Learn one of the OWASP vulnerabilities every day for 10 days in a row. A new task will be revealed every day, where each task will be independent from the previous one. These challenges will cover each OWASP topic:
My First Try at Hacking Lab Write-Ups ;)
Vulnerability: Injection
Target: http://MACHINE_IP/evilshell.php.
Simple Description: A Search bar is given, we also know that the PHP Code for the same allows command injection
Questions:
Question 1: What strange textfile is in the website root directory ?
My Solution:
A simple ls command gave away the name of a textfile.
Ideally, I should have also checked the root directory using pwd.
Question 2: How many non-root/non-service/non-daemon users are there ?
My Solution:
This seemed difficult at first, on running cat /etc/passwd, even though all the users were displayed, still I wasn't able to figure out much.
I searched up online and then used cut -d: -f1 /etc/passwd to get only the usernames. Comparing this output with a similar output on my own
terminal led me to realise that there are no such non-special users.
Question 3: What user is this app running as ?
My Solution:
This was easy, a simple whoami did the task.
Question 4: What is the user's shell set as ?
My Solution:
This was the trickiest in my opinion. I used this amazing guide on the forums to figure it out. Link to the Article. On deeper analysis of the cat /etc/passwd result. We find the answer. I owe this answer fully to this article. I realised that I needed to know what cat /etc/passwd actually gave.
Question 5: What version of Ubuntu is running ?
My Solution:
This again was pretty easy. lsb_release -a did the job.
Question 6: Print out the MOTD. What favorite beverage is shown ?
My Solution:
I tried a pretty amateur apporach at this. On opening the contents of the file that we found in *Question 1*, I thought I'd try out the same as the answer and it worked!
Yet actually, (again had to use this article) the "message-of-the-day" file had been changed to "00-header" as mentioned in the *Hint*.Thus, using cat /etc/update-motd.d/00-header, the answer was finally revealed.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: drpepper.txt
Q2: 0
Q3: www-data
Q4: /usr/sbin/nologin
Q5: 18.04.4
Q6: Dr Pepper
Vulnerability: Broken Authentication
Target: http://MACHINE_IP:8888
Simple Description: A SignIn Button and a Register Button is given on the top, 2 fields are given for Sign-Up and a new set of 3 fields is opened up on Registration
Questions:
Question 1: What is the flag that you found in darren's account ?
My Solution:
We are given that there is an account named darren which contains a flag. To access this account, if we try something like darren (Notice the space at the end), or even darren (3 spaces in the front), for REGISTERING a new account and then we try Logging in with this account. Then we are able to access the account details, in this case, the flag from the actual darren account.
Question 2: Now try to do the same trick and see if you can login as arthur.
Not Solution Based, only apply the above method again.
Question 3: What is the flag that you found in arthur's account ?
My Solution:
By trying the same method as in Darren's account, we are able to reach the flag in this one too!
What's important though, is going to the next level. Thus, I tried out various different types of alternative inputs like arthur. art hur _arthur "arthur".
Well, none of those actually work and thus I realised that only blank spaces can be used to check Broken Authentication successfully.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: fe86079416a21a3c99937fea8874b667
Q2: No Answer Required
Q3: d9ac0f7db4fda460ac3edeb75d75e16e
Vulnerability: Sensitive Data Exposure
Target: http://MACHINE_IP
Simple Description: A wesbites is given. We need to access the SQLite database and find crucial leaked information
Questions:
Question 1: What is the name of the mentioned directory ?
My Solution:
I used the hint for this. But after that it became pretty clear. An important point to be noted is that View Page Source and more over looking it at very closely is a really necessary skill that all budding Ethical Hackers and Security Researchers need to understand!
Question 2: Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data ?
My Solution:
This was pretty simple. When sensitive data is directly under the root directory, then you can directly see the "database file" that we need to access.
Question 3: Use the supporting material to access the sensitive data. What is the password hash of the admin user ?
My Solution:
This requires understanding the support material about SQLite Databases. The basics are as follows:
- Run
filein the terminal. This gives you the "File Type" and "Version" of the same file-type. - Since it is an SQLite DB, we use
sqlite3to access the tables under it. - A really important command to be used is
.help. Infact, we should use this anywhere and everywhere, if we're unfamiliar to the specific command.
Question 4: Crack the hash. What is the admin's plaintext password ?
My Solution:
Crack-Station is the "go-to" place for Cracking Hashes. What's more interesting is that you can download the 15GB wordlist for your own use as well!
Question 5: Login as the admin. What is the flag ?
My Solution:
Once we have the admin access from the SQLite Database, we just need to login as admin and the flag appears right there.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: /assets
Q2: webapp.db
Q3: 6eea9b7ef19179a06954edd0f6c05ceb
Q4: qwertyuiop
Q5: THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}
Bonus:
This was really fun to try out. Here goes the description for the same:
To spice things up a bit, in addition to the usual daily prize draw this box also harbours a special prize: a voucher for a one month subscription to TryHackMe. There may or may not be another hint hidden on the box, should you need it, but for the time being here's a starting point: boxes are boring, escape 'em at every opportunity.
I tried various things here, ssh, nmap, metasploit, but unfortunately, I failed to get through or even find the answer. I wasn't disheartened though. This bonus question has been an amazing learning experience 😊
Vulnerability: XML External Entity
Target: http://MACHINE_IP
Simple Description: An XXE Payload TextField is given, Certain tasks are to be done
Questions:
P1: eXtensible Markup Language Basics
Here we had to learn the basics of XML, its syntax and its use.
Question 1: Full form of XML
Question 2: Is it compulsory to have XML prolog in XML documents ?
Question 3: Can we validate XML documents against a schema ?
Question 4: Full form of XML
P2: XML DTD Basic
Now we go into the basics of DTD.
DTD stands for Document Type Definition. A DTD defines the structure and the legal elements and attributes of an XML document.
Question 1: How do you define a new ELEMENT ?
Question 2: How do you define a ROOT element?
Question 3: How do you define a new ENTITY?
P3: XXE Payload basics
We get a really detailed description of how do we really use XXE payloads. It is possible to print out data on the webpage easily by using
What is more important to understand it the fact, that by using some system commands, we can also print /etc/passwd contents on it!
P4: XXE Exploitation Basics
Finally!!!
Now we have to actually use these exploits learnt to do the following:
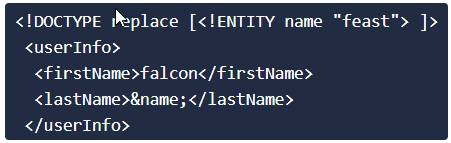
Question 1: Try to display your own name using any payload.
My Solution:
As far as this goes, based on the first exploit in P3, I could have just replaced "feast" with my name. But I realised, that if you just put 2 opening and closing tags, like <name>Nishant<name/>, then also, the exploit works well
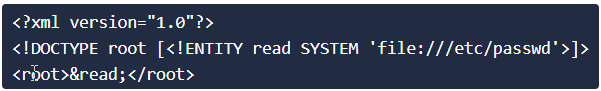
Question 2: See if you can read the /etc/passwd
My Solution:
This is the second exploit mentioned in P4.
Question 3: What is the name of the user in /etc/passwd ?
My Solution:
Well, navigating to the end of the result that we recieved in the previous question, we find that the user name is clearly visible (It stands apart from the root/service/daemon users)
Question 4: Where is falcon's SSH key located ?
My Solution:
I needed to search this up online as to where the SSH Keys are actually located.
Honestly speaking though, I didn't have much confidence to try it out that time, even though I had found the answer. I'm thankful to this great write-up, that helped me out. I'd like to take this moment to say that never lose faith in your hardwork or yourself.
You have great potential! Always remember that and Never Give Up!
Question 5: What are the first 18 characters for falcon's private key ?
My Solution:
Once, we displayed the data from the SSH Key file (using the method like the second exploit), we were able to easily view the SSH Key!
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: No Answer Required.
Q2: No Answer Required.
Q3: falcon
Q4: /home/falcon/.ssh/id_rsa
Q5: MIIEogIBAAKCAQEA7
Vulnerability: Broken Access Control
Target: http://MACHINE_IP
Simple Description: A target machine is given, IDOR and Broken Access Control are to be learned and exploited!
Questions:
Question 1: Read and understand how IDOR works.
My Understanding of IDOR:
IDOR or Insecure Direct Object Reference, is an important vulnerability which comes under Broken Access Control.
Being able to access data which is not meant to be accessed by normal users, is an exaple of Broken Access Control. In simple words, say that you are able to login to your bank account and the following is your link in the address bar, https://example.com/bank?account_number=1234. You might not notice this normally, but if you consider an attacker, then all they need to do is change the account number in the above URL and lo and behold!, all your data belongs to the attacker!
Question 2: Deploy the machine and go to http://MACHINE_IP - Login with the username being noot and the password test1234.
No Answer Required
Question 3: Look at other users notes. What is the flag ?
My Solution:
This is IDOR in action, the fact that we are able to change the note number paramter in the URL (http://MACHINE_IP/index.php?note=1), and then navigate to a specific note, shows how we are able to read and access someone else's data!
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: No answer needed
Q2: No answer needed
Q3: flag{fivefourthree}
Vulnerability: Security Misconfiguration
Target: http://MACHINE_IP
Simple Description: A target machine is given and the question is pretty simple. Hack the webapp and find the flag😅
Questions:
Question 1: Deploy the VM.
No Answer Required
An important point!
Pensive Notes is the target web-app and we wish to hack into it. As far as Security Misconfigurations go, not changing the default passwords is what leads to major problems!
Question 2: Hack into the webapp, and find the flag !
My Solution:
Turns out, that problems like these require a bit more effort. More than effort, they require experience! As a beginner, when I'm told to look into the "source code", I would naturally go to Inspect Element or View Page Source. With some help from the TryHackMe Discord Server, I realised and well, now have understood, that for source code and documentation, my go-to place is GitHub.
Moreover, sometimes using GitHub Search instead of Google Search can help you reach the solution.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: No answer needed
Q2: thm{4b9513968fd564a87b28aa1f9d672e17}
Vulnerability: Cross-Site Scripting
Target: http://MACHINE_IP
Simple Description: Try out XSS on http://MACHINE_IP/reflected and http://MACHINE_IP/stored , to answer the following questions!
Questions:
Question 1: Deploy the VM.
No Answer Required
Question 2: Go to http://MACHINE_IP/reflected and craft a reflected XSS payload that will cause a popup saying "Hello".
My Solution:
Now see, this is something important to note. Ethical Hacking is NOT the use of random tools or scripts to gain access. Then you just exist as a script kiddie. To really get good at it (I'm a beginner😅, by the way), you must learn certain core concepts and perhaps even go deep into them!
Take XSS for that matter. It is obvious to think that you might get around by copying some payload scripts. But no. Without some knowledge of JavaScript (and more advanced knowledge, if you wish to get good at this), you won't be able to craft new exploits or mould them according to your situation.
In short, Learn Everything!🙂.
Just like Albert Einstein once said, "Education is not the learning of facts, but the training of the mind to think", similarly,
"Ethical Hacking is not the learning of tools, but the training of the mind figure out methodologies!
So as far as this exploit goes, it was a simple <script>onclick(alert("Hello"));</script> script which did the magic. After clicking on the search button, first we see "Hello" and then the answer.
Question 3: On the same reflective page, craft a reflected XSS payload that will cause a popup with your machines IP address.
My Solution:
This is an example of moulding or re-crafting your own exploit. Take <script>onclick(alert("Hello"));</script> and instead of "Hello" , use window.location.hostname. To validate my point about learning JavaScript, here is a picture of the hint from TryHackMe.
**Question 4:**
Now navigate to http://MACHINE_IP/stored and make an account. Then add a comment and see if you can insert some of your own HTML. **My Solution:**
Okay, so what this page basically has a comment box, where the input data is dangerously unsanitised. Adding a simple <h1>Hi</h1>, would help you see the answer right on the page!
Question 5: On the same page, create an alert popup box appear on the page with your document cookies.
My Solution:
This is similar to Question 3. instead of window.location.hostname, just use document.cookie.
Question 6: Change "XSS Playground" to "I am a hacker" by adding a comment and using Javascript.
My Solution:
Finally, the part that seems most exciting! You can change the way the wesbite looks! And that too for all Users!
I did have to use a hint for this though. Turns out, that here we use something like <script>document.querySelector('#thm-title').textContent = 'I am a hacker'</script> to change the title. What's more important is, that we can similarly affect other elements in the page if we known their span id.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: No answer needed
Q2: ThereIsMoreToXSSThanYouThink
Q3: ReflectiveXss4TheWin
Q4: HTML_T4gs
Q5: W3LL_D0N3_LVL2
Q6: websites_can_be_easily_defaced_with_xss
Vulnerability: Insecure Deserialization
Target: http://MACHINE_IP
Simple Description: Learn about cookies and Remote Code Execution to gather the flags!
Questions:
P1: Insecure Deserialization Basics
An Introduction to Insecure Deserialization and its impact was given. According to Acunetix(2017), Insecure Deserialization is a vulnerability which occurs when untrusted data is used to abuse the logic of an application (Taken from the written material on the TryHackMe Room).
Question 1: Who developed the Tomcat application ? Hint: Give the name of the company, not the developer.
Question 2: What type of attack that crashes services can be performed with insecure deserialization ?
P2: Insecure Deserialization-Objects
This was pretty simple. Here we discuss a well known concept of Object Oriented Programming or OOP and discuss about states and behaviours.
Question 1: Select the correct term of the following statement: if a dog was sleeping, would this be: A) A State B) A Behaviour
P3: Insecure Deserialization-Deserialization
We get a really detailed description of Serialization and Deserialization. Using an analogy of a giving directions to foreigner by giving them a map, TryHackMe paints a very clear picture of how Data is conversion to bytes and back!
Question 1: What is the name of the base-2 formatting that data is sent across a network as?
P4: Insecure Deserialization-Cookies
As far as the concept of cookies goes, I guess this is one of the most simple yet the most appropriate description of it that I have come across. We get to understand what cookies are, what attributes do they have and how they are created in Flask.
Question 1: If a cookie had the path of webapp.com/login, what would the URL that the user has to visit be ?
Question 2: What is the acronym for the web technology that Secure cookies work over ?
P5: Insecure Deserialization-Cookies Practical
This one is fun for 2 reasons.
(1) We get to find Flags!😁
(2) We find those flags by manipulating Cookies!
Question 1: 1st flag (cookie value)
My Solution:
Okay, so we're given that the first flag is somehwere in that cookie which has both plainText and base64 encoded text. That points directly towards the Cookie "Value". Here the Session ID is Base64 Encoded and decoding it using Burp-Suite's Decoder does the work.
Question 2: 2nd flag (admin dashboard)
My Solution:
This is pretty simple, but can spell chaos if it happens in an actual application! So, there is a userType cookie field and contains whether the user is a normal one or an admin. Changing this value by logging in as a normal user, can help you reach the admin dashboard and get the flag.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: THM{good_old_base64_huh}
Q2: THM{heres_the_admin_flag}
P6: Insecure Deserialization-Remote Code Execution
And finally! Something that I personally am fond of doing (but never managed to do successfully till now😅). We generate a reverse shell to get data from a flag.txt file
Question 1: flag.txt (That's it. That's the question.)😅
My Solution:
Well, this one is pretty tricky. I'd highly recommend anyone who wishes to know about Remote Code Execution, to go over the actual write up in the TryHackMe room. This basically involves the following
- Creating a new cookie field,
- Opening a form,
- Making a python script to create a Base64 Encoded Cookie,
- Opening a netcat listener,
- Changing the cookie value in the new field,
- And finally, getting a reverse shell to the Website's Server.
cd .. and an ls would do.
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answer. Thanks.)
Q1: 4a69a7ff9fd68
Vulnerability: Components with Known Vulnerabilities
Target: http://MACHINE_IP
Simple Description: We learn a very important concept for any ethical hacker out there. Using exploits!
Questions:
Question 1: How many characters are in /etc/passwd (use wc -c /etc/passwd to get the answer).
My Solution:
Okay. So even though there were 2 sections before this one (related to this Vulnerability), what they primarily focussed on, was taking about the basics of these and as to why does OWASP rate it a a 3 (A high risk). Turns out, that using out dated software and not updating it frequently can lead to an attacker using known exploits to get into and compromise a system.
The exploitation turns out to be quite simple as well. Exploit-DB has some great exploits, for almost every system out there.
Using this, we had to figure out a way to execute remote code on our "bookstore" application that's the hint, by the way😉.
TryHackMe, like always, leaves out an important note for budding ethical hackers.
(Note: exploit-db is incredibly useful, and for all you beginners you're gonna be using this a lot so it's best to get comfortable with it)
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: 1611
Vulnerability: Insufficient Logging and Monitoring
Target: Download login-logs.txt and
Simple Description: A login-logs file is given, we need to analyse it and answer the questions.
Questions:
Question 1: What IP address is the attacker using ?
My Solution:
This is easily visible through the unauthorised attempts that the attacker is making, by repeatedly using some common usernames for admin pages.
Question 2: What kind of attack is being carried out ?
My Solution:
Since the user is not trying any type of specific methodology or tool, and is just randomly trying out known credentials. The technique becomes easily obvious
Answers: (CAUTION!: If you are also trying this machine, I'd suggest you to maximise your own effort, and then only come and seek the answers. Thanks.)
Q1: 49.99.13.16
Q2: Brute Force

.png)
.png)
.png)
.png)
.png)
_(Blurred).png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
_(Blurred).png)
_(Blurred).png)
.png)
.png)