Malice's mission is to be a free open source version of VirusTotal that anyone can use at any scale from an independent researcher to a fortune 500 company.
Install Docker for Mac
-Or-
Install with homebrew.
$ brew install caskroom/cask/brew-cask
$ brew cask install virtualbox
$ brew install docker
$ brew install docker-machine
$ docker-machine create --driver virtualbox --engine-storage-driver overlay malice
$ eval $(docker-machine env malice)$ brew install https://raw.githubusercontent.com/maliceio/malice/master/contrib/homebrew/Formula/malice.rbUsage: malice [OPTIONS] COMMAND [arg...]
Open Source Malware Analysis Framework
Version: 0.1.0-alpha, build HEAD
Author:
blacktop - <https://github.com/blacktop>
Options:
--debug, -D Enable debug mode [$MALICE_DEBUG]
--help, -h show help
--version, -v print the version
Commands:
scan Scan a file
watch Watch a folder
lookup Look up a file hash
elk Start an ELK docker container
web Start, Stop Web services
plugin List, Install or Remove Plugins
help Shows a list of commands or help for one command
Run 'malice COMMAND --help' for more information on a command.
$ malice scan evil.malwareNOTE: On the first run malice will download all of it's default plugins which can take a while to complete.
Malice will output the results as a markdown table that can be piped or copied into a results.md that will look great on Github see here
Once the scan completes you can open the Kibana UI and look at the scan results here: http://localhost (assuming you are using Docker for Mac)
-
You will be prompted for a user/pass which defaults to:
- user:
admin - password:
admin
- user:
-
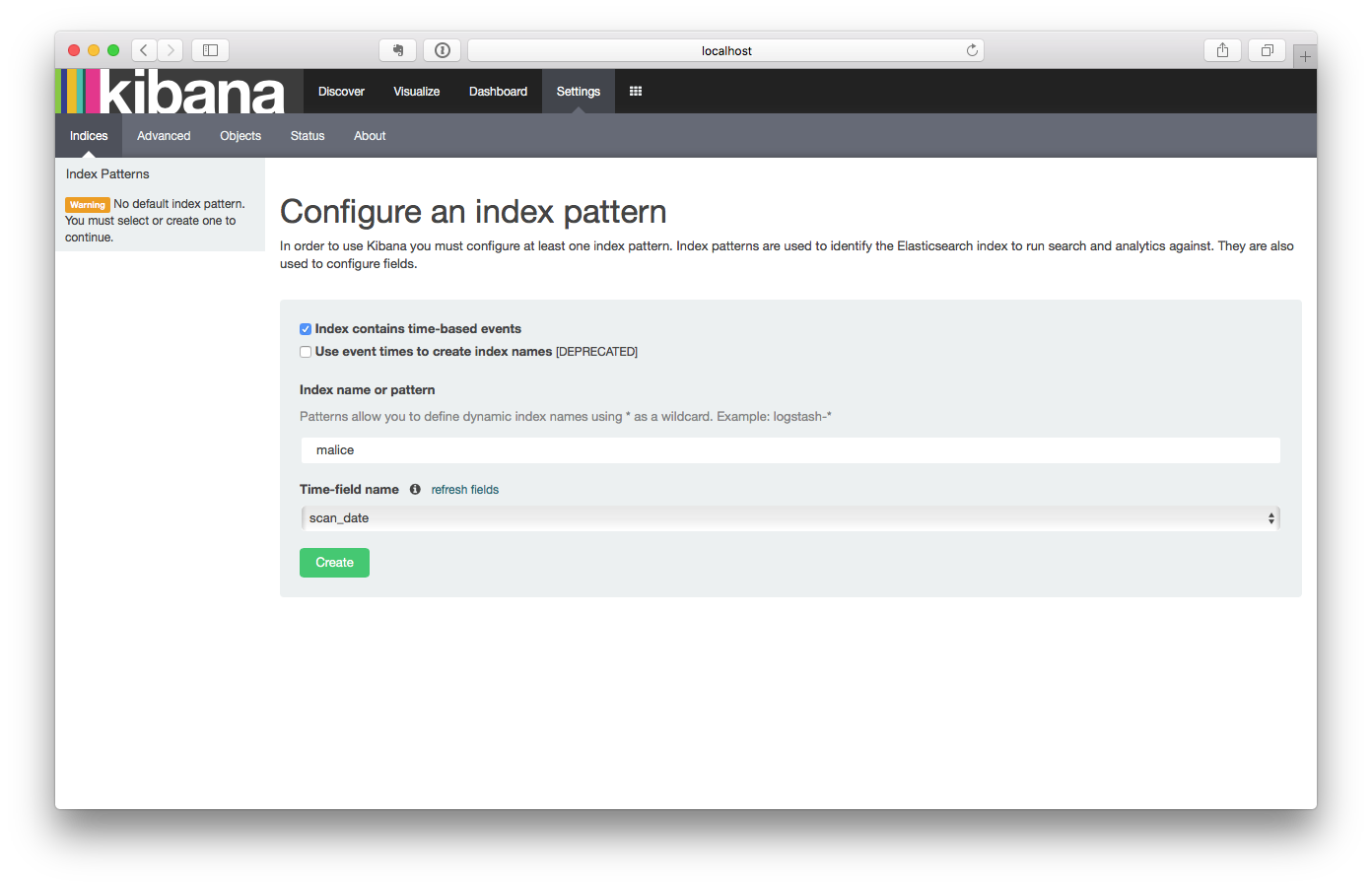
Type in malice as the
Index name or patternand click Create. -
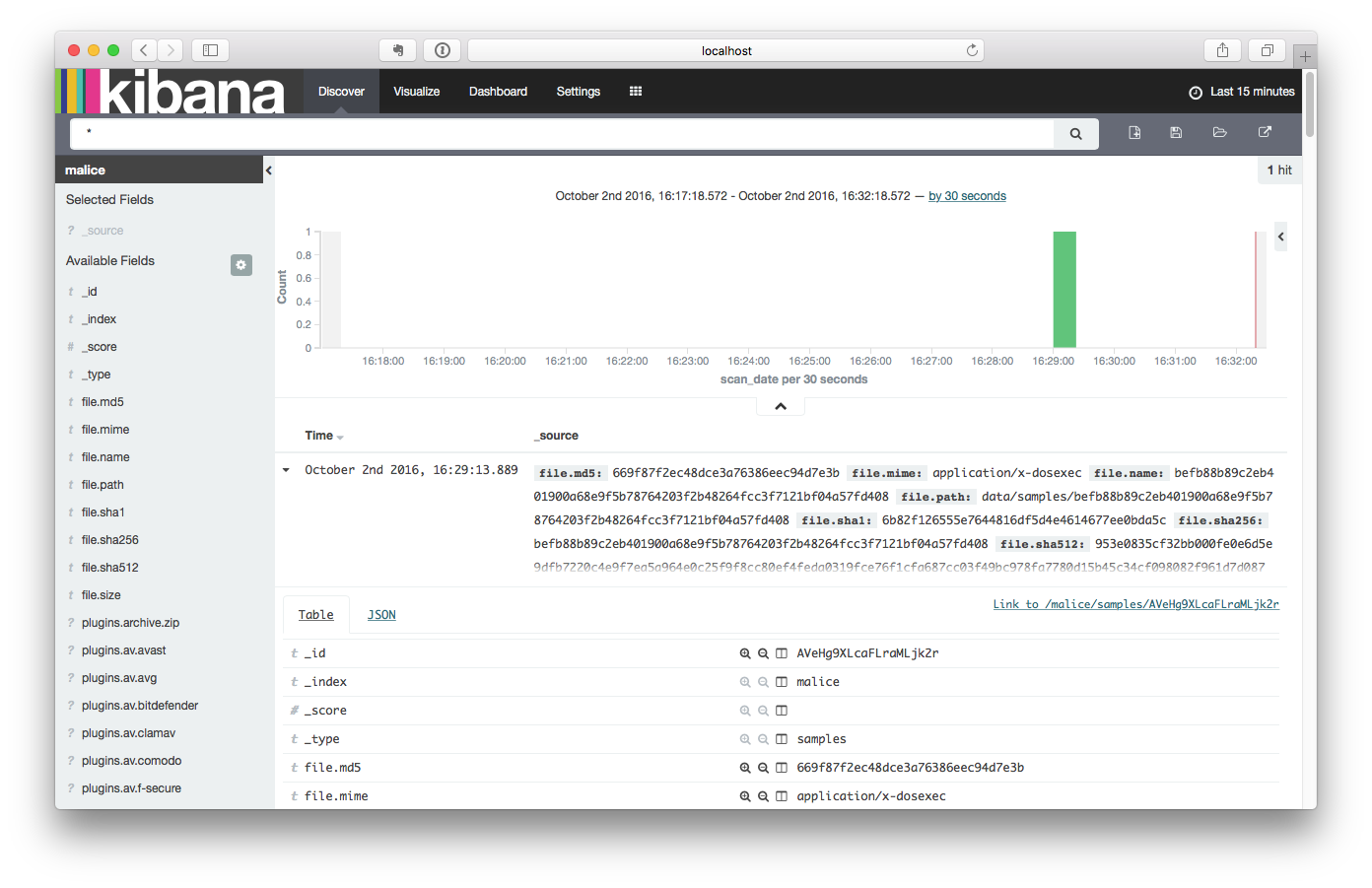
Now click on the
Discover Taband behold!!!


docker run --rm -v /var/run/docker.sock:/var/run/docker.sock malice/engine plugin update --alldocker run --rm -v /var/run/docker.sock:/var/run/docker.sock \
-v `pwd`:/malice/samples \
-e MALICE_VT_API=$MALICE_VT_API \
malice/engine scan SAMPLEAdd the following to your bash or zsh profile
$ alias malice='docker run --rm -v /var/run/docker.sock:/var/run/docker.sock \
-v `pwd`:/malice/samples \
-e MALICE_VT_API=$MALICE_VT_API \
malice/engine $@'See CHANGELOG.md
Apache License (Version 2.0)
Copyright (c) 2013 - 2016 blacktop Joshua Maine