The next generation ansible-managed linux router framework using all the trendy new things
If you dislike systemd. This project is not for you.
Current device target is a nanopi-r5s running Armbian using a WAN port for internet, and then LAN1 and LAN2 aggregated in a Router on a stick pattern for east-west traffic.
This should work on a standard ARM or x86 debian linux system. Currently targeted at bleeding edge debian side.. Bookworm should work fine.
Desire is to have a robust router config with zone firewall leveraging the following underlying components
- netplan
firewalldfoomuuri- dnsmasq
- frrouting
- wireguard
Currently works:
- wan configuration
- bonidng/LACP config
- vlan support
- dhcp zones
- dns
- zone firewall policies
- dynamic dns client setup
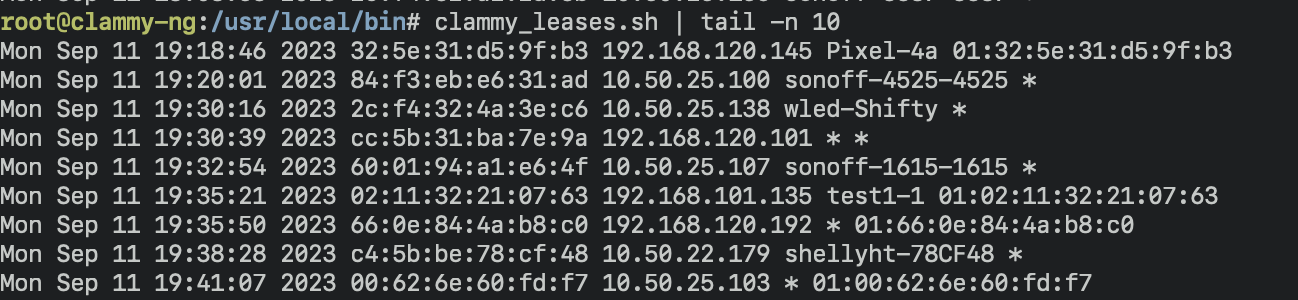
- helper script for leases
- armbian adjustments
- irqbalance
- schedutil governor
- install some helpful tools
- mtr
- bmon
- vnstat
- lnav
- dig
- batcat
- clammy_leases.sh
This repo is meant to be the ansible project directory.. or close to it plus documentation.. Trying to leverage off-the-shelf roles when possible. Other roles will via the clammy collection The roles in the clammy collection need README.md updates, but the defaults/main.yml are very understandable. code should be straight forward
there are better ways, but this way for now... .gitignore has been preconfigured to use namedspace ansible home ~/.clammy-ng-ansible/ and venv used in the example.
assume you have python3 and python3-venv installed
python3 -m venv venv
source venv/bin/activate
python3 -m pip install requirements.txt
ansible-galaxy install -r requirements.yml
ansible-galaxy install -r requirements-clammy-ng.yml
- everything should be ansible role driven
- only roles in calling playbook ex: full.yml
- all config driven by host_vars or group_vars
- try to use modern linux tools
- no large daemons
- friendly tui for looking at state on router
- use things like node_exporter and dnsmasq_exporter for visualizing externally
Naturally there's some sequencing challenges with a router.. especially out of the box. For now full.yml is the POC full sequence of operations.
in reality, this stuff will proably want to be decoupled...
I think there's going to be a generally need to decouple WAN interface-oriented operations from LAN, including firewall management.
approach so far:
- sanitize some armbian stuff such as removing NetworkManager
- sysctl_base config # interface specific stuff might move this
- configure wan interface
- configure lan interfaces
- configure vpn interfaces
- configure wan firewall ingress and port forwards
- configure lan/vpn zones
- configure wan/vpn zone policies
- configure DHCP / DNS (dnsmasq) # what happens if vpn needs DNS to work?
- configure advanced routing (frrouting)
- extra ammenitities
- configure monitoring
Updating firewall demo with ansible / clammy-ng
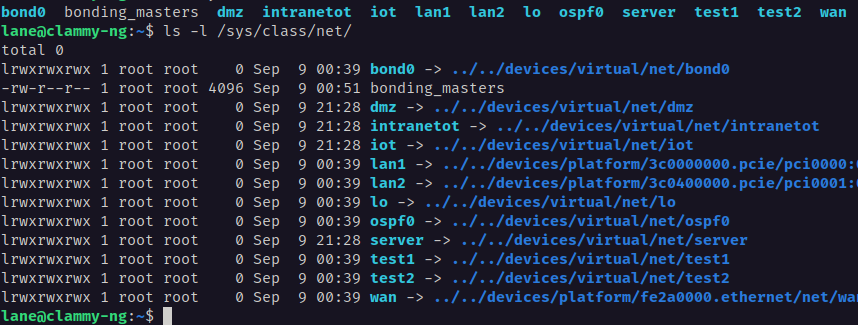
Clean interface names thanks to netplan
Handy Script to view dhcp leases
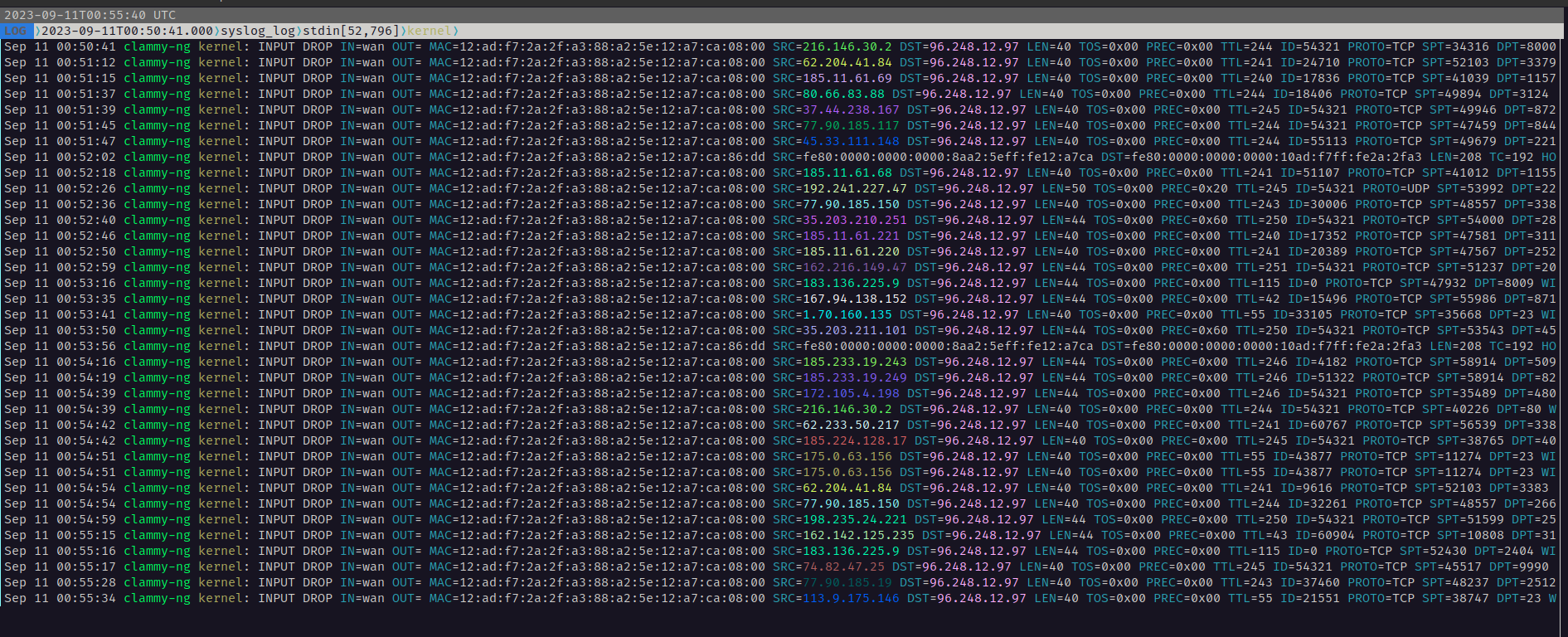
Filter live firewall logs easily with lnav
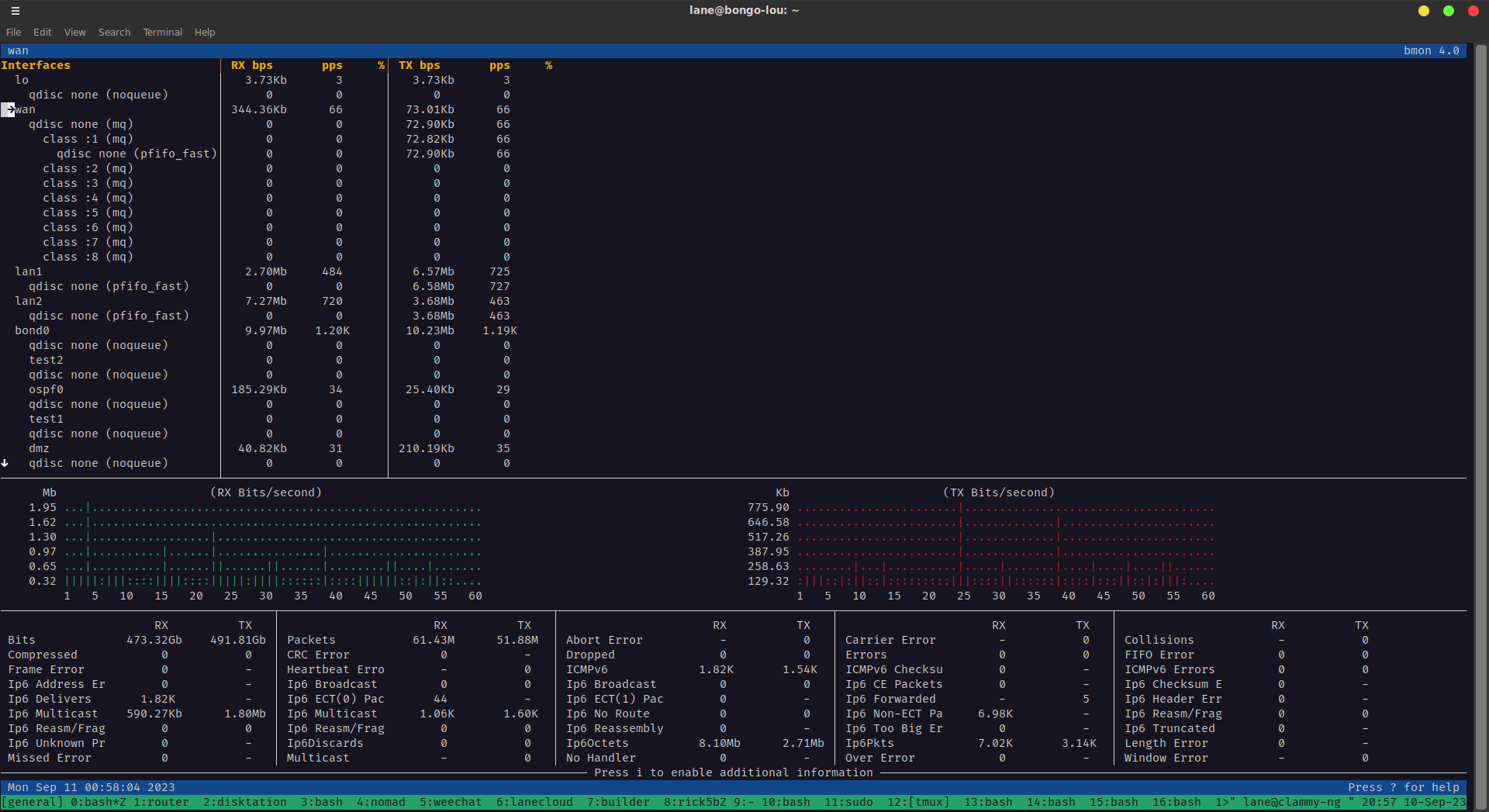
Bandwidth Monitoring with bmon