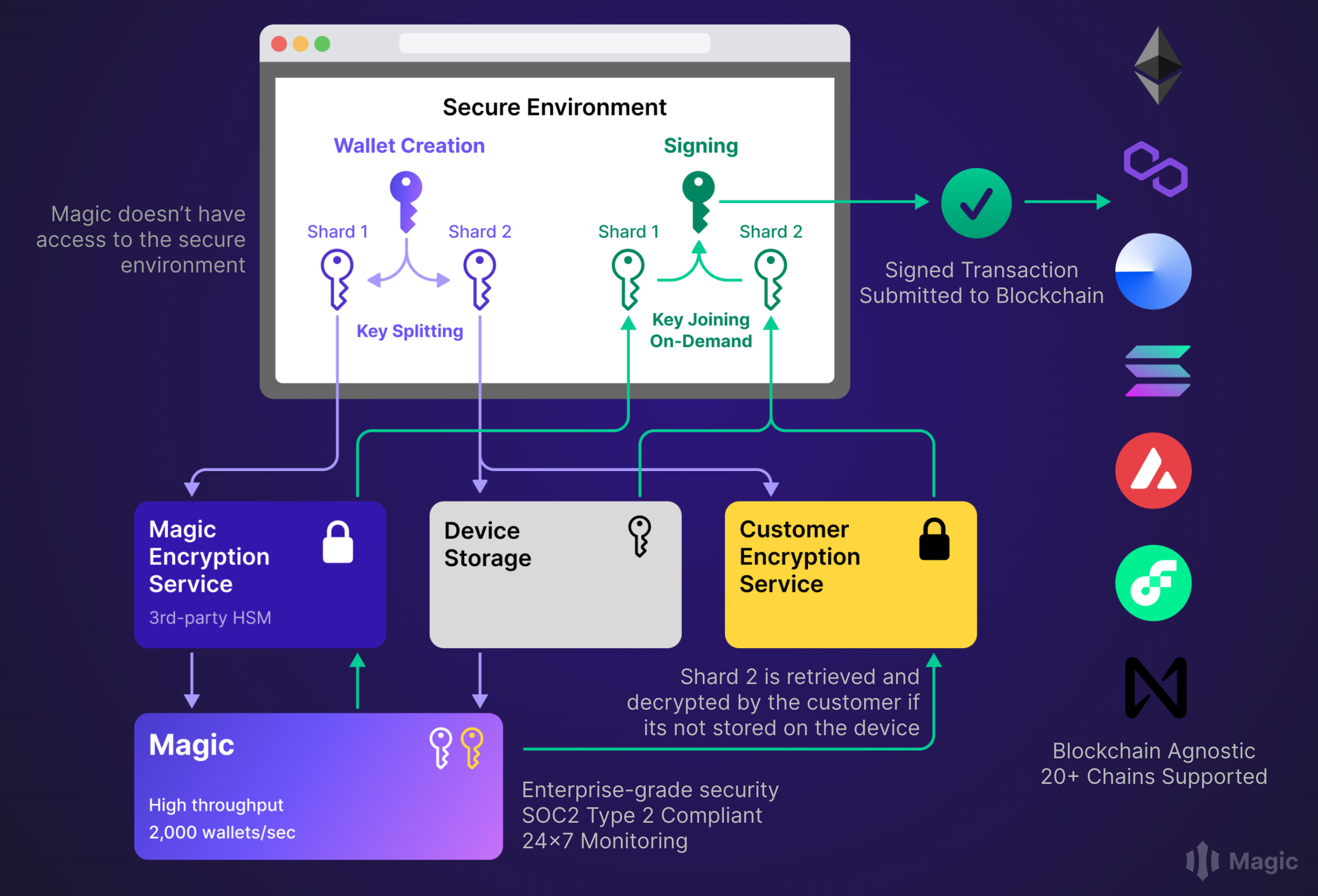
Magic offers non-custodial Wallet-as-a-Service, allowing web or mobile application developers to seamlessly integrate web3 wallets into their apps with a familiar web2 user experience. The cornerstone of Magic’s offering is its patented Delegated Key Management System (DKMS).
This repository introduces a novel shared security model where Magic’s developers can deploy a cloud-native, elastic infrastructure to encrypt segments of the private key, divided into multiple shares using the tested and proven Shamir's Secret Sharing algorithm. You can learn more about this wallet key management model in Magic’s developer documentation.
Below outlines the expected workflow for developers participating in the Modular KMS offering:
- Opt-in for Modular KMS when opening your developer account with Magic. Note that this feature is currently in invite-only mode; therefore, please contact sales to enable this functionality.
- Customers using Magic’s Modular KMS need to encrypt device hydration private key shares. To do so, fork this repository, make any modifications (if necessary), and deploy it to your AWS account. The encryption API tech stack is optimized for AWS Serverless Architecture, ensuring easy scalability.
- Register the API endpoints with Magic to receive callbacks for encryption and decryption at runtime when users create a wallet and perform signing transactions.
Sign up for a cloud vendor; currently, we support Amazon Web Services (AWS).
We have open-sourced this repository under the Apache 2.0 license, making it suitable for modification to fit the unique requirements of your production environment. View the license.
Currently we support AWS as the default cloud providers, we are looking to integrate this offering with other cloud providers such as Google Cloud and Microsoft Azure
We use AWS CDK for this repository. The following commands will help you deploy the CDK to your AWS account.
make install
make synth
make diff
make deployThe reference implementation of the CDK comes with a bring-your-own KMS model for encrypting and decrypting your share of the key. You are welcome to customize the configuration further to suit your needs, such as using an external HSM in place of AWS KMS.
Reach out to Magic customer support for assistance.