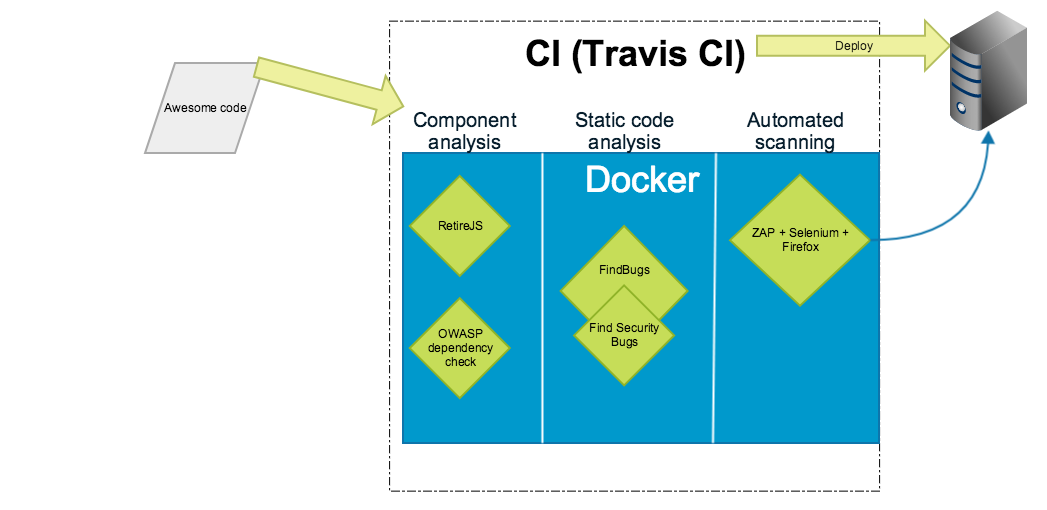
Demo project about automating security testing with Docker. In this case we are running the stuff with Travis CI.
Intentionally the source codes in this repository have some findings reported by the tools. Especially the Python application is intentionally vulnerable to attacks so do understand that running it on your own servers (as a demonstration) is a security risk!
Currently this repository demonstrates using these tools through Docker containers:
In the usual case scanning requires authenticating the test user with some credentials. This is not currently easy, but soon will be. See issue at GitHub.
Another common trick is to use some sort of custom HTTP header (mocking SSO frontend for example) which specifies the authenticated user. This can be achieved like this. Load a custom script which forces a HTTP header for each request.
zap-cli scripts load --name=force-auth --script-type=proxy --engine='Oracle Nashorn' --file-path=$(pwd)zap-header.js
Essentially zap-header.js boils down to this in this example:
function proxyRequest(msg) {
msg.getRequestHeader().setHeader("user-auth", "test-user")
return true
}
For real projects, you would probably want to tune the tools to generate HTML reports or something more readable and host these documents somewhere instead of having a load of stuff within the build server log. See sample Travis CI log as an example.
This is currently under development, but this example now uploads some of the generated reports to Amazon S3 bucket from Travis. This means basically mounting a local directory for the Docker container so that the container can write a file to the host machine. After container shuts down the file is then uploaded to S3.
Sample reports generated by the Travis CI build:
Given that there is an application written in Python for ZAP to scan, here's a sample from PYT tool designed to analyze Python programs. This tool is a static analysis tool for Python, similar to FindBugs in principle. However, it would appear that Pyt has a more sophisticated approach for it's analysis.
I can't say much about this tool at the moment, but at least it finds something so it's not completely useless:
1 vulnerability found:
Vulnerability 1:
File: flask-vuln.py
> User input at line 150, trigger word "get(":
¤call_2 = ret_request.args.get('name')
Reassigned in:
File: flask-vuln.py
> Line 150: ret_mystery = ¤call_1
File: flask-vuln.py
> reaches line 150, trigger word "redirect(":
¤call_1 = ret_redirect(¤call_2, code=302)