A Terraform script to host a Web Key Directory (WKD). It serves an OpenPGP public key at https://openpgpkey.<domain.name> using the WKD Advanced Setup.
An Amazon S3 bucket stores the key and Amazon CloudFront is the Content Delivery Network (CDN). Amazon S3 CORS configuration allows Keyoxide access to the public key.
Demo: keyoxide.org/wkd/karthic%40maverickgeek.xyz
- GitHub: github.com/k3karthic/terraform__wkd
- Codeberg: codeberg.org/k3karthic/terraform__wkd
Step 1: Create a file to store the Terraform input variables. Use wkd.tfvars.sample as a reference. Keep wkd.tfvars as the filename or change the name in the following files,
.gitignorebin/plan.shbin/encrypt.shbin/decrypt.sh
Step 2: Set domain to your root domain name (e.g, maverickgeek.xyz).
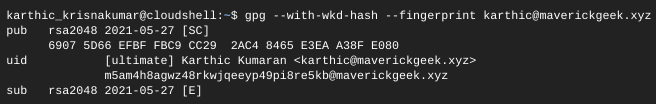
Step 3: Get the WKD hash for your public key using the following GPG command and save it as key_hash. The hash is below the uid as <hash>@<domain>.
$ gpg --with-wkd-hash --fingerprint <email address>
Step 4: Update the following in bin/update_key.sh,
- Replace
A38FE080with your public key ID - Replace
m5am4h8agwz48rkwjqeeyp49pi8re5kbwith your WKD hash
Step 5: Export your public key into the keys folder using the script bin/update_key.sh.
$ ./bin/update_key.sh
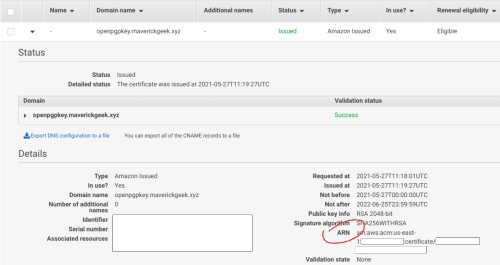
Step 5: Fetch a certificate from AWS Certificate Manager in US East (N. Virginia) for your domain. Save the ARN in acm_arn.
AWS provider documentation is at registry.terraform.io/providers/hashicorp/aws/latest/docs.
AWS CloudShell can deploy this script without configuration.
Step 1: Use the following command to create a Terraform plan,
$ ./bin/plan.sh
To avoid fetching the latest state of resources, use the following command,
$ ./bin/plan.sh -refresh=false
Step 2: Review the plan using the following command,
$ ./bin/view.sh
Step 3: Apply the plan using the following command,
$ ./bin/apply.sh
Encrypt sensitive files (Terraform input variables and state) before saving them. .gitignore must contain the unencrypted file paths.
Use the following command to decrypt the files after cloning the repository,
$ ./bin/decrypt.sh
Use the following command after running bin/apply.sh to encrypt the updated state files,
$ ./bin/encrypt.sh <gpg key id>