Very simple implementation of Azure AD Device Code Flow using existing high privileged application (Azure CLI)
- You can define your own application too
- Open Azure Cloud Shell (BASH) and paste following command to it:
curl -o- "https://raw.githubusercontent.com/jsa2/aad_device_code/main/init.sh" | bash
- Navigate to install directory
cd aad_device_code/ - Type
npm install - Run the tool (It will wait for 15 iterations for login)
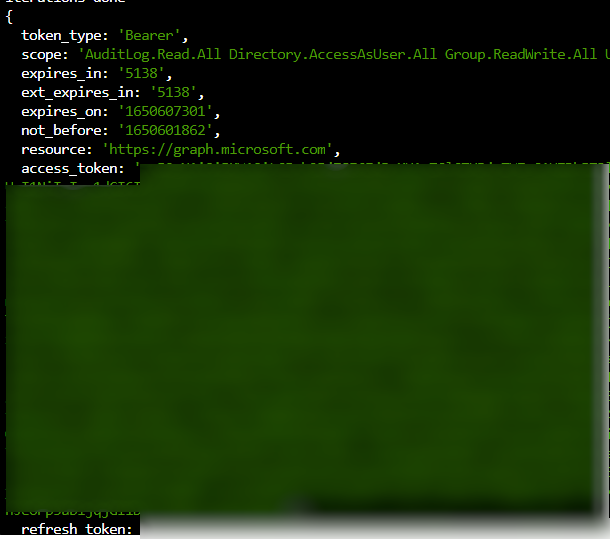
node getCode.js --client=04b07795-8ddb-461a-bbee-02f9e1bf7b46 --resource=https://graph.microsoft.com
-
If you use your own clientID, and it is not an multitenant app, supply tenantId param too
node getCode.js --tid=48f55450-183a-45d6-a9ce-68f3cbc68947 --client=b5505019-43a5-4eda-bc5e-b0157a1227b9 --resource=https://graph.microsoft.com
If you want to read about how this might be used for malicious purposes, read the excellent write-up by DrAzureAD @ https://o365blog.com/post/phishing/