CMS Link: https://www.hoteldruid.com/
Version Affected: 3.0.4
Severity & CVSS: 5.4 (Medium) | Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N
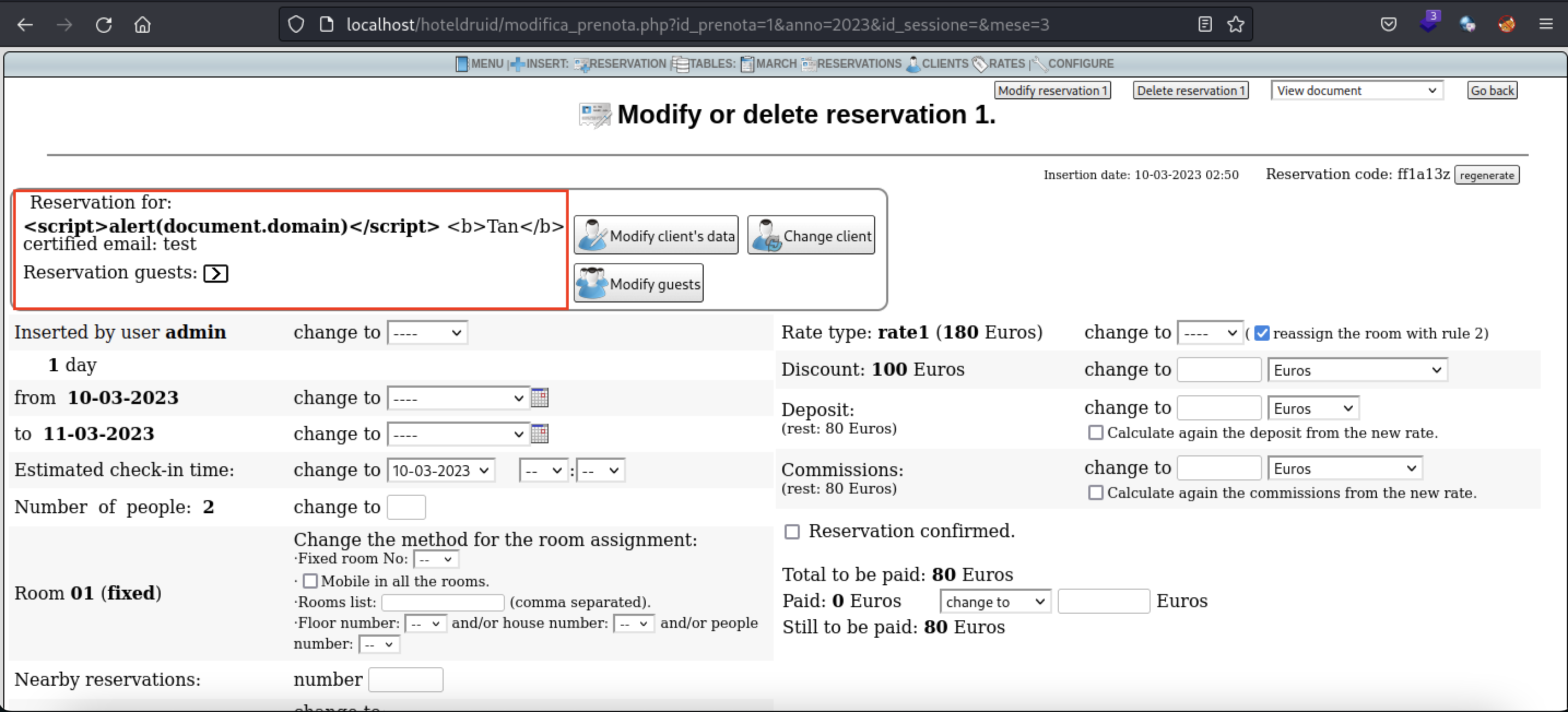
A Stored Cross Site Scripting (XSS) vulnerability exists in multiple pages in Version 3.0.4 of the Hotel Druid application that allows for arbitrary execution of commands.
Vulnerable Fields: Surname, Name, Nickname in the "Document" function
Affected Links: /visualizza_contratto.php
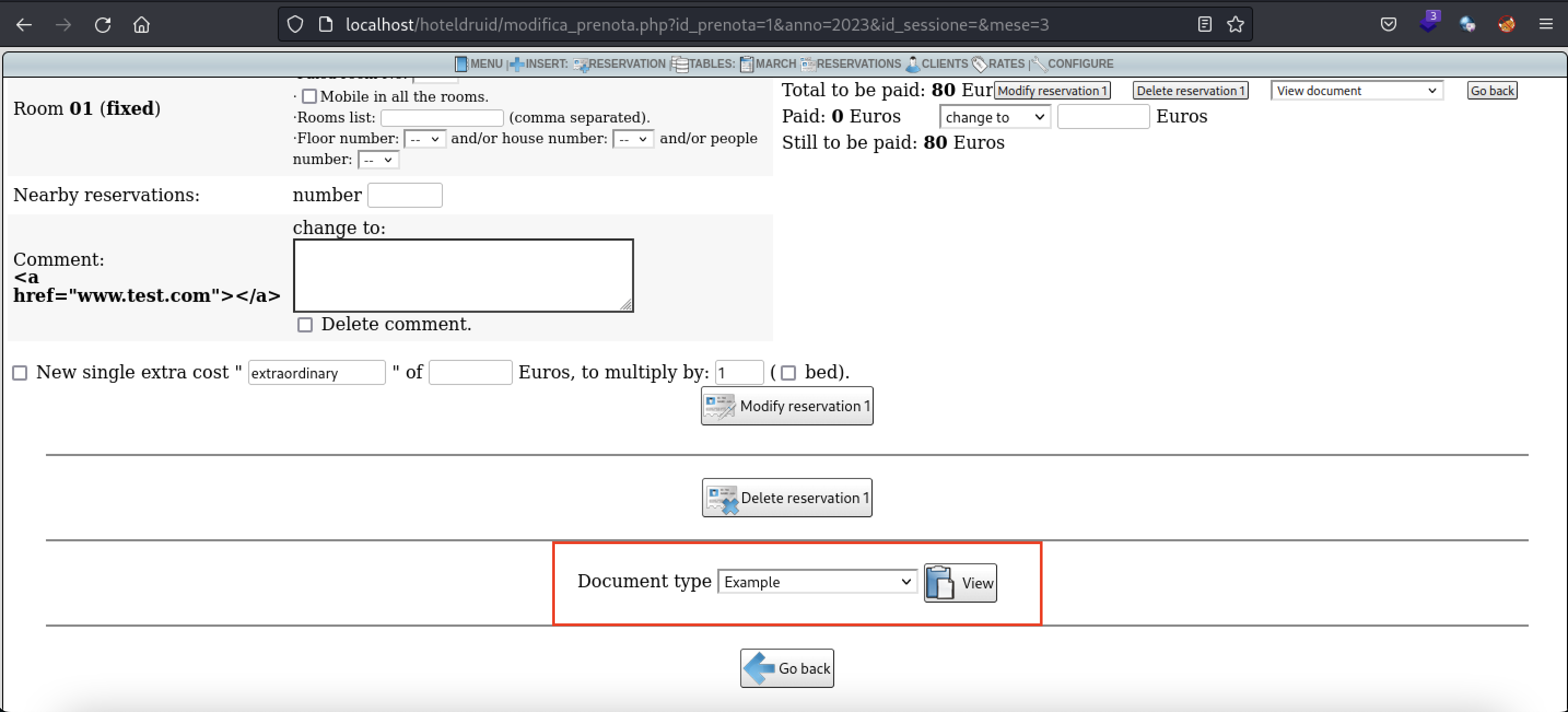
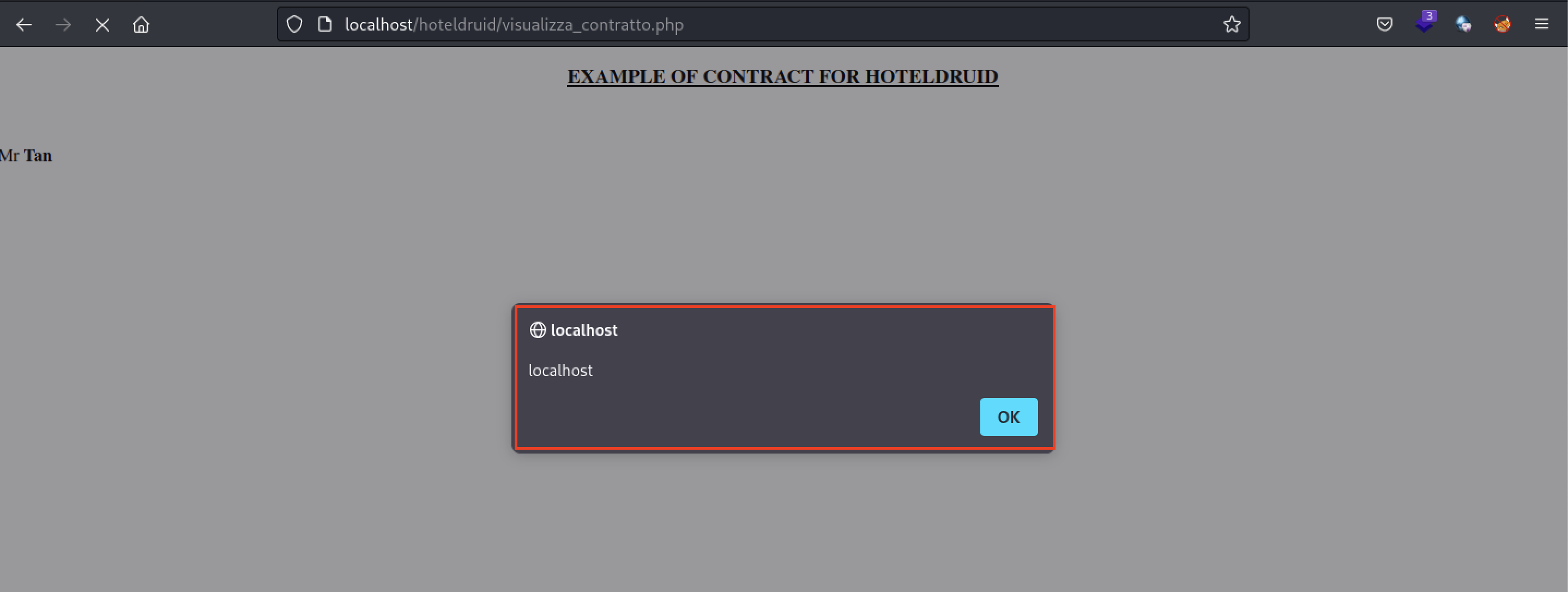
Triggering the payload: Visit the Example document preview function
Remediation: Update to HotelDruid version 3.0.5
Steps to Reproduce:
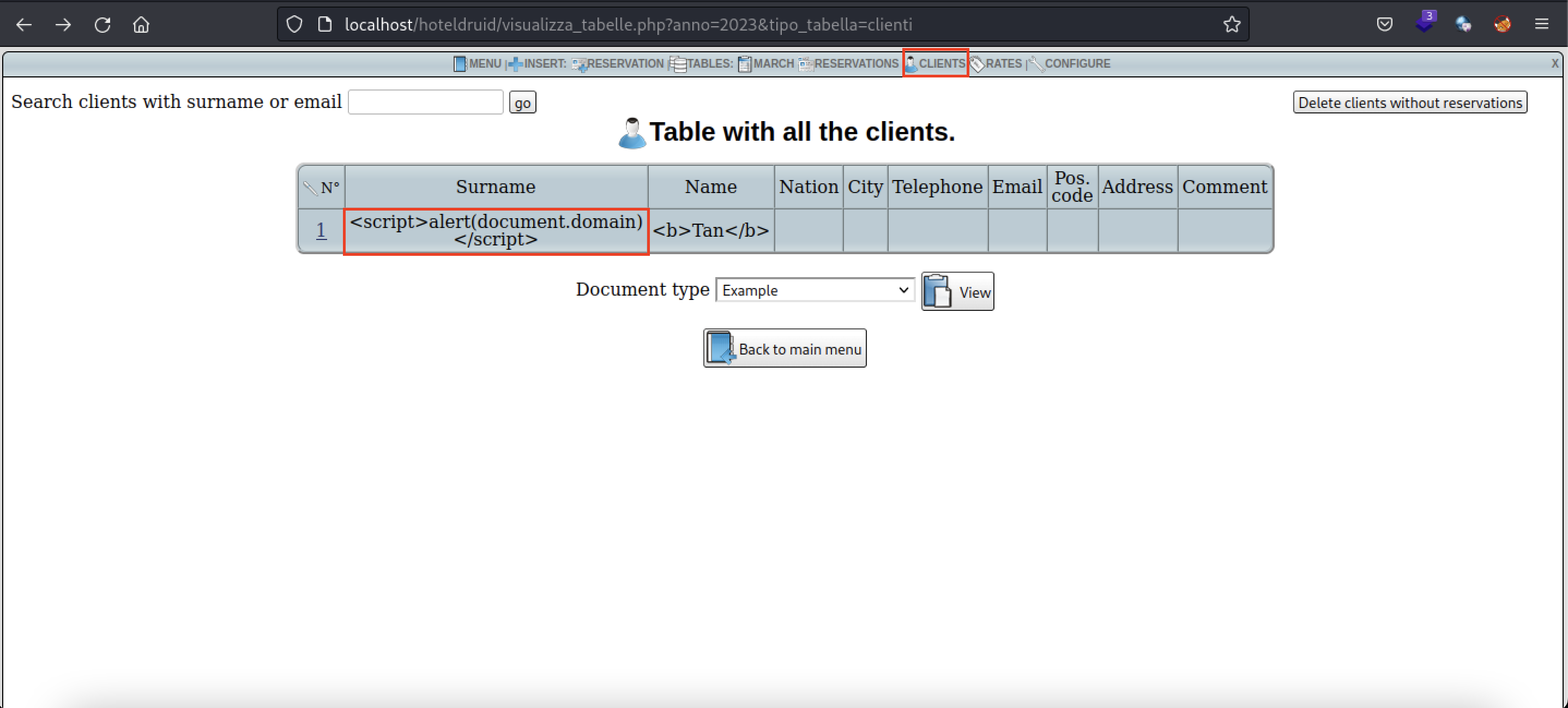
- Enter a XSS payload into a client's name. This can be done during room reservation or a brand new registration of a client. The payload used is
<script>alert(document.domain)</script>
- Navigate to "Clients" tab and select the client with the XSS payload by clicking on the "N" column
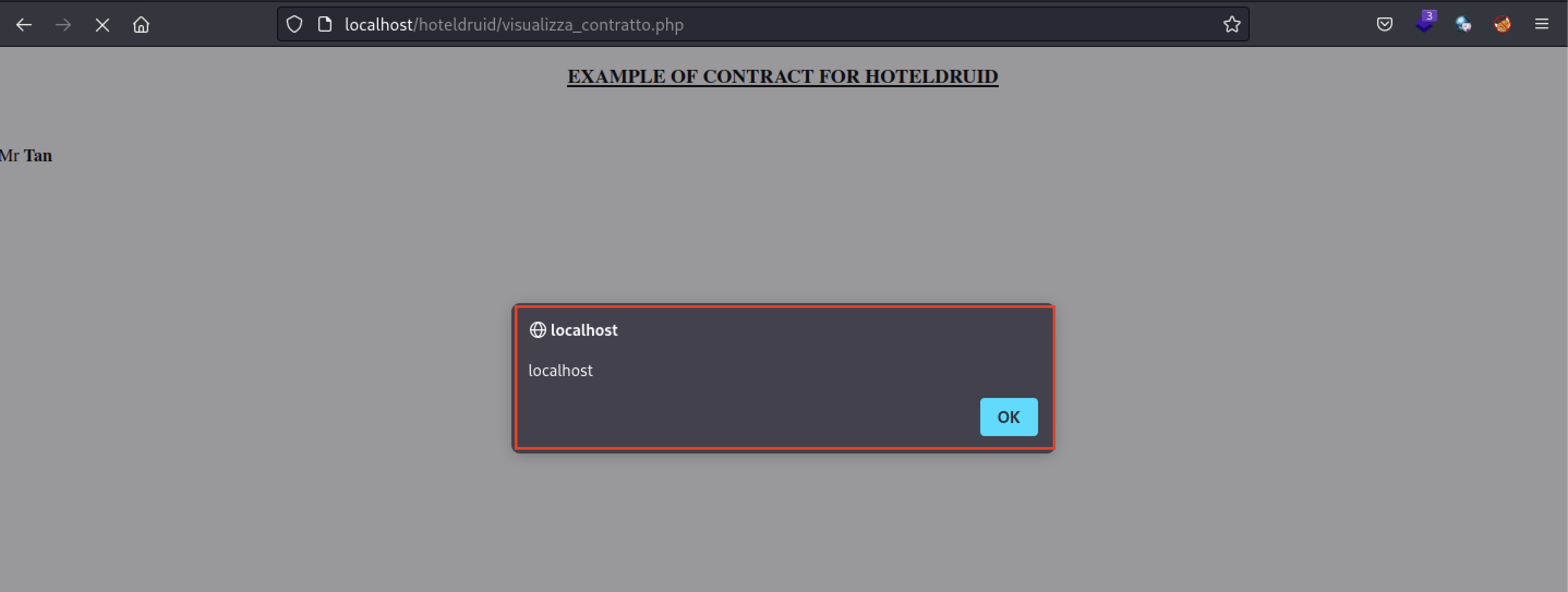
- In this page, there are 2 ways to trigger the stored XSS payload. The first is by viewing the Example document in the top right hand corner of the page
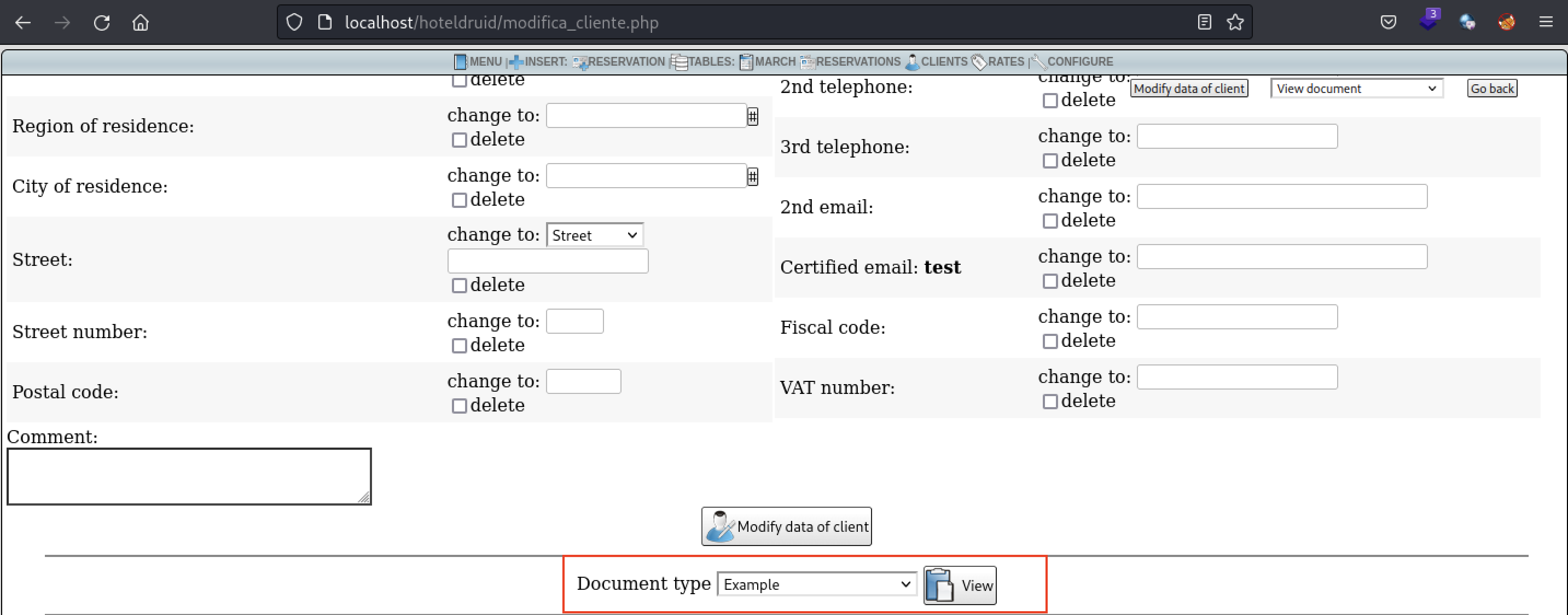
- The second way to trigger the XSS payload is to navigate to the bottom of the page where you can modify the client's data
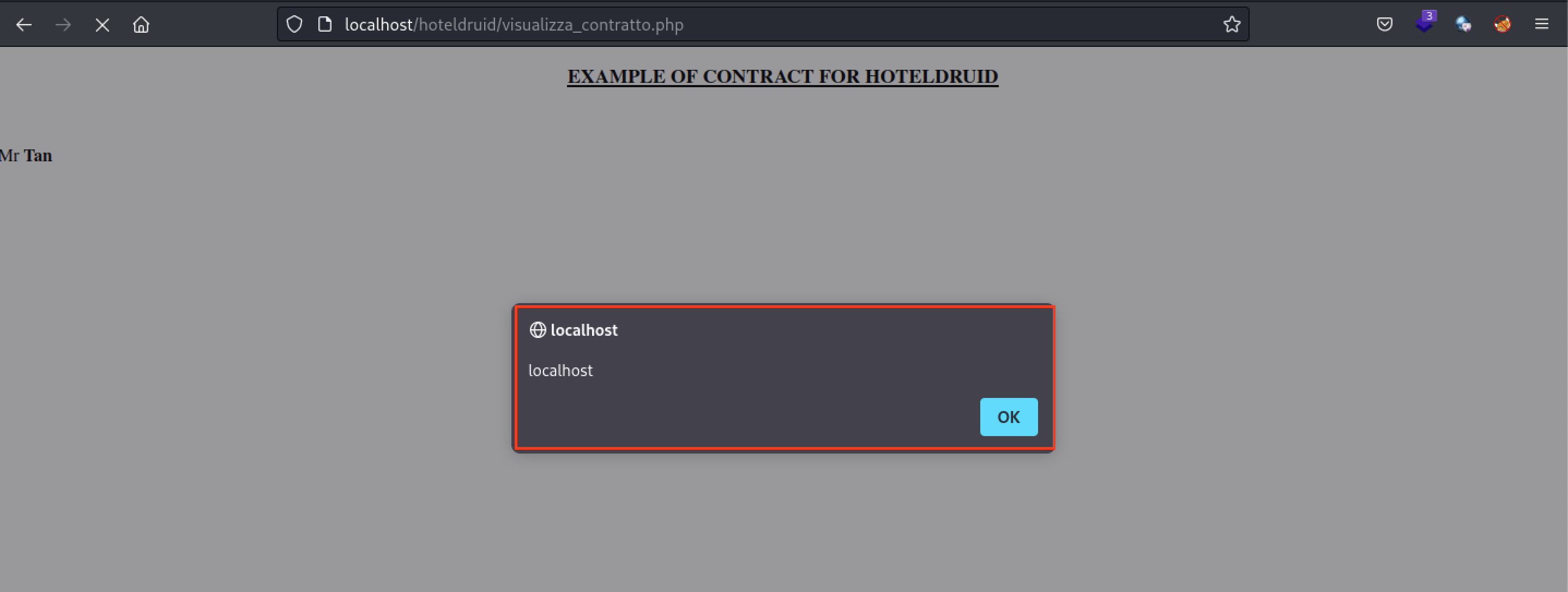
- Once again, select the Example document and click on "View"
- There are also other methods to trigger the XSS payload. By navigating to "Reservations" and modifying the client's reservation
- Scroll to the bottom of the page and once again select the Example document and click on "View"