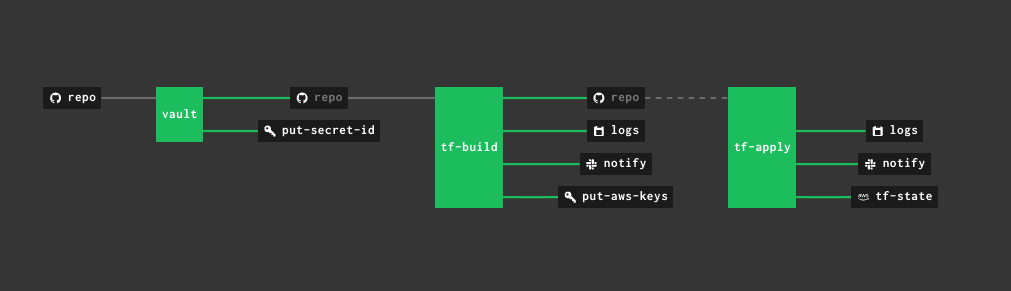
Some resources are fake for the demo :)
- Replacing
tkaburagi/vault-role-idto your image name for each file. - Replacing
tkaburagi:tkaburagito yourusername:passwordindocker-compose.yml. - Replacing
CONCOURSE_WORK_DIRandCONCOURSE_EXTERNAL_URLto your local environemts indocker-compose.yml. - Replcaing
https://github.com/tkaburagi/vault-secure-ci-pipeline.gitto your cloned repo inpipeline.yml.
- Vault AWS Setting
$ vault secrets enable aws
$ vault write aws/config/root \
access_key=*** \
secret_key=*** \
region=ap-northeast-1
$ vault write aws/config/lease lease=10m lease_max=10m
$ vault write aws/roles/tf-handson-role \
credential_type=iam_user \
policy_document=-<<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"rds:*",
"ec2:*",
"elasticloadbalancing:*"
],
"Resource": "*"
}
]
}
EOF- Vault AppRole Setting
$ vault auth enable approle
$ vault write auth/approle/role/aws-read \
policies="aws" \
secret_id_num_uses=1 \
secret_id_ttl="600" \
token_num_uses=3 \
token_ttl="600" \
token_max_ttl="1200"
$ vault read -format=json /auth/approle/role/aws-read/role-id | jq -r '.data.role_id'- Vault ACL Setting
$ vault policy write read-role-id read-role-id.hcl
$ vault policy write kv-concourse kv-concourse.hcl
$ vault policy write pull-secret-id pull-secret-id.hcl
$ vault policy write aws aws.hcl
$ vault policy write revoke-aws revoke-aws.hcl
$ vault token create -policy read-role-id -no-default-policy
$ vault token create -policy kv-concourse -no-default-policy
$ vault token create -policy pull-secret-id -no-default-policy
$ vault token create -policy revoke-aws -no-default-policy-
Replacing
VTOKENandVADDRto your environments inDockerfile. -
Vault EGP Setting (Enterprise Only)
$ vault write sys/policies/egp/validate-cidr-ci-demo \
policy=$(base64 validate-cidr.sentinel) \
enforcement_level="hard-mandatory" \
paths='sys/internal/ui/mounts/kv/aws-keys-concourse','sys/internal/ui/mounts/kv/secret-id-concourse', 'auth/approle/role/aws-read/secret-id'
$ vault read sys/policies/egp/validate-cidr-ci-demo- Concourse Setting
$ docker build -t <<IMAGE_NAME>> .
$ cat << EOF > ci/vars.yml
vault_addr: http://192.168.100.101:8200
vault_kv_token: <<TOKEN-1>>
vault_init_token: <<TOKEN-2>>
vault_revoke_token: <<TOKEN-3>>
EOFThen create the pipeline!
- Start Concourse
$ docker-compose up
$ fly -t localhost login -c http://127.0.0.1
$ fly -t localhost set-pipeline -p snapshots-demo -c ci/pipeline.yml ci/vars.yml
$ fly -t localhost unpause-pipeline --pipeline snapshots-demouse_limit & TTL for each secretACL & Sentinel for KVDockerfileReplace Role-id for the Docker imageRevoke the keyE2E testWebhook