A Terraform script to deploy an instance in Google Cloud running under the Always Free tier.
A custom VPC allows for more control over network security. The Terraform script below creates a custom VPC,
- terraform__gcloud-vpc
The following Ansible playbook covers basic setup for FreeBSD (e.g, swap, fail2ban),
- ansible__freebsd-basic
Use a Njalla hostname for the instance using the Ansible playbook below,
- ansible__gcloud-njalla-dns
- GitHub: github.com/k3karthic/terraform__gcloud-instance
- Codeberg: codeberg.org/k3karthic/terraform__gcloud-instance
- Create a file to store the Terraform input variables. Use
uscentral.tfvars.sampleas a reference. Keepuscentral.tfvarsas the filename or change the name in the following files,.gitignorebin/plan.sh
- Create a custom VPC and update the subnet name in
subnetwork. To skip creating a VPC, usedefaultas the value. - Change
nameif you would like to change the name of the instance. - Set
projectto the name of your Google Cloud Project. - Set
zoneto an available zone in the same region assubnetwork. List of zones by region are at cloud.google.com/compute/docs/regions-zones/#available. - Create a hostname in Njalla and update the same in
njalla_domainandnjalla_domain_id.
Note: Image ID can be found in the release announcement from the FreeBSD website at https://www.freebsd.org/releases/.
Google provider documentation is at registry.terraform.io/providers/hashicorp/google/latest/docs.
Google Cloud Shell can deploy this script without configuration.
Step 1: Use the following command to create a Terraform plan,
$ ./bin/plan.sh
To avoid fetching the latest state of resources, use the following command,
$ ./bin/plan.sh -refresh=false
Step 2: Review the plan using the following command,
$ ./bin/view.sh
Step 3: Apply the plan using the following command,
$ ./bin/apply.sh
Step 4: Display the created instance using the following command,
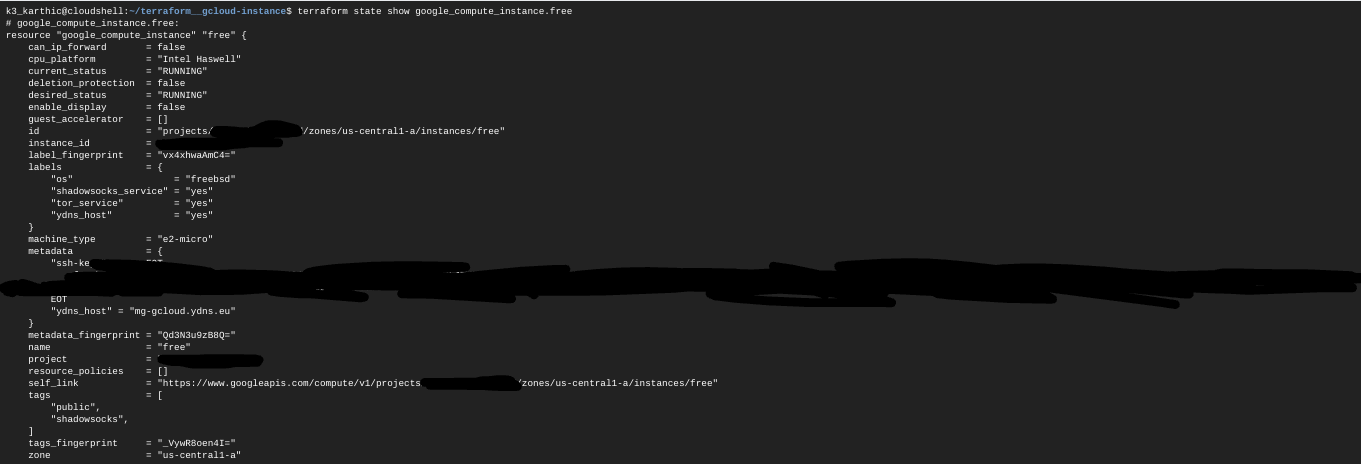
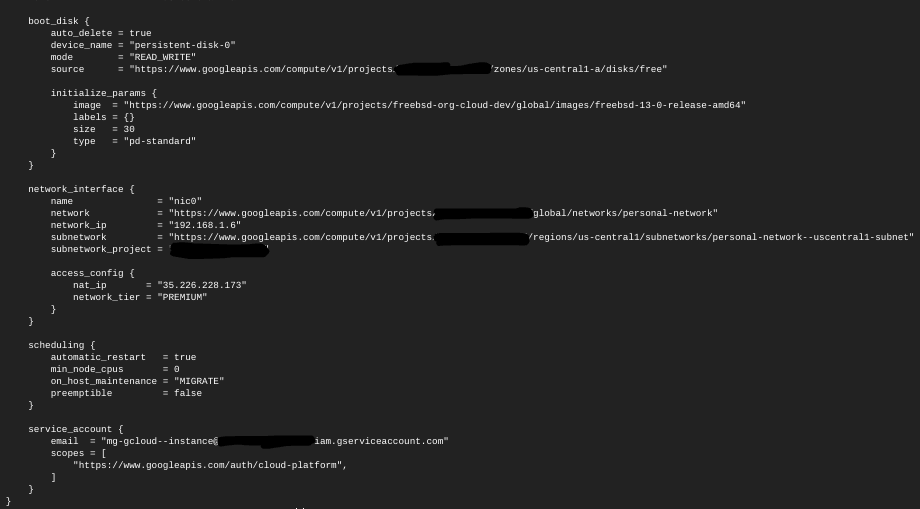
$ terraform show google_compute_instance.free
Encrypt sensitive files (Terraform input variables, SSH public key and state) before saving them. .gitignore must contain the unencrypted file paths.
Use the following command to decrypt the files after cloning the repository,
$ ./bin/decrypt.sh
Use the following command after running bin/apply.sh to encrypt the updated state files,
$ ./bin/encrypt.sh <gpg key id>