Author: Thomas Stern
Date: 26/01-2023
It is possible via the import languages functionality to upload and arbitrary file. This file could be a webshell that would allow for execution of code on the server.
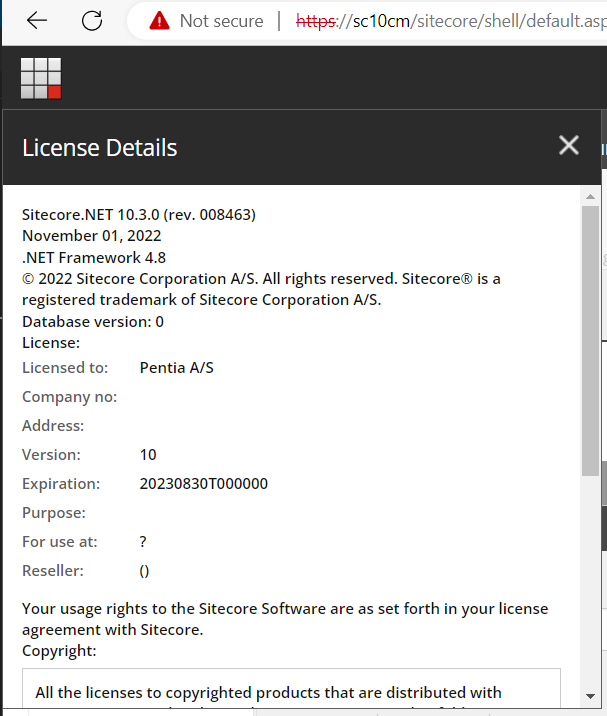
For testing this vulnerability a Sitecore 10.3 instance was spawned on a local machine through docker. This vulnerability haven't been tested on previous versions of Sitecore, but earlier version might be vulnerable for the same technique.
Host: Windows 11 Running Docker for Desktop Sitecore 10.3
Since this is an authenticated vulnerability a valid set of credentials is required. For this testing instance admin/b was used
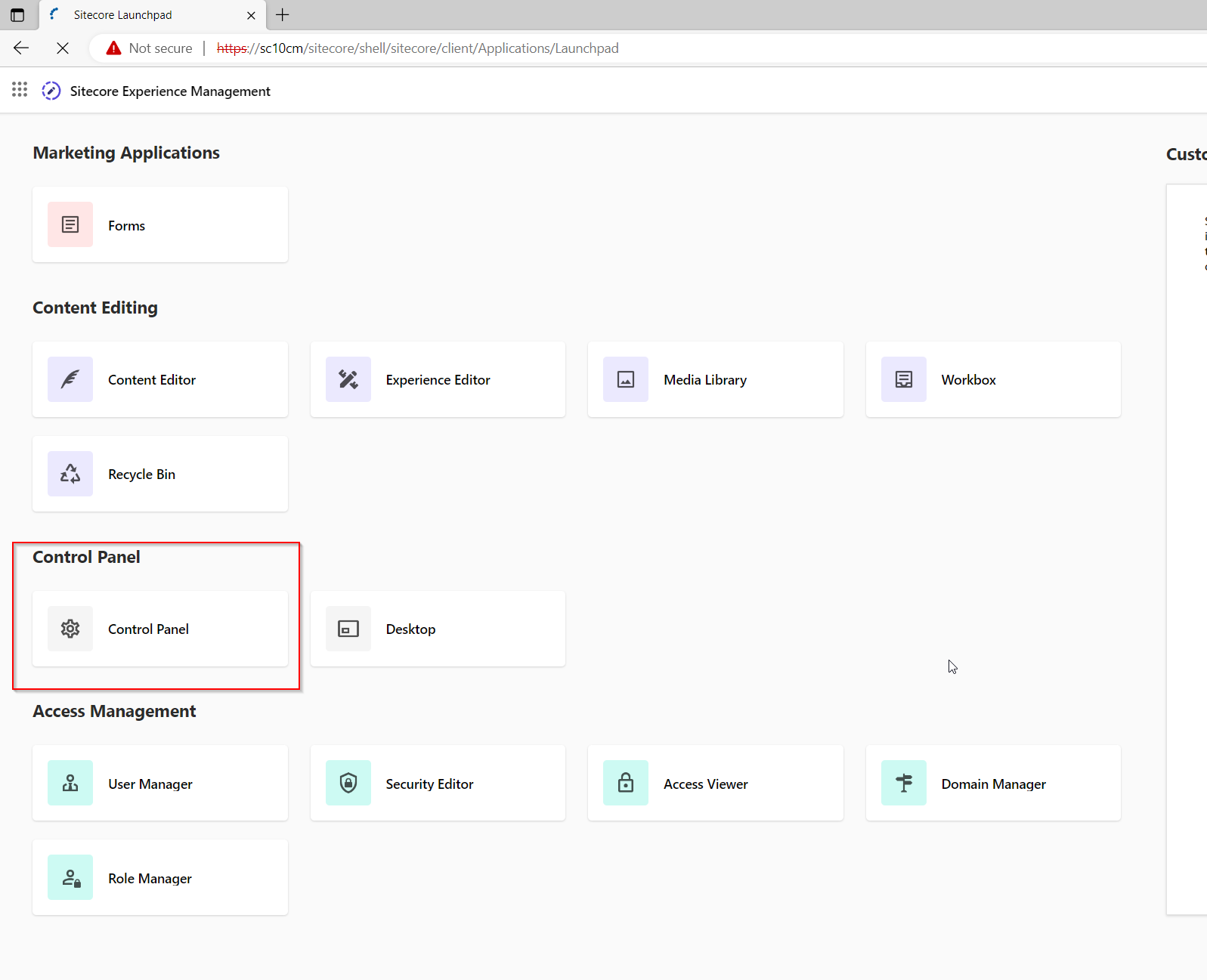
The toolbox is found under the control panel for Sitecore
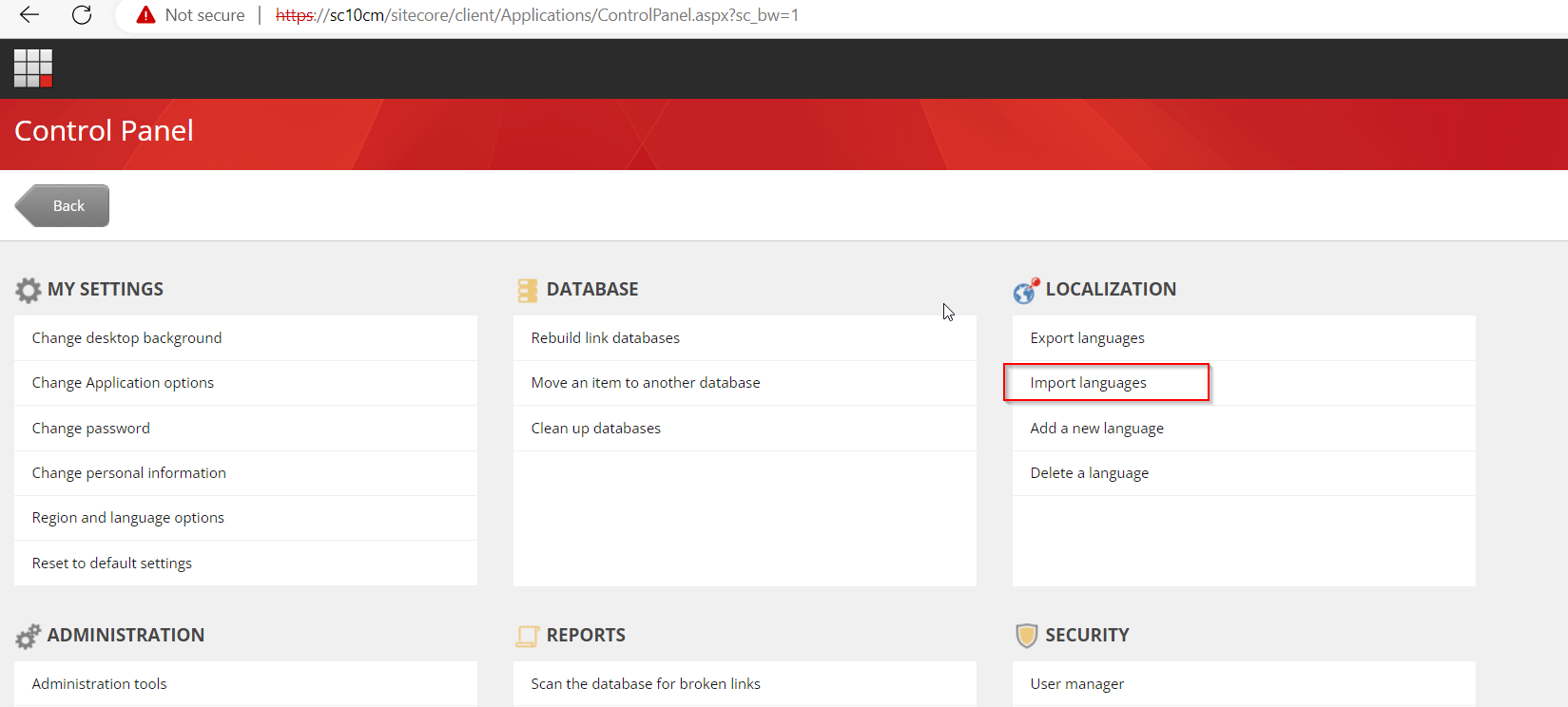
Now choose language import
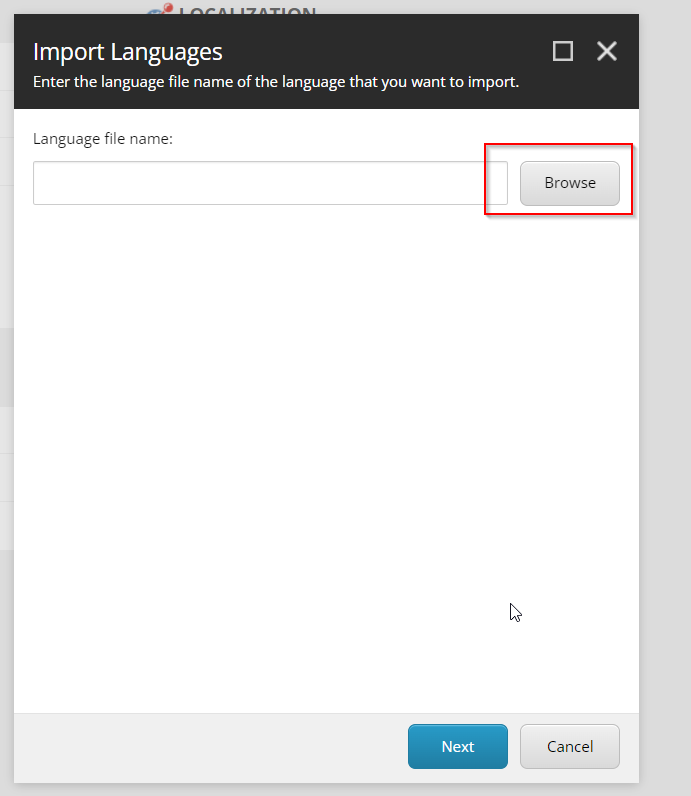
Start by choosing Browse
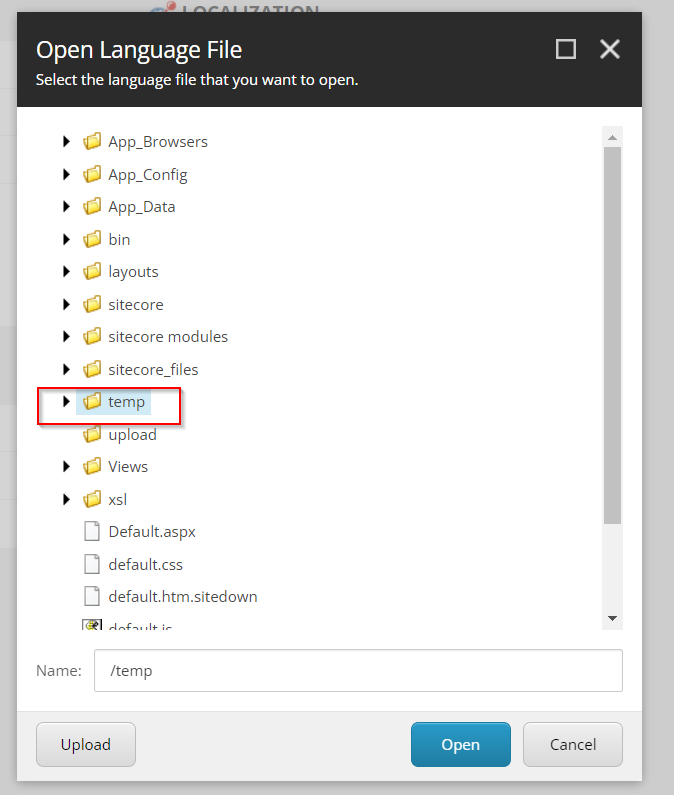
Next select the temp folder 'this will also be the destination for the shell.
The code used for testing is shown a simple webshell from downloaded from https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmdasp.aspx note a small modification was made to run powershell instead of the default cmd.
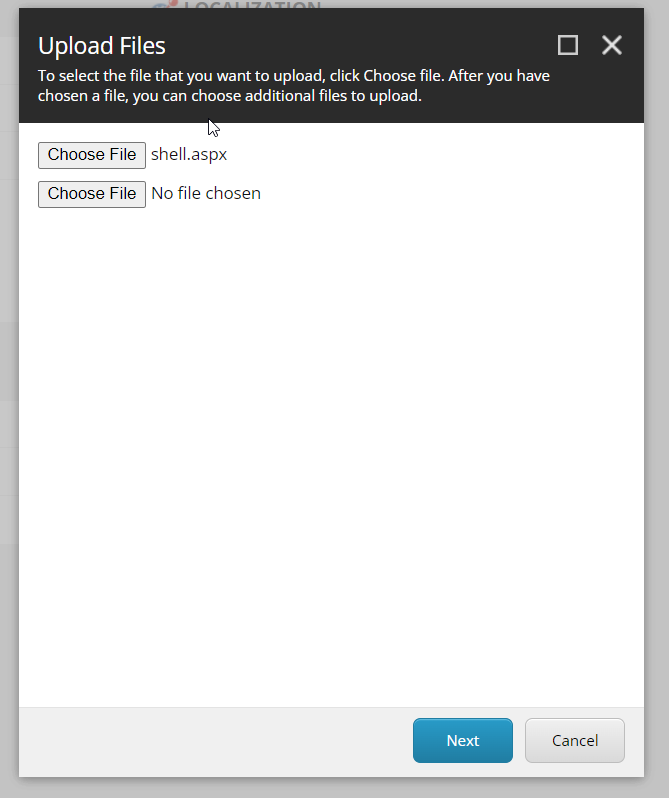
Choose upload button and select your shell and press next
You shell should now be uploaded
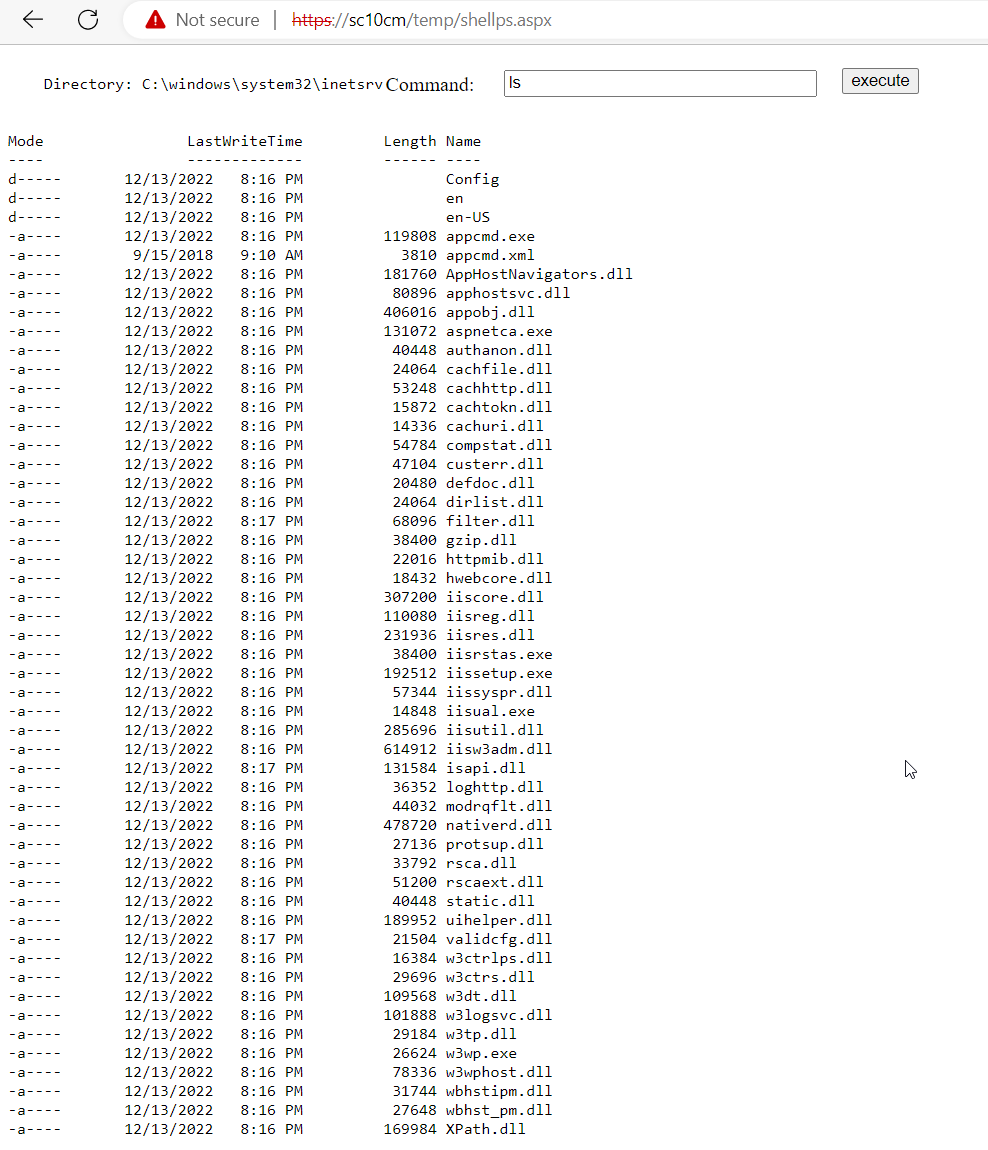
Started by navigating to the uploaded shell "https://sitename/temp/shell.aspx" With the shell uploaded it is now possible to have full code execution on the system
The code for uploading the language files should validate files being uploaded and only allow for executable files like aspx,exe and more. Also language files should only be uploaded to a directory that doesn't allow code execution. A way of doing this is by addaing a block rule to the web.config like the below. Note this will block all request to the two files.
<rule name="BlockFileUpload" enabled="true" patternSyntax="Wildcard" stopProcessing="true">
<match url="*" />
<conditions logicalGrouping="MatchAny">
<add input="{URL}" pattern="*sitecore/shell/Applications/Files/FileBrowser.aspx" />
<add input="{URL}" pattern="*sitecore/shell/Applications/Dialogs/Upload/Upload2.aspx" />
</conditions>
<action type="CustomResponse" statusCode="404" statusReason="File or directory not found." statusDescription="The resource you are looking for might have been removed, had its name changed, or is temporarily unavailable." />
</rule>