19 Customizable honeypots for monitoring network traffic, bots activities, and username\password credentials (DNS, HTTP Proxy, HTTP, HTTPS, SSH, POP3, IMAP, STMP, RDP, VNC, SMB, SOCKS5, Redis, TELNET, Postgres, MySQL, MSSQL, Elastic and ldap)
If you want to implement the honeypots in your project, check QeeqBox honeypots
Chameleon is considered very effective. This is an active defense tool. The system simulates open, unprotected ports and takes on attempts to find vulnerabilities - by Dean Chester, Chief Editor of cooltechzone
Pon un Honeypot en tu vida by Héctor Herrero, bujarra
- Modular approach (honeypots run as scripts or imported as objects)
- Most honeypots serve as servers (Only a few that emulate the application layer protocols)
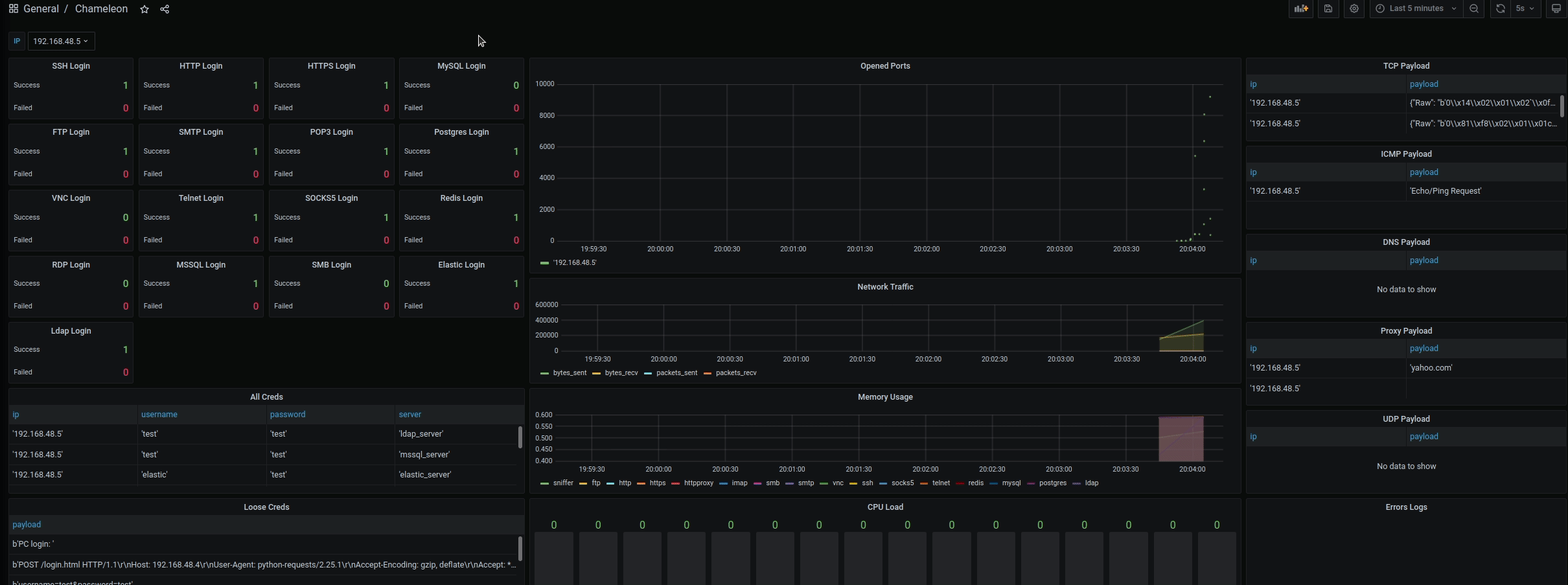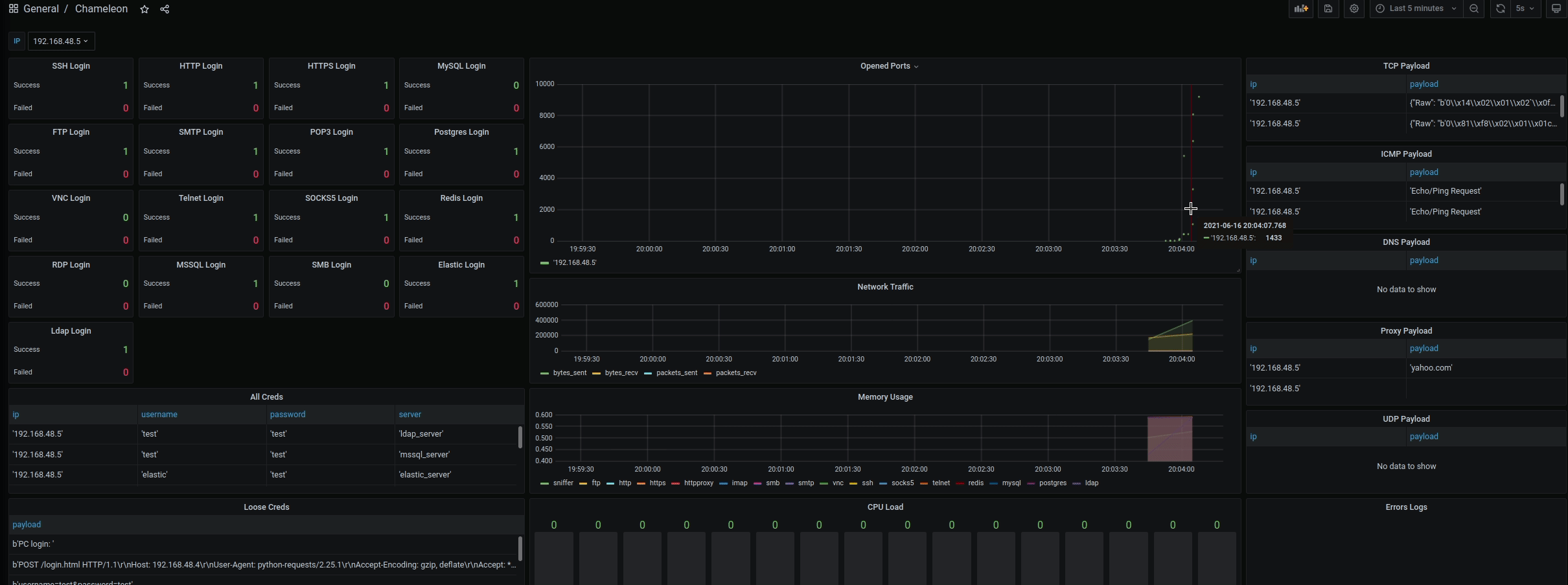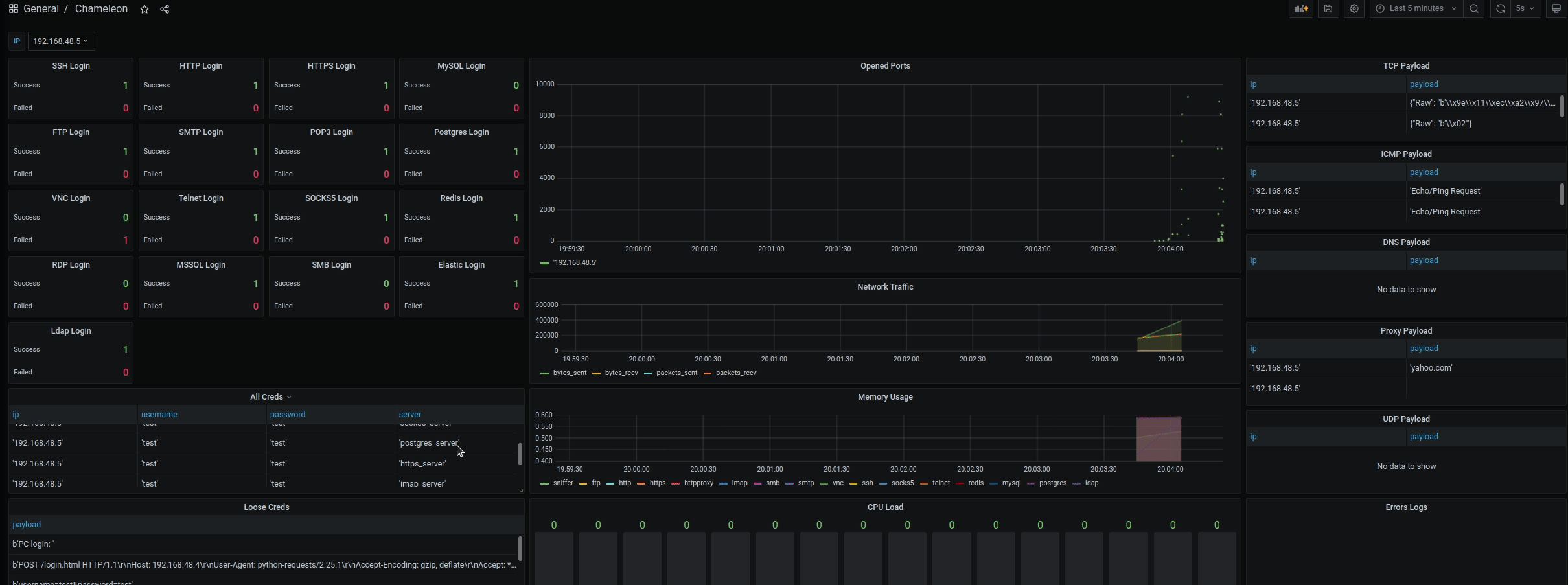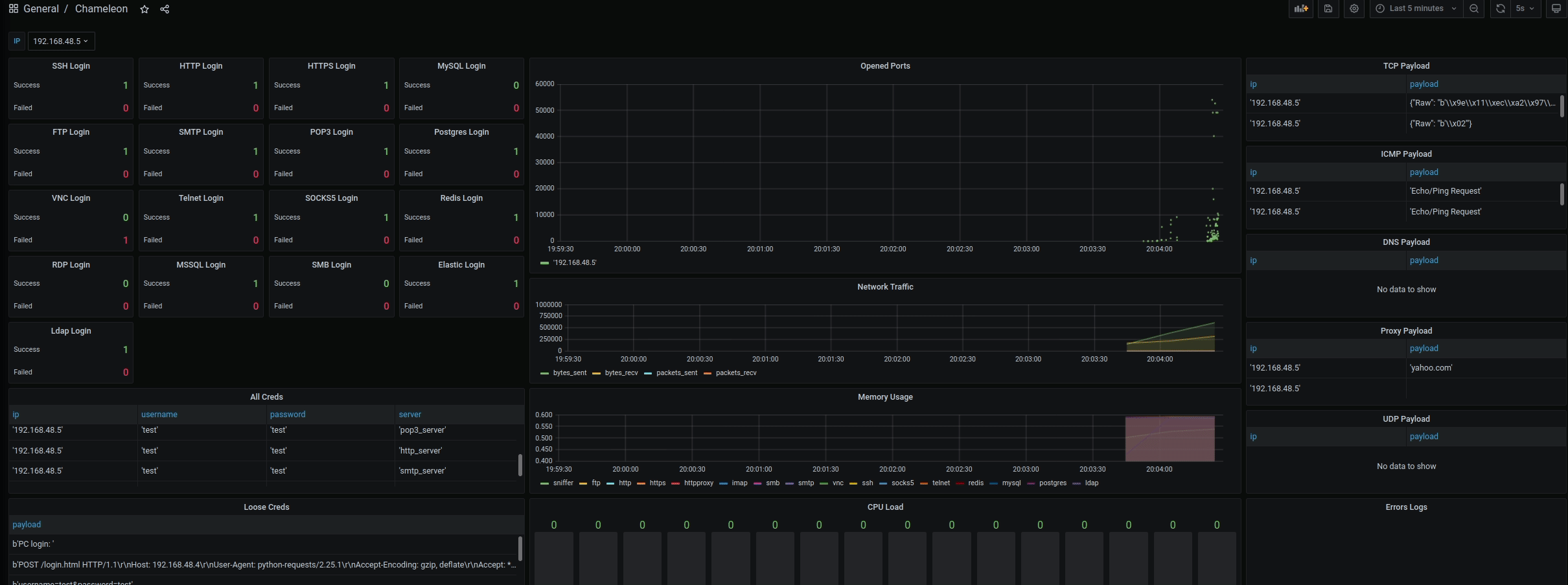
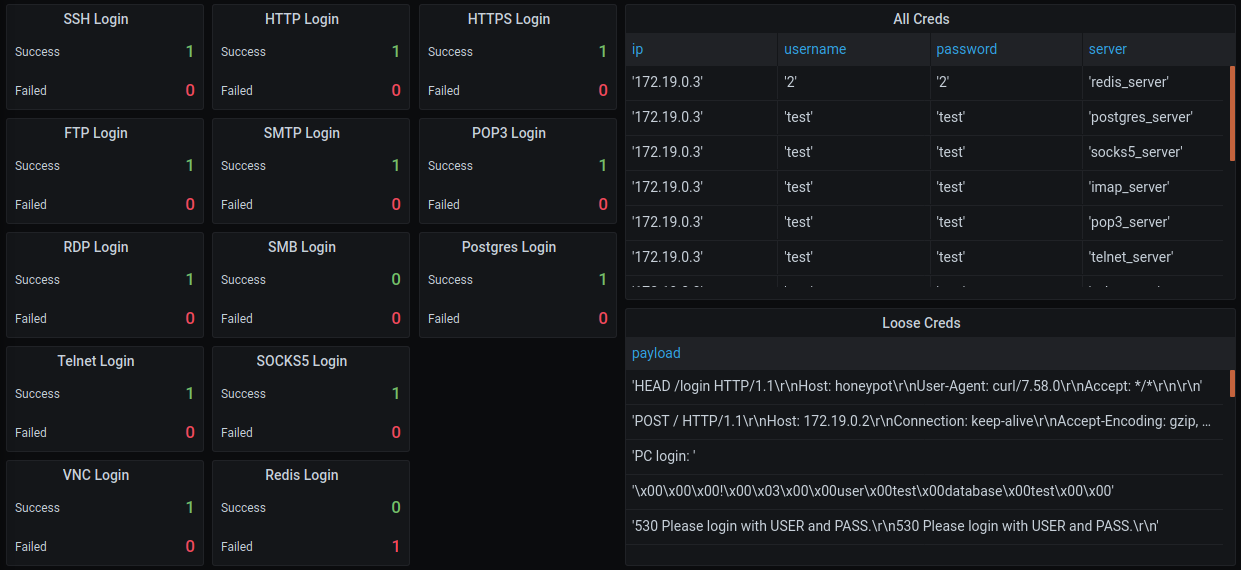
- Settings servers with username, password, and banner (Default username and password are test)
- ICMP, DNS TCP, and UDP payloads are parsed and checked against common patterns
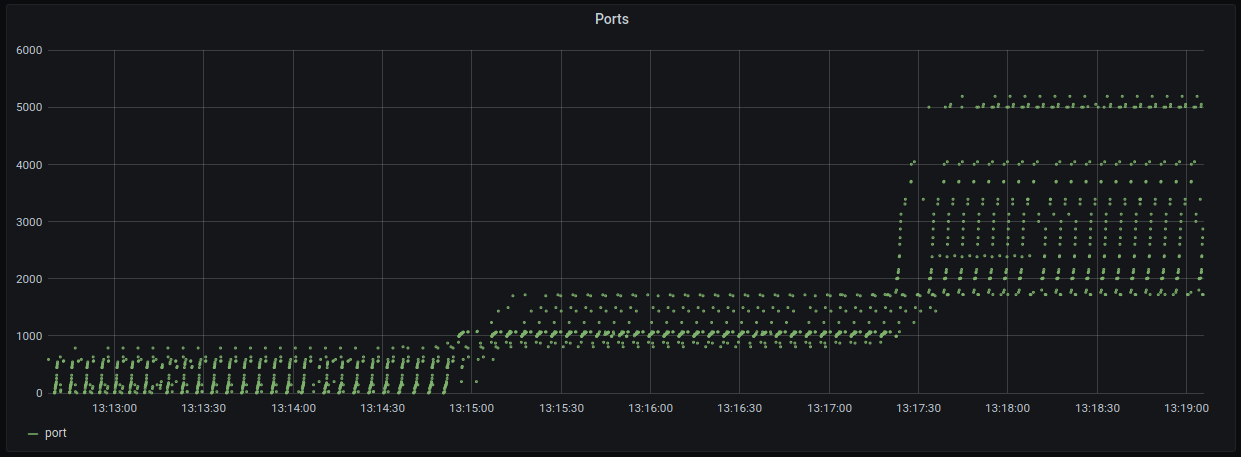
- Visualized Grafana interfaces for monitoring the results (Filter by IP - default is all)
- Unstructured and structured logs are parsed and inserted into Postgres
- All honeypots contain clients for testing the servers
- All ports are opened and monitored by default
- Easy automation and can be deployed on AWS ec2
- & More features to Explore
git clone https://github.com/qeeqbox/chameleon.git
cd chameleon
sudo chmod +x ./run.sh
sudo ./run.sh testThe Grafana interface http://localhost:3000 will open automatically after the initialization process (username is admin and password is admin). If you don't see the Chameleon dashboard, click on the search icon in the left bar and add it.
git clone https://github.com/qeeqbox/chameleon.git
cd chameleon
sudo chmod +x ./run.sh
sudo ./run.sh deployThe Grafana interface http://localhost:3000 will open automatically after the initialization process (username is changeme457f6460cb287 and password is changemed23b8cc6a20e0). If you don't see the Chameleon dashboard, click on the search icon in the left bar and add it.
Wait for a few seconds until honeypot shows the IP address
...
honeypot_1 | Your IP: 172.19.0.3
honeypot_1 | Your MAC: 09:45:aa:23:10:03
...You can interact with the honeypot from your local system
ping 172.19.0.3
or run any network tool against it
nmap 172.19.0.3sudo docker run -it --privileged -v /var/run/docker.sock:/var/run/docker.sock ubuntu:latest
git clone https://github.com/qeeqbox/chameleon.git
cd chameleon
sudo chmod +x ./run.sh
sudo ./run.sh testYou can do that by using this package honeypots
Raspberry Pi 3B+ (setup zram first to avoid lockups)
apt-get update -y && apt-get install -y iptables-persistent tcpdump nmap iputils-ping python python-pip python-psycopg2 lsof psmisc dnsutils
pip install scapy==2.4.4 netifaces==0.10.9 pyftpdlib==1.5.6 sqlalchemy==1.3.23 pyyaml==5.4.1 paramiko==2.7.1 impacket==0.9.22 twisted==20.3.0 psutil==5.8.0 requests==2.25.1 redis==3.5.3 mysql-connector-python==8.0.23 pygments==2.5.2
pip install -U requests[socks]
pip install -Iv rsa==4.0
pip install rdpy==1.3.2- DNS (Server using Twisted)
- HTTP Proxy (Server using Twisted)
- HTTP (Server using Twisted)
- HTTPS (Server using Twisted)
- SSH (Server using socket)
- POP3 (Server using Twisted)
- IMAP (Server using Twisted)
- STMP (Server using smtpd)
- RDP (Server using Twisted)
- SMB (Server using impacket)
- SOCK5 (Server using socketserver)
- TELNET (Server using Twisted)
- VNC (Emulator using Twisted)
- Postgres (Emulator using Twisted)
- Redis (Emulator using Twisted)
- Mysql (Emulator using Twisted)
- Elasticsearch (Emulator using http.server)
- Mssql (Emulator using Twisted)
- Oracle (Coming..)
- ldap (maybe)
- 2020.V.01.05 added mysql
- 2020.V.01.04 added redis
- 2020.V.01.03 switched ftp servers to twisted
- 2020.V.01.02 switched http and https servers to twisted
- 2020.V.01.02 Fixed changing ip in grafana interface
Twisted, documentation, Impacket, documentation, Grafana, documentation, Expert, Twisted, robertheaton
By using this framework, you are accepting the license terms of all these packages: grafana, tcpdump, nmap, psycopg, dnsutils, scapy, netifaces, pyftpdlib, sqlalchemy, pyyaml, paramiko, impacket, rdpy, psutil, requests, FreeRDP, SMBClient, tigervnc
securehoney kitploit redteaming my-infosec-awesome blackhatethicalhacking securityonline redpacketsecurity
- Do not deploy without proper configuration
- Setup some security group rules and remove default credentials
- Almost all servers and emulators are stripped-down - You can adjust that as needed
- Please let me know if I missed a resource or dependency