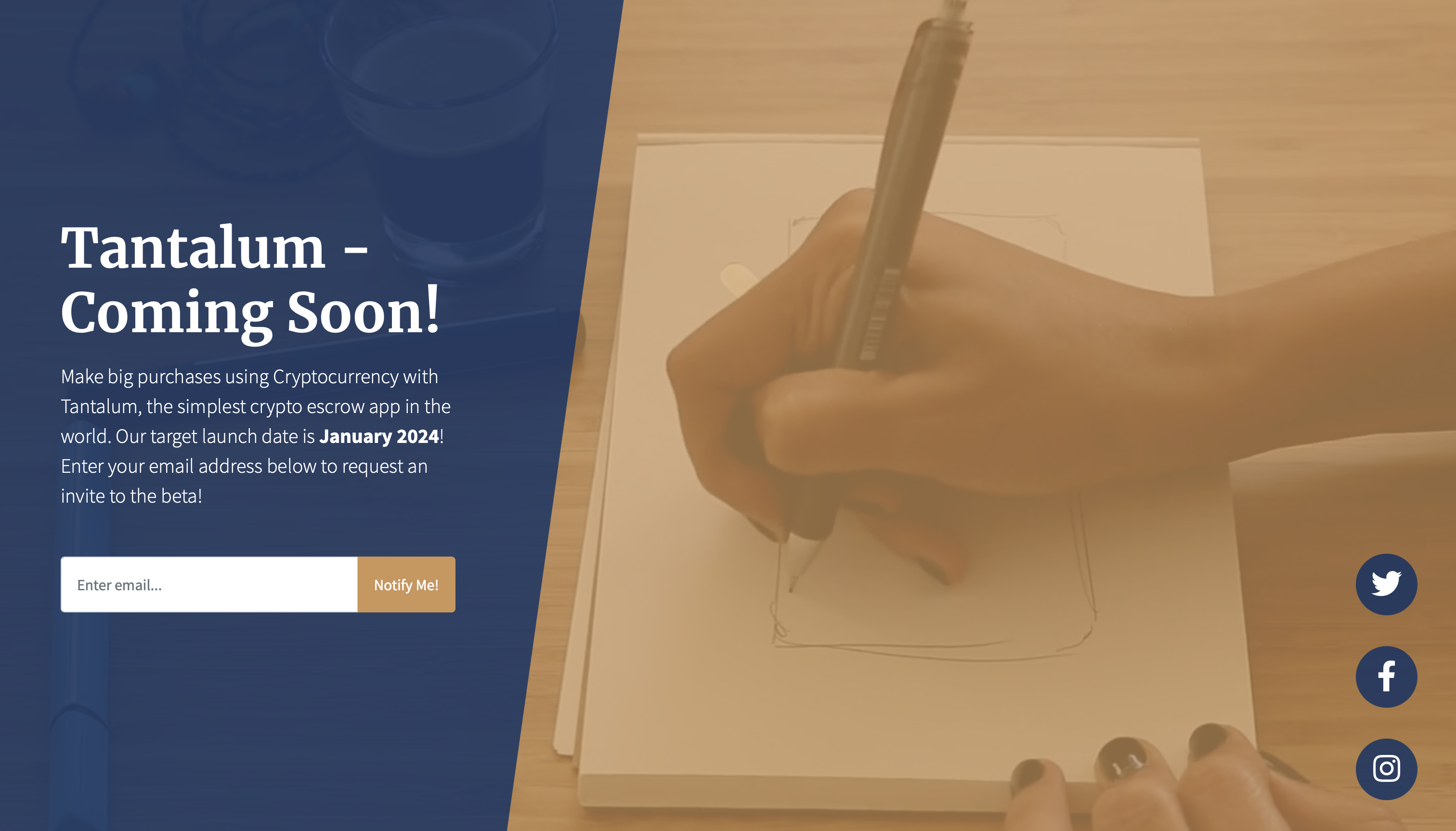
This repository contains a deliberately vulnerable web application exhibiting a HTML injection vulnerability.
Warning
Use these materials sensibly and legally please. Using any of the techniques discussed here against any website when you have not been granted explicit permission (in writing!) to do so is a serious criminal offence that will get you in trouble very quickly.
I use this as part of a practical activity in my seminars on cybersecurity for business students. It allows students to get hands-on in conducting a cyberattack aimed at phishing credentials from the website administrator without leaving the browser.
Caution
Do not deploy this intentionally vulnerable web application on any webserver unless you don't mind destroying it.
Now, configure Apache to separately serve (under different subdomains, for example) the three folders under the root of this project (/attacker-service, /vulnerable-service, and /victim-service). Alternatively, to run the project locally, ensure that PHP 7.0+ is installed and run the following from either of the aforementioned folders:
php -S localhost:8080You'll then be able to access the relevant web application at:
http://localhost:8080
If you want to add this application to your vhosts, config files are included in the /vhosts folder to get you started.
Rename these, update them with your server names/document roots and copy them to /etc/apache2/sites-available. Activate them with a2ensite and run letsencrypt or similar to configure HTTPS automatically.
Follow this workflow to conduct the cyberattack on the web application:
- First, go to the attacker service.
- You should see several files here. Open “monitor.php” in a new tab.
- Now, navigate into the "payloads" folder and copy-paste the contents of "tracker.html.txt" into the email field on the vulnerable service. Hit submit.
- Now, visit the victim service and browse to the "Beta Invite Requests" page. You'll see that "monitor.php" is now showing you the IP address of the victim.
- Next, go back to the attacker service and open "monitorcreds.php" in a new tab.
- Now, navigate into the "payloads" folder and copy-paste the contents of "phishing-one-line.html.txt" into the email field on the vulnerable service. Hit submit.
- Now, visit the victim service again and browse to the "Beta Invite Requests" page. Your phishing payload will execute, showing a form blocking the victim from using the web application and requesting their credentials. You’ll see “monitorcreds.php” change to show you these once they submit them.
In case the audience is more technical, you may want to show how to patch the vulnerabilities in the application.
To do so, perform a project-wide search for TODO to find each code change that needs to be made. Patched code is included as comments.
Apache will need to be reconfigured to disallow the download of the /emails.txt user database. Do this my renaming .htaccess.patch (under /vulnerable-service) to .htaccess. Ensure that your Apache installation allows .htaccess overrides in the web root directory.
The following libraries are used by the project frontend, but are committed to the repository (i.e. not dependency-managed) for ease of deploying the project and resetting it for the next group of students:
- jQuery v3.5.1
- jQuery UI Easing v1.4.1
- Bootstrap v4.5.0
- FontAwesome v5.13.0
- Chart.js v2.9.3
- DataTables v1.10.21
Fonts used include:
The frontends for this project are based on:
Copyright 2023 Saul Johnson. Code released under the MIT license.