Pentesting Swiss Army Knife (P-SAK) is a Docker Image with the eleven ( four optional ) most used tools for Hacking and Pentesting. It allows you to use these tools easily and quickly on your Pentest from any OS supporting the Docker Engine. It has been developed using bitnami-docker-python as the base image and installing the following tools:
- NMAP - Utility for network , ports and service discovery in addition to security auditing.
- Metasploit - Most used penetration testing framework.
- Commix - Automated tool to test web-based applications with the view to find vulnerabilities related to command injection.
- Reconspider - OSINT Framework for scanning IP Address, Emails, Websites, Organizations and find out information from different sources.
- Wfuzz - It replaces any web reference to the FUZZ keyword by the value of a given payload.
- John the Ripper - Password cracking software tool.
- Tcpdump - Data-network packet analyzer
Optional tools:
- SQLMAP - Tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers.
- Nikto - Web server vulnerabilities scanner.
- Hydra - Password brute force cracking tools.
- Aircrack-ng - Complete suite of tools to assess WiFi network security.
You can build P-SAK using the following command:
$ git clone https://github.com/leoanggal1/P-SAK.git
$ cd P-SAK
$ docker build -t <image-tag> .You can build the image along with other optional tools using the environment variables in the Dockerfile.
| Tool | Environment Variable | Default Value |
|---|---|---|
| SQLMAP | SQLMAP_INSTALL |
no |
| Nikto | NIKTO_INSTALL |
no |
| Hydra | HYDRA_INSTALL |
no |
| Aircrack-ng | AIRCRACK_INSTALL |
no |
To enable these tools you have to change the default value of environment variables to yes.
For example, if you need Aircrack-ng and Nikto for your Pentest you must change the Dockerfile like this:
ENV SQLMAP_INSTALL="no" \
NIKTO_INSTALL="yes" \
HYDRA_INSTALL="no" \
AIRCRACK_INSTALL="yes"P-SAK has been developed to be a non-root image, following security best practises. The user psak has the UID 1001.
If you need root privileges execute the image like the following:
$ docker run --user 0 <image-tag>You can run the image in interactive mode with the command:
$ docker run --rm -it <image-tag> bashIf you only need to run one P-SAK tool, you can use the following command:
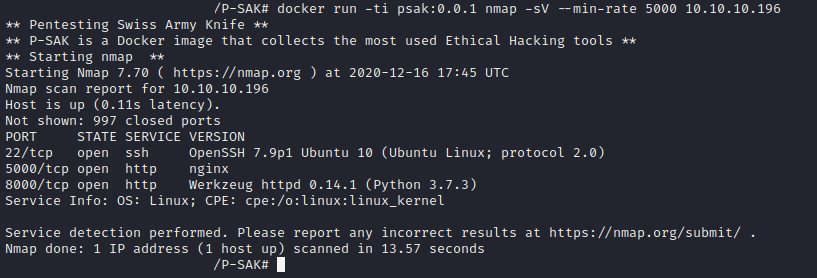
$ docker run -ti <image-tag> <tool-name> <tool-options>For example, to run a port scan using NMAP, use the following command:
$ docker run -it <image-tag> nmap -sV --min-rate 5000 <target-ip>The output obtained:
Want to contribute? Great!! You can request new features or create PR, we love contributions!
- Email: leopol.angul0@gmail.com
- LinkedIn: Leopoldo Angulo Gallego
Usage of P-SAK image for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this image.
Found this project useful? If you want, you might donate.
- For donate BTC : 12DuuMYdEHpANfWRZMxKcswftSuEpTj8Em
- For donate ETH : 0x23d1d8ccf69d4d634d25aaf01fe409f1ac4a7bce