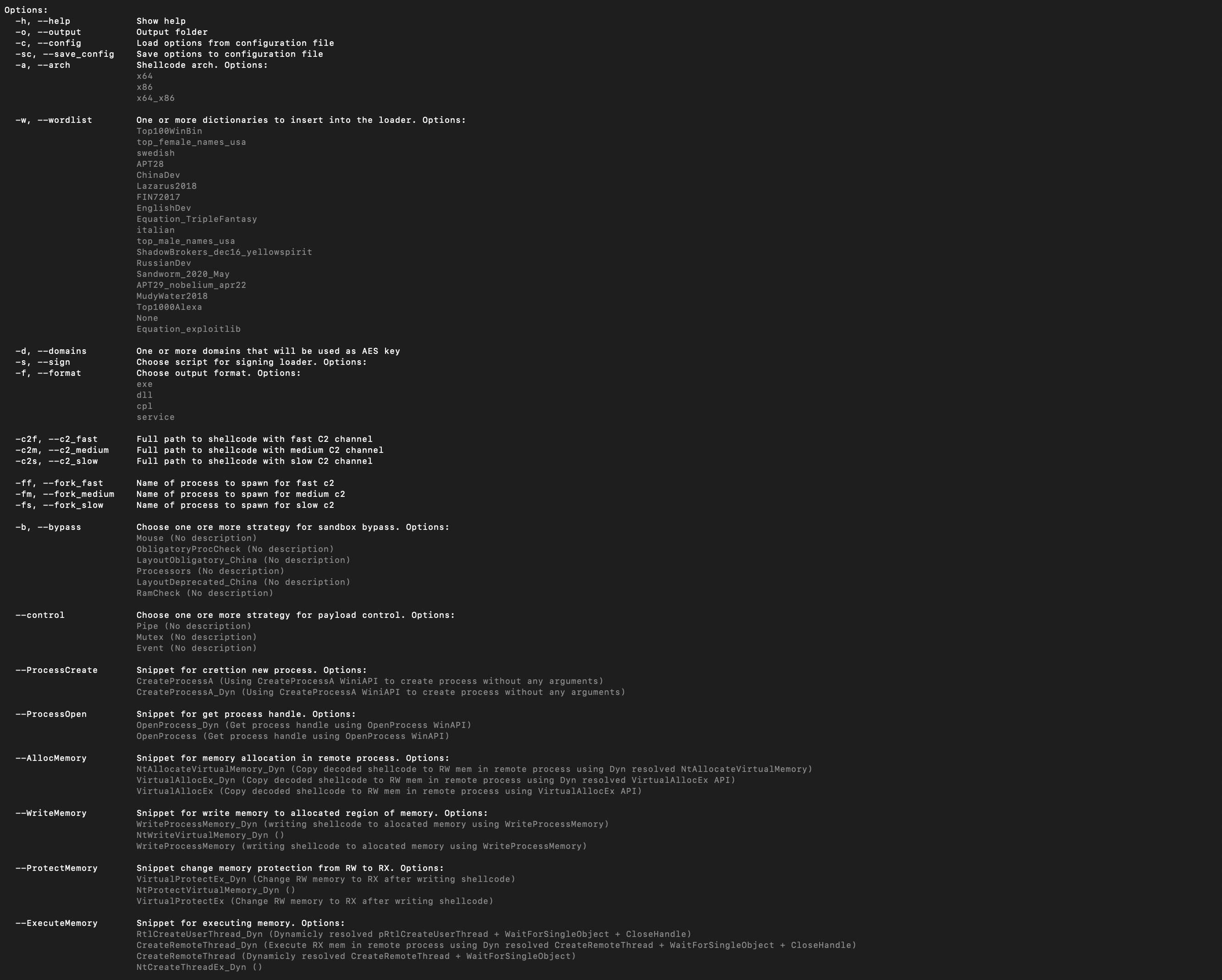
ShellcodePlayer is a versatile tool for configuring loaders for shellcode payloads. It allows you to dynamically generate loaders from templates and customize them according to your needs. The project provides options to add one or multiple sandbox bypass strategies and payload execution controls. It also enables you to remove specific strings from the output file, ensuring flexibility and variability in the generated payloads. With ShellcodePlayer, you can create templates for different stages of shellcode execution, allowing you to easily generate payloads with distinct behaviors. The tool supports various options for memory execution control, providing fine-grained control over the execution of the payload in memory. By default, the project encrypts the shellcode using AES with the target's domain name. You can add multiple domains, resulting in multiple encrypted shellcodes embedded in the loader. Upon execution, the loader attempts to decrypt the shellcode using the domain obtained on the host through WinAPI.
The user has control over IOCs (Indicators of Compromise) and can add them to a new dictionary and use it during compilation.
To make a string less noticeable in the bin file, enclose the string in <obf>"string_here"<ob_end>.
The user can save configurations used to build loaders and load them during runtime from JSON configuration files.
The execution flow of the loader is as follows:
- Sandbox Bypass Strategies
- Payload Execution Control Strategies
- QueryDomain
- AESDecrypt fast/medium/slow Shellcodes
- ProcessCreate (Creates a new process for EACH shellcode)
- ProcessOpen
- AllocMemory (Allocates memory in the EACH remote proces)
- WriteMemory
- ProtectMemory
- ExecuteMemory
Note: The project is designed to allow red team operators to add three shellcodes (fast, medium, and slow) for each C2 channel.
The code is provided "as is" without any warranties or guarantees. It is intended for educational and research purposes only. The usage of this code for any illegal activities is strictly prohibited. The responsibility for any consequences of using this code lies solely with the user.