Compliance-Auditor
Compliance Auditor is a tool written to bridge the gap between expected configruation required for compliance and actual configuration.
Cloud Native Infrastructure, Platforms, and applications can establish OSCAL documents that live beside source-of-truth code bases. Providing an inheritance model for when a control that the technology can satisfy IS satisfied in a live-environment.
This can be well established and regulated standards such as NIST 800-53. It can also be best practices, Enterprise Standards, or simply team development standards that need to be continuously monitored and validated.
Hows it work?
The primary functionality is leveraging Kyverno CLI/Engine. Compliance Auditor:
- Ingests a
oscal-component.yamland creates an object in memory - Queries all
implemented-requirementsfor arulesfield- This rules block is a strict port from the rules of a Kyverno ClusterPolicy resource
- If a rules field exists:
- Generate a
ClusterPolicyresource on the filesystem - Execute the
applyCommandHelperfunction from Kyverno CLI- This will return the number of passing/failing resources in the cluster (or optionally static manifests on the filesystem)
- If any fail, given valid exclusions that may be present, the control is declared as
Fail
- Remove
ClusterPolicyfrom the filesystem - This is done for each
implemented-requirementthat has arulesfield
- Generate a
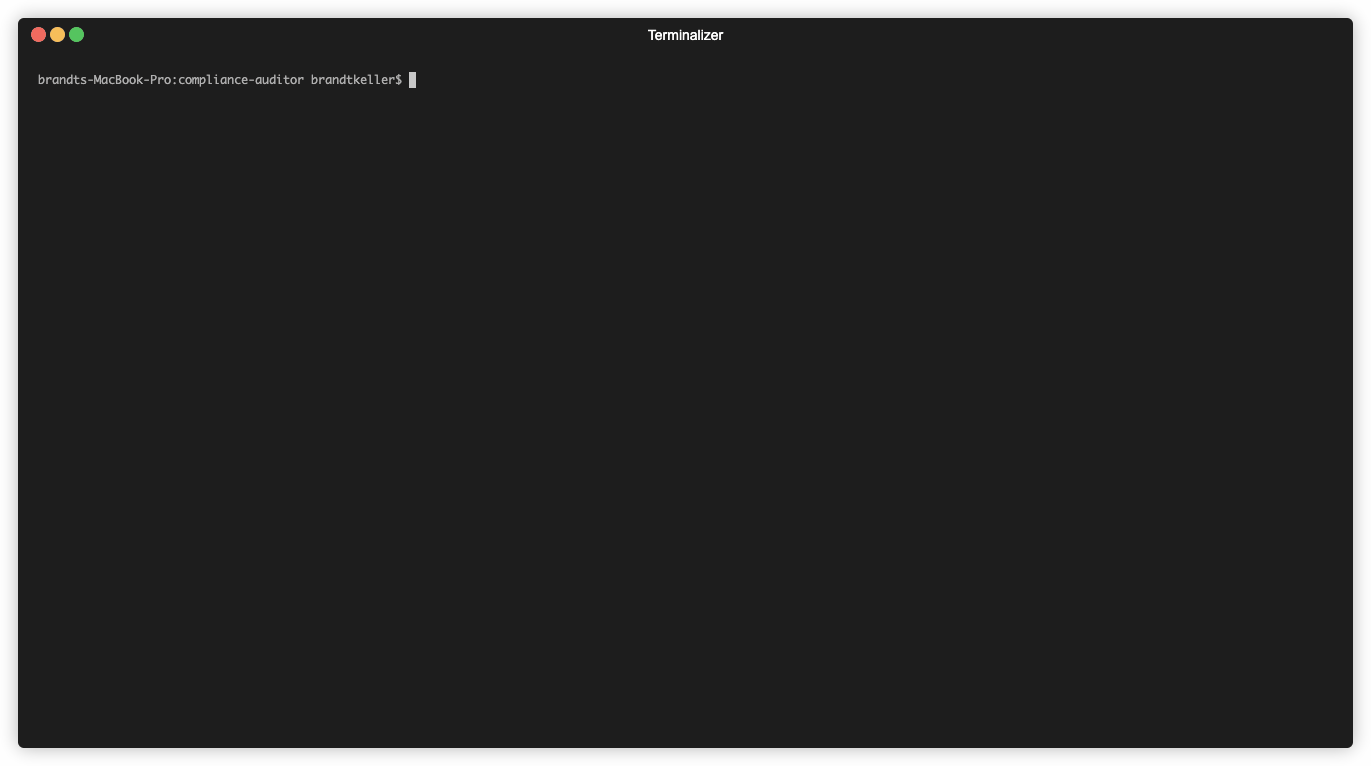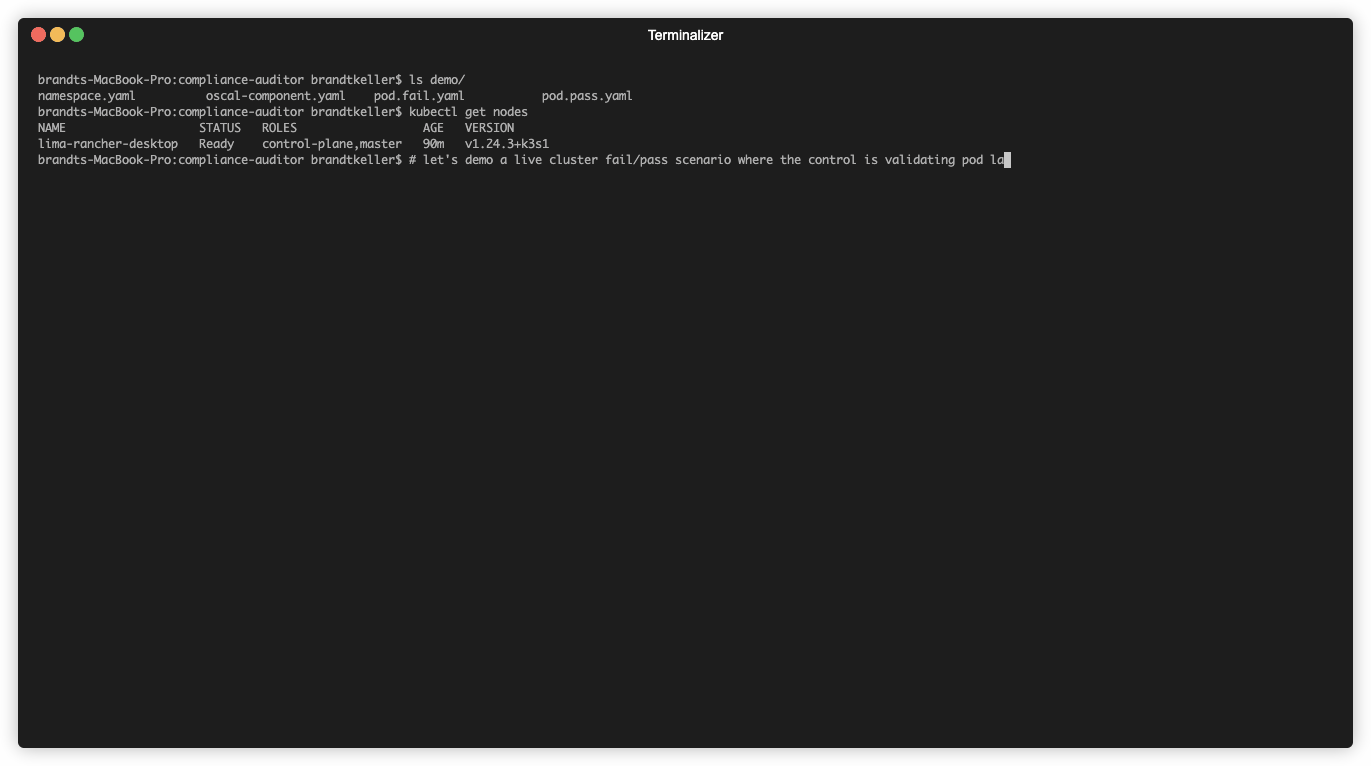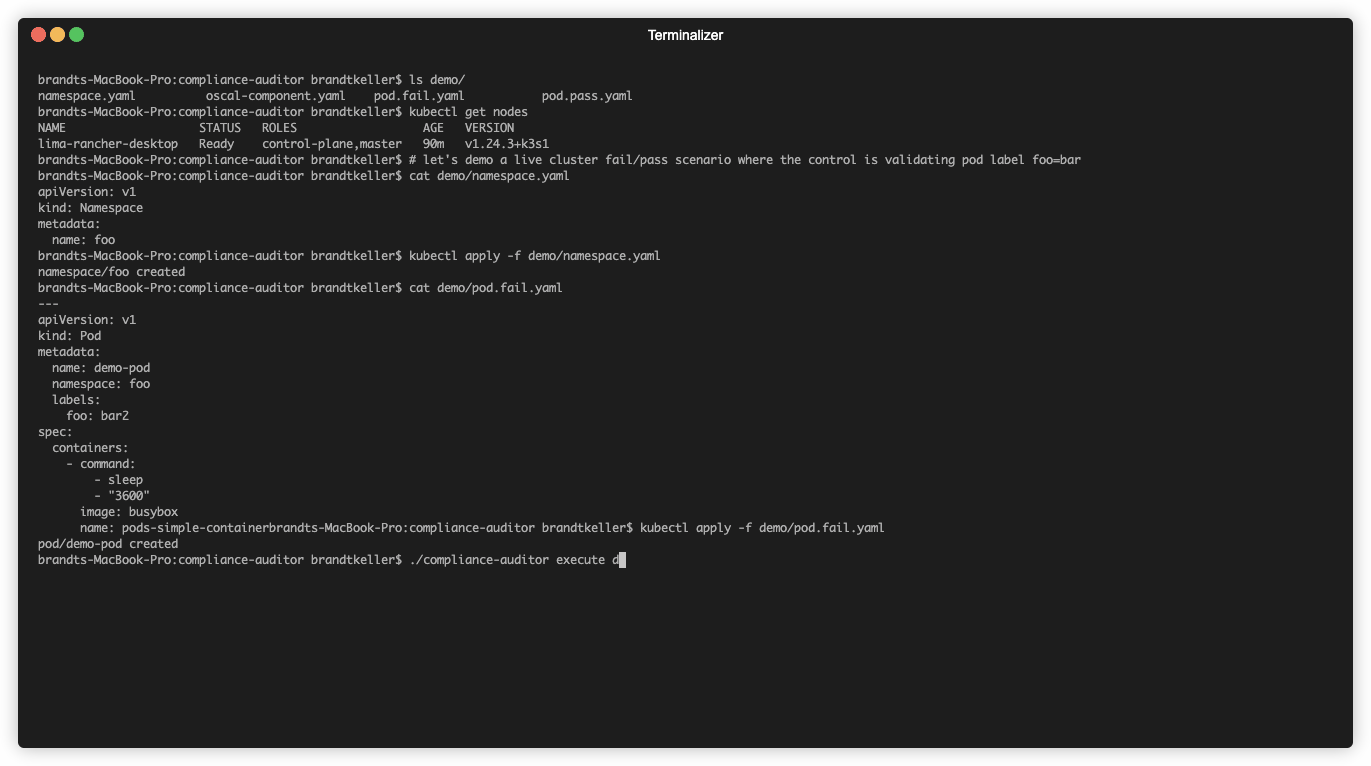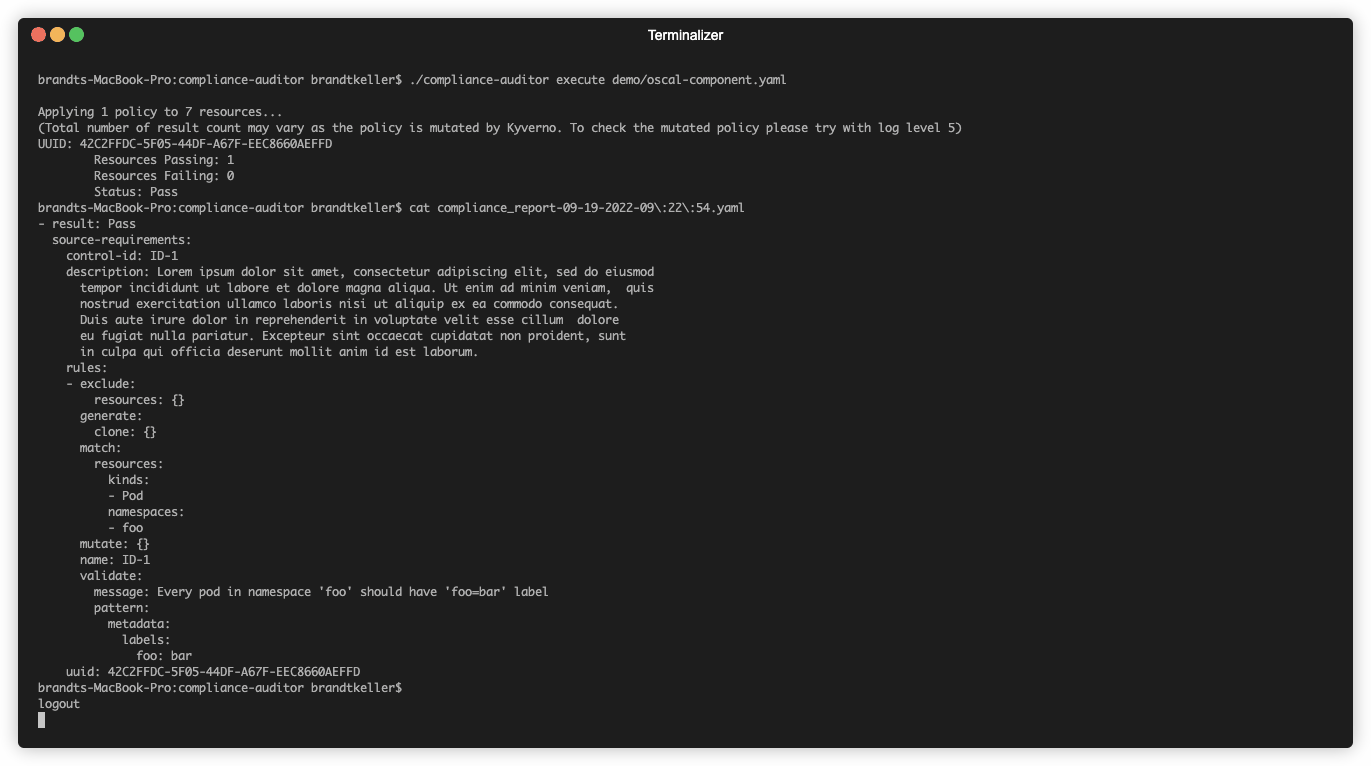
- Generate a report of the findings (
Passorfailfor each control) on the filesystem (optional - can be run with--dry-runin order to not write to filesystem)
Getting Started
Demo
Static Manifest Demo
Live Cluster Demo
Try it out!
Dependencies:
- A running Kubernetes cluster
- GoLang version 1.19.1
Steps
- Clone the repository to your local machine
- While in the
compliance-auditordirectory, rungo build .to compile the tool - Apply the
namespace.yamlfile in thedemodirectory to your cluster using thekubectl apply -f ./demo/namespace.yamlcommand - Apply the
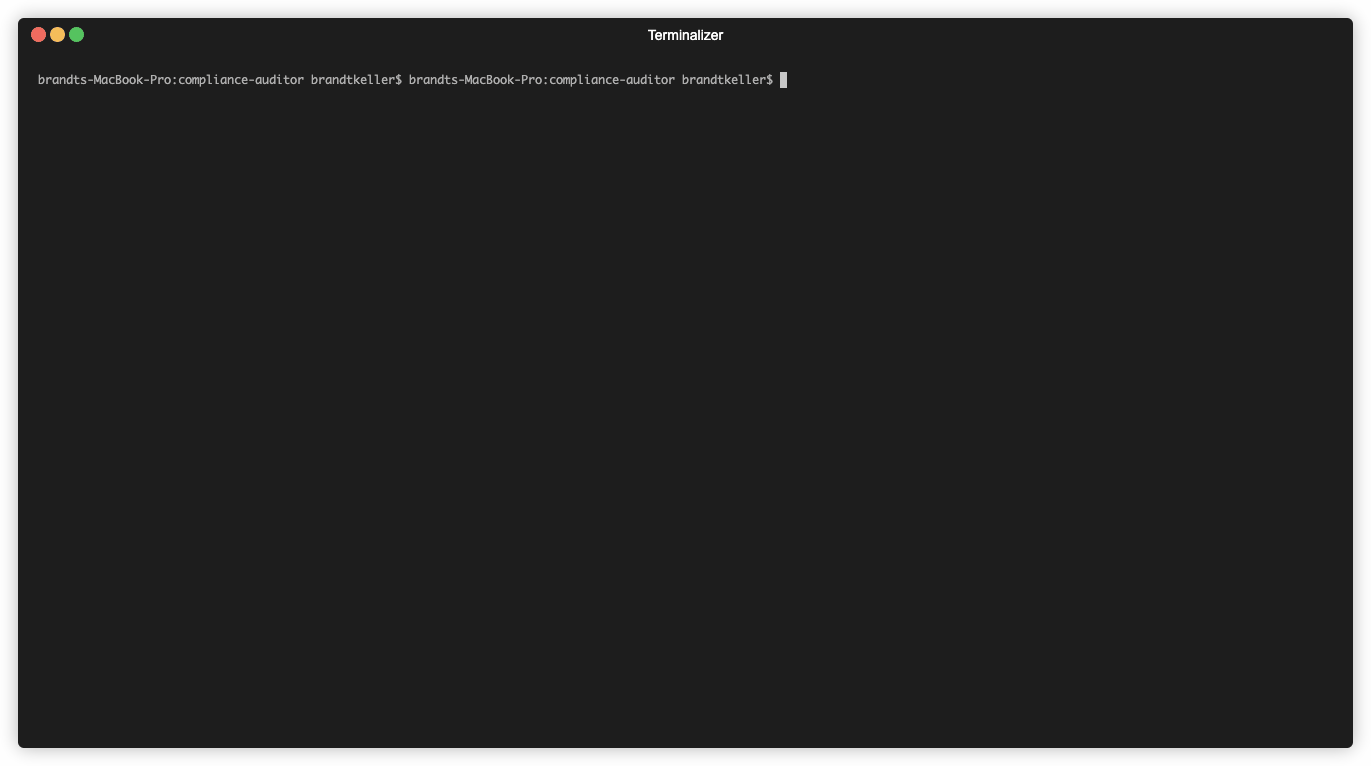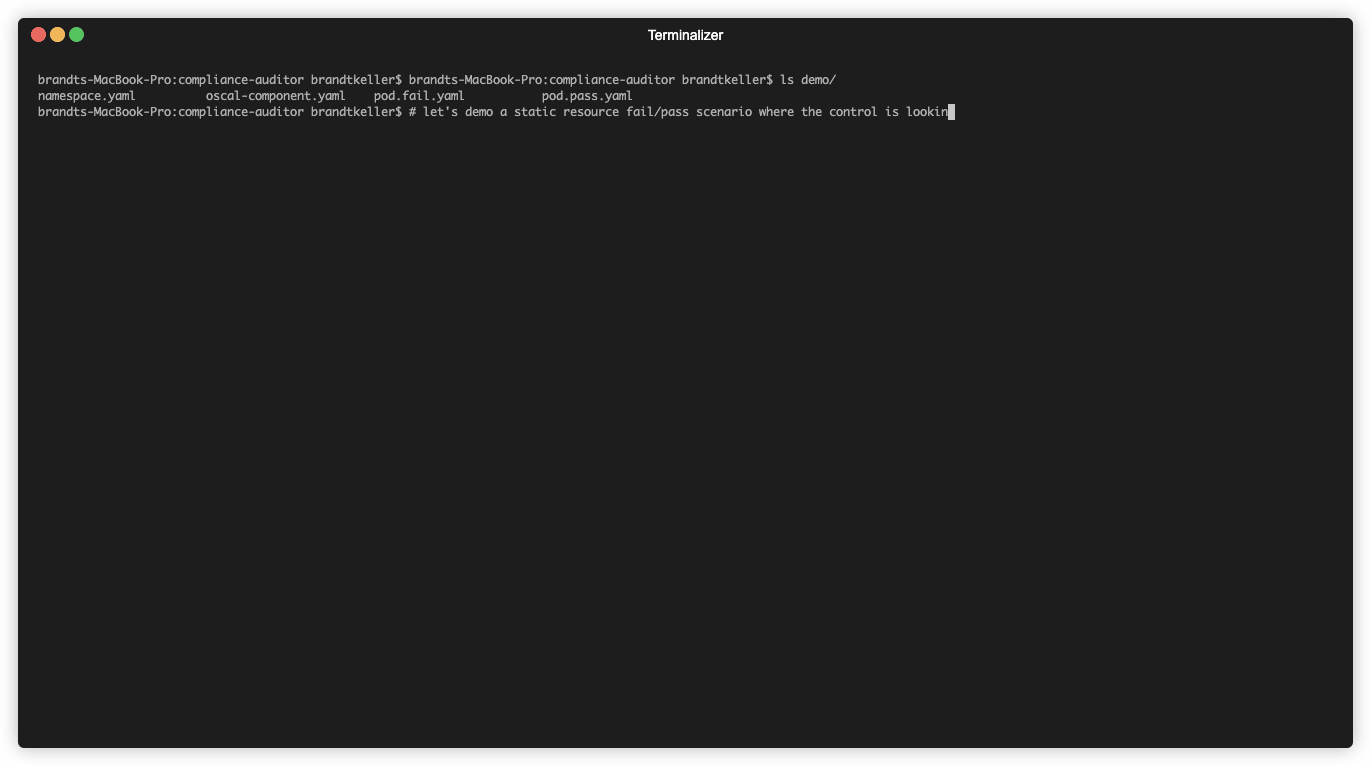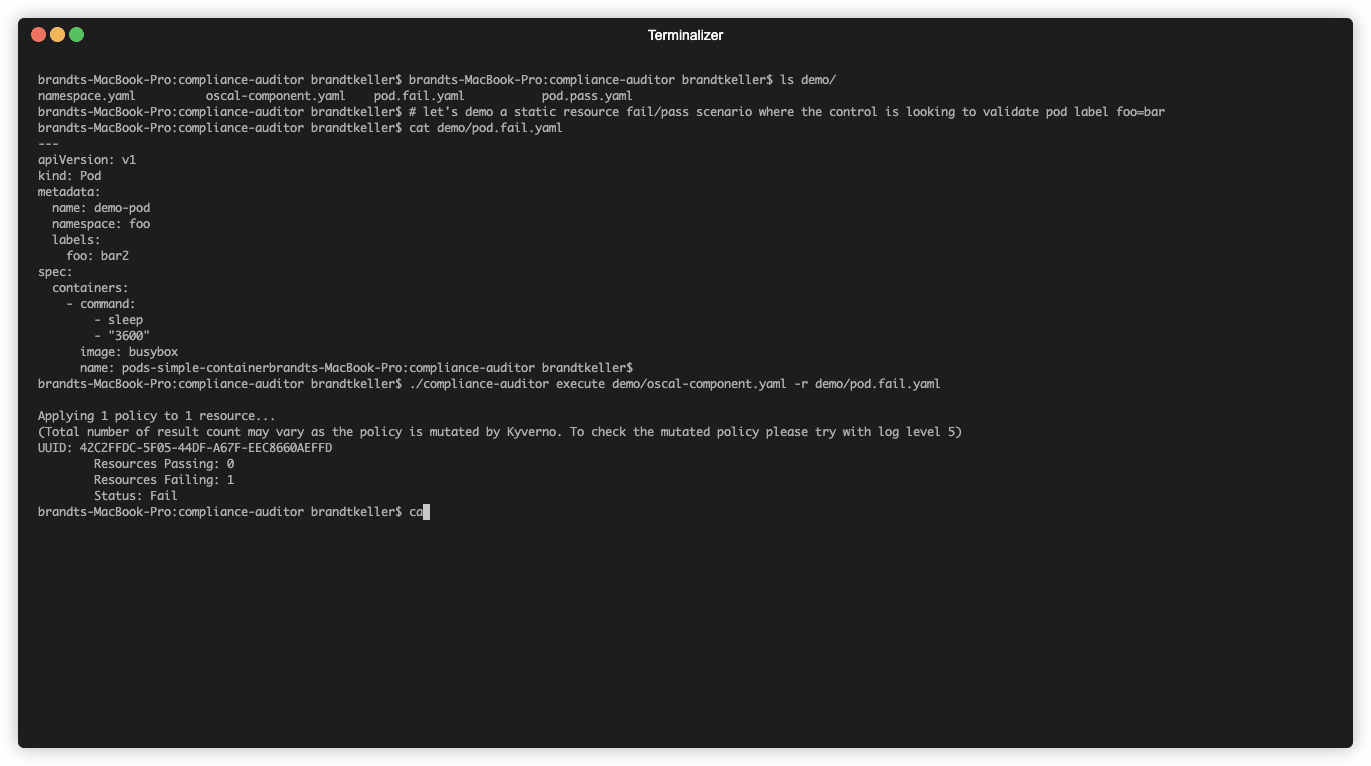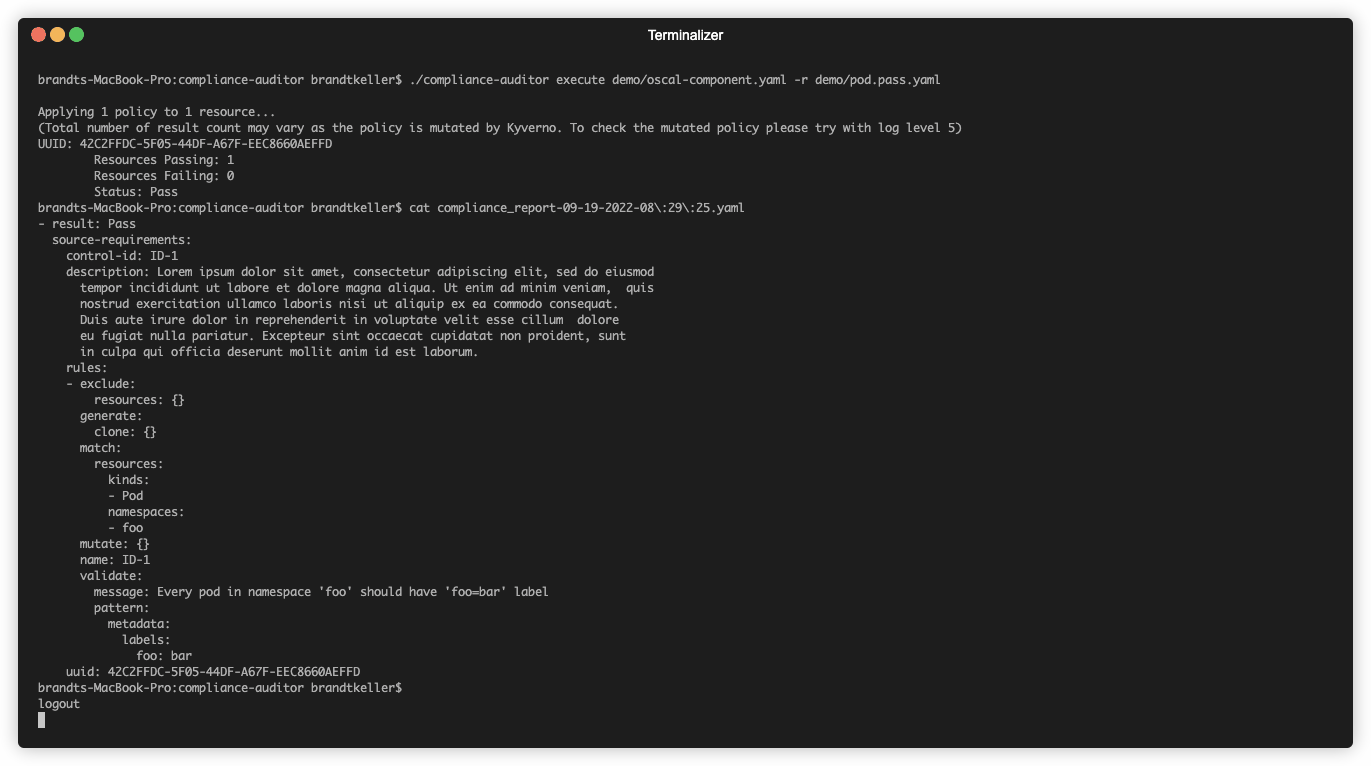
pod.fail.yamlfile to your cluster using thekubectl apply -f ./demo/pod.fail.yamlcommand - Run the following command in the
compliance-auditordirectory,./compliance-auditor execute ./demo/oscal-component.yaml- The tool should inform you that there is at least one failing pod in the cluster
- Now, apply the
pod.pass.yamlfile to your cluster using thekubectl apply -f ./demo/pod.pass.yamlcommand- This should modify the configuration for the pod to have the validation pass
- Run the following command in the
compliance-auditordirectory,./compliance-auditor execute ./demo/oscal-component.yaml- The tool should now show the pod as passing the compliance requirement
Future Extensibility
- Support for cloud infrastructure state queries
- Support for API validation
Developing
- GO 1.19