New VNET + OPNsense with two NICs (Untrusted/Trusted)
Existing VNET + OPNsense with two NICs (Untrusted/Trusted)
New VNET + OPNsense with single NIC
Existing VNET + OPNsense with single NIC
Those template allows you to deploy an OPNsense Firewall VM using the opnsense-bootsrtap installation method. It creates an FreeBSD VM, does a silent install of OPNsense using a modified version of opnsense-bootstrap.sh with the settings provided.
The login credentials are set during the installation process to:
- Username: root
- Password: opnsense (lowercase)
*** Please *** Change default password!!!
After deployment, you can go to https://PublicIP, then input the user and password, to configure the OPNsense firewall.
- Added all templates on main page for new VNET and existing VNETs for both two NICs and single NIC.
- Added options to specific your own deployment script and configuration file.
- Added NSG to support Standard SKU Public and Internal Load Balancer.
This OPNsense solution is installed in FreeBSD 11.2 (Azure Image). Here is what you will see when you deploy this Template:
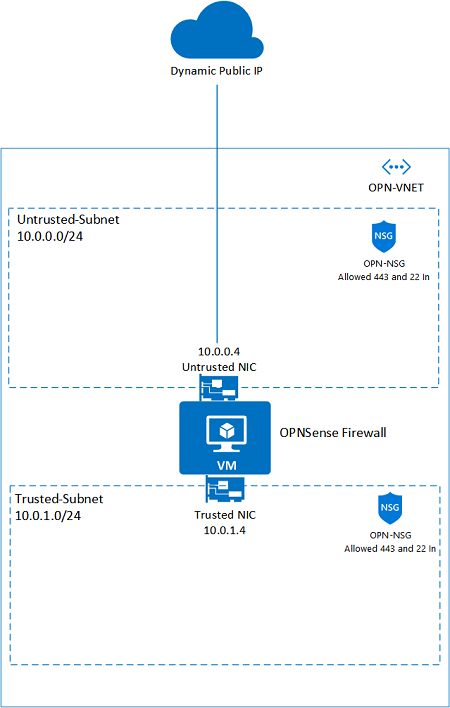
- VNET with Two Subnets and OPNsense VM with two NICs.
- VNET Address space is: 10.0.0.0/16 (suggested Address space, you may change that).
- External NIC named Untrusted Linked to Untrusted-Subnet (10.0.0.0/24).
- Internal NIC named Trusted Linked to Trusted-Subnet (10.0.1.0/24).
- It creates a NSG named OPN-NSG which allows incoming SSH and HTTPS. Same NSG is associated to both Subnets.
Here is a visual representation of this design of the two NIC deployment:
Here are few considerations to deploy this solution correctly:
- When you deploy this template, it will leave only TCP 22 listening to Internet while OPNsense gets installed.
- To monitor the installation process during template deployment you can just probe the port 22 on OPNsense VM public IP (psping or tcping).
- When port is down which means OPNsense is installed and VM will get restarted automatically. At this point you will have only TCP 443.
Note: It takes about 10 min to complete the whole process when VM is created and a new VM CustomScript is started to install OPNsense.
- First access can be done using HTTPS://PublicIP. Please ignore SSL/TLS errors and proceed.
- Your first login is going to be username "root" and password "opnsense" (PLEASE change your password right the way).
- To access SSH you can either deploy a Jumpbox VM on Trusted Subnet or create a Firewall Rule to allow SSH to Internet.
- To send traffic to OPNsense you need to create UDR 0.0.0.0 and set IP of trusted NIC IP (10.0.1.4) as next hop. Associate that NVA to Trusted-Subnet.
- Note: It is necessary to create appropriate Firewall rules inside OPNsense to desired traffic to work properly.
The following improvements will be added soon:
- Add option to create Jumpbox VM for management
Please use Github issues tab to provide feedback.
Thanks for direct feedbacks and contributions from: Adam Torkar, Brian Wurzbacher, Victor Santana and Brady Sondreal.