An hash-based obserbation tool of VirusTotal
# Setting VT API Key
$ cp .env.example .env
# Add your API Key on .env file
$ docker build -t vttotal:latest .
$ docker run -p {your_port}:8000 vttotal:latest
# access localhost:{your_port} :-)- requires python3, pipenv and SQLite>=3.8.3
- Recommend to use pyenv
# Install dependencies
$ pipenv sync
# Setting VT API Key
$ cp .env.example .env
# Add your API Key on .env file
# launch server
$ pipenv shell
# Create cron jobs
(VTTotal)$ python manage.py crontab add
(VTTotal)$ python manage.py migrate
(VTTotal)$ python manage.py runserver 0.0.0.0:8000
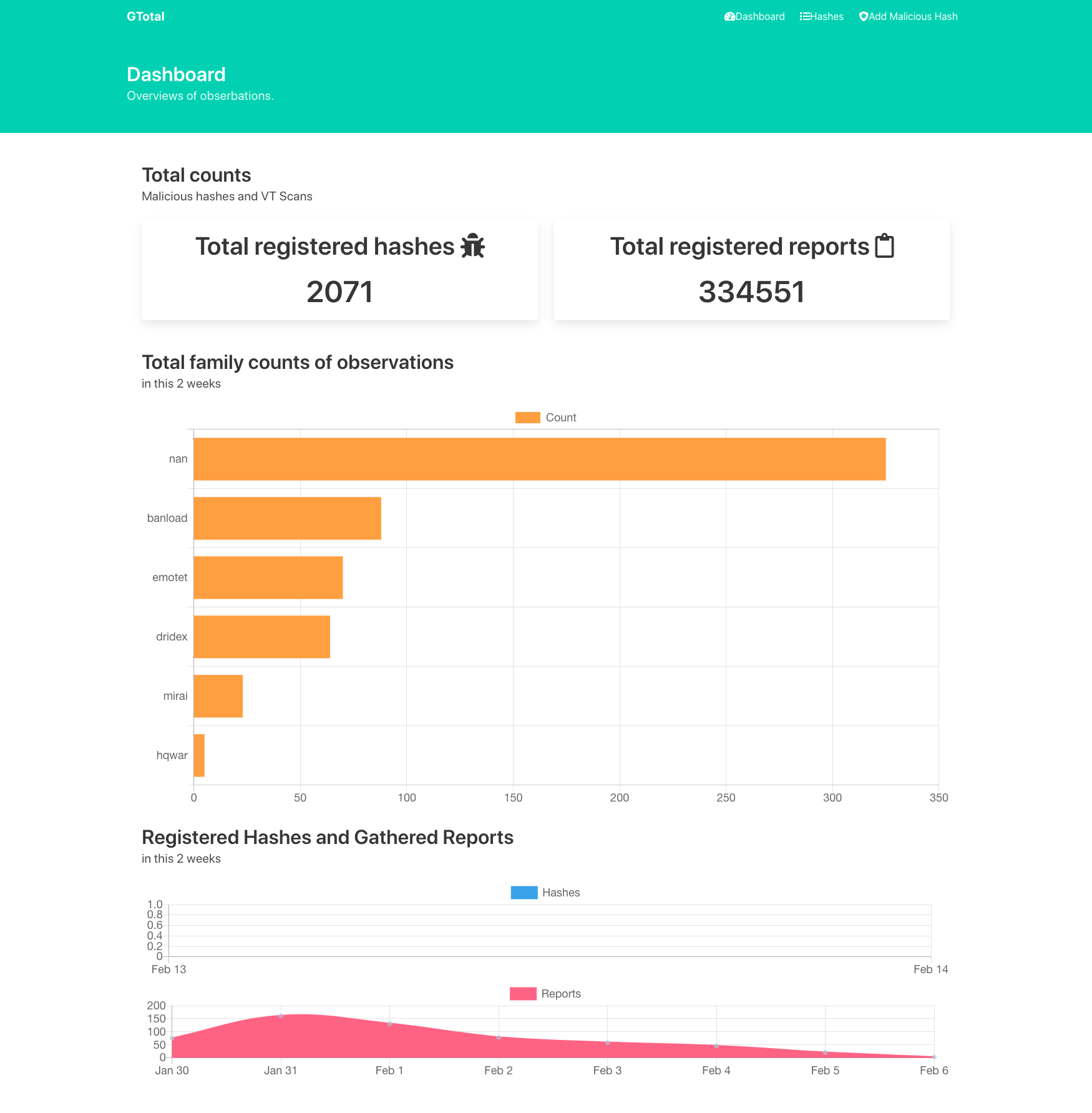
# access localhost:8000 :-)- Register malicious hash.
- Automatic rescan and gather reports on VirusTotal.
- Recommend to use Enterprise API key due to request rate limit.
- Gather information and automatic tagging via AVClass2.
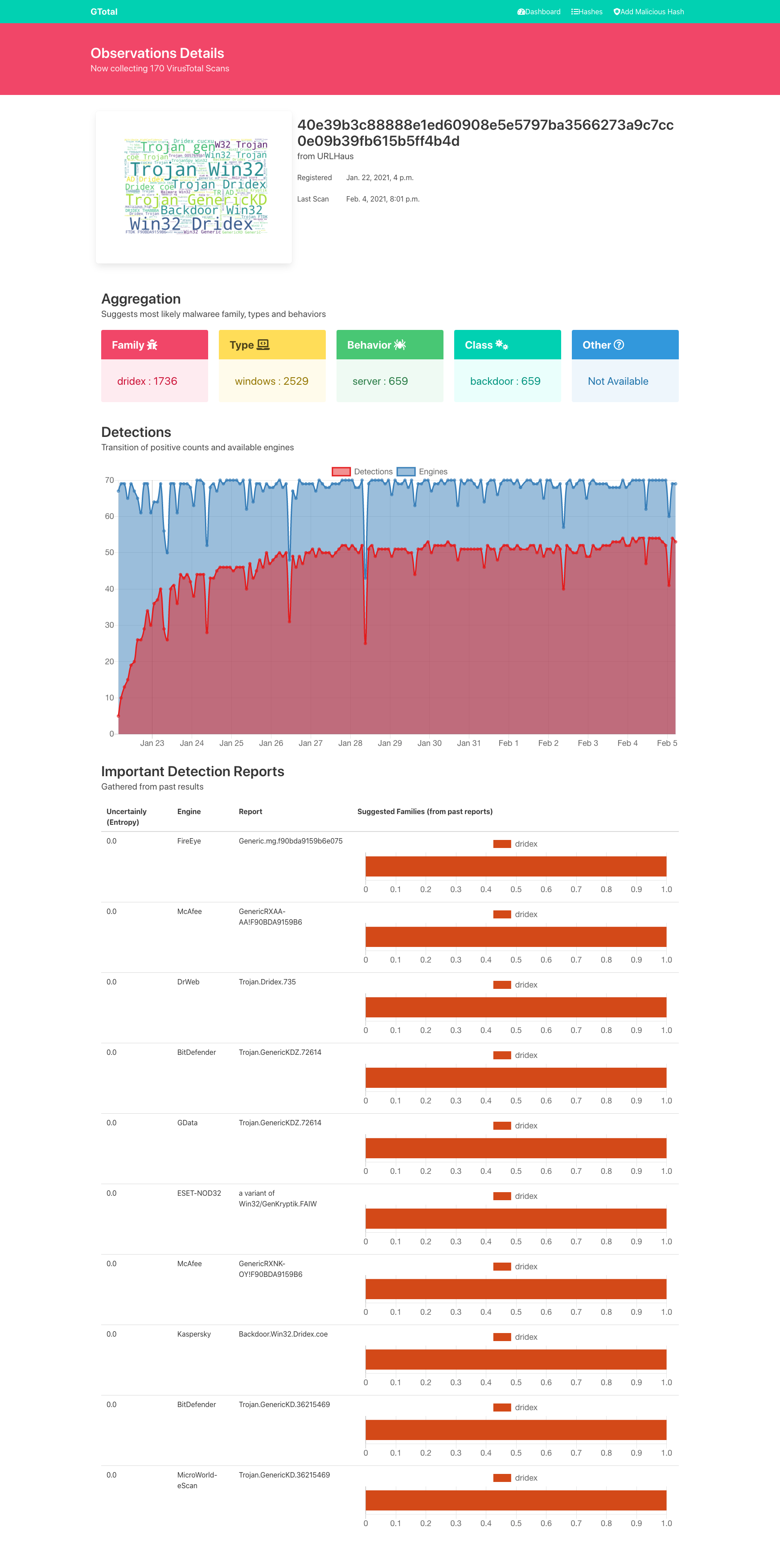
- Show dynamics of detections by av-vendors and available engines.
- Entropy based suggestions of raw detection reports calculated from past family tagging.
- REST API for batch observation & malware labelling
- VirusTotal is an online malware detection tool which include about 70 antivirus engines.
- But current research shows that VirusTotal detection will "flips" over time.
- And if new malware has been detected, We should trigger rescan on several occasions.
- Ofcourse AV-vendors have no common rules to naming malware families, types and so on.
- We define 2 types of ambiguousness of VirusTotal reports.
- Detection Count (Eg: 10/70, 1/70/, 15/30, ...)
- Reports by AV-vendors (Eg: Trojan:Generic, Malware Ai Score=85,...)
- Our tool features keep you from these ambiguousness.
-
Zhu, S., Shi, J., Yang, L., Qin, B., Zhang, Z., Song, L., & Wang, G. (2020). Measuring and modeling the label dynamics of online anti-malware engines. In Proceedings of the 29th USENIX Security Symposium (pp. 2361-2378). (Proceedings of the 29th USE NIX Security Symposium). USENIX Association.
-
Silvia Sebastián, Juan Caballero. AVClass2: Massive Malware Tag Extraction from AV Labels. In proceedings of the Annual Computer Security Applications Conference, December 2020.
This repository contains another repository which licensed by MIT LICENSE. So, this repository is too.
This software is one of deliverables of SecHack365 program by NICT. Thanks for trainers and trainees of SecHack365 2020.