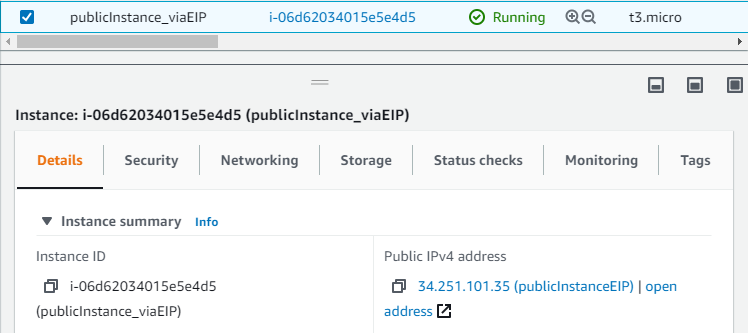
Typically EC2 instances are encountered in 3 different deployments.
- With directly attached Elastic IP.
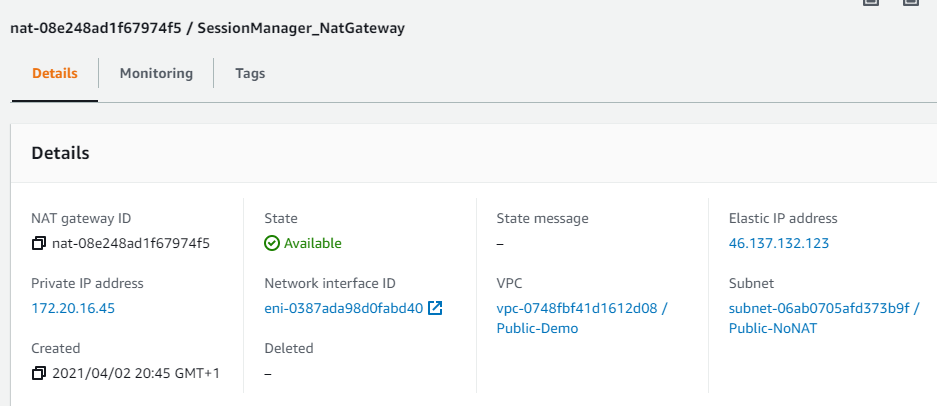
- Public access, via other architecture (such as NAT gateway or LoadBalancer).
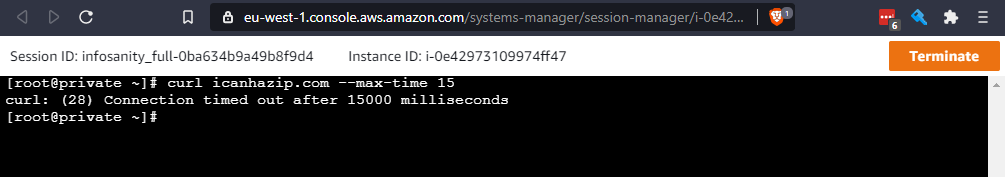
- Fully private, with no Internet access.
With the correct architecture, Session Manager (via AWS Systems Manager) can be leveraged to remotely manage all EC2 instances; without the need to expose the instances' management services directly.
The below diagram describes the network architecture for each use-case, as deployed by this Terraform code.
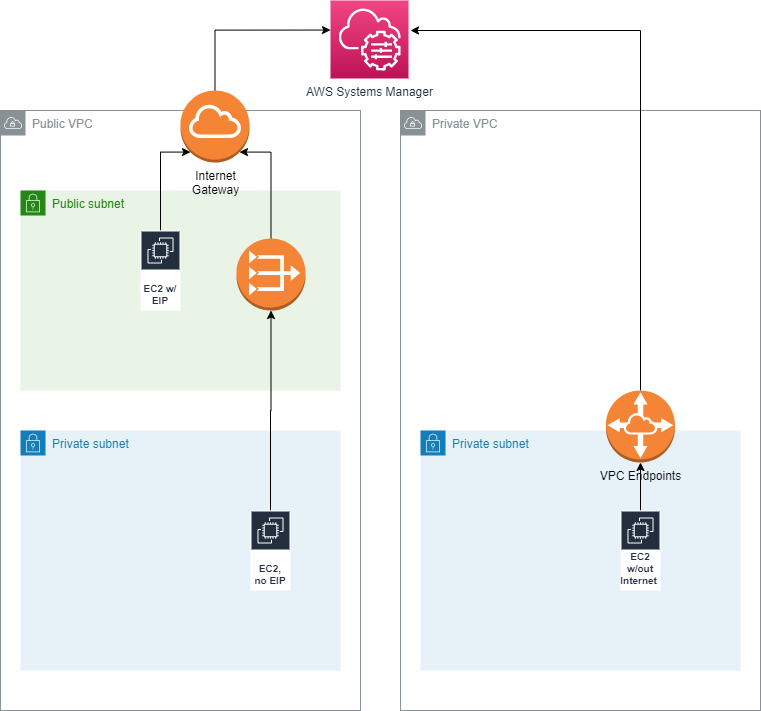
- EC2 intance must run SSM Agent
- IAM Instance role with access to SSM EndPoints
- Access to System Manager endpoints:
- ec2Messages
- SSMMessages
- SS
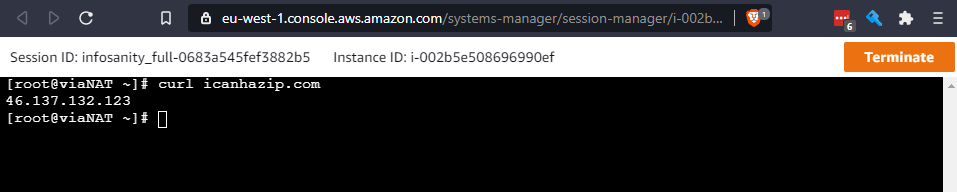
Deployment use-cases 1 & 2 are deployed within a public VPC, one with a directly attached elastic IP; the other in a private subnet, accessing the wider Internet via a NAT Gateway.
For the private instance, if they can't reach the required Systems Manager API endpoints, the services must come to the instance. In this case, via private VPC endpoints
Access to each EC2 instance, should be available via Session Manager Connect
Connect Session
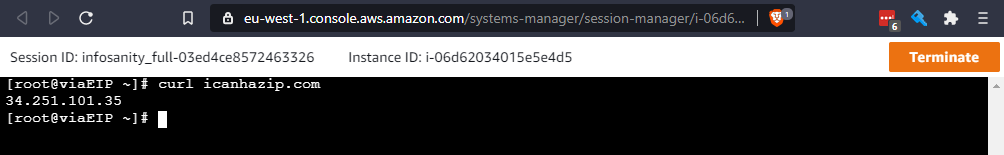 Matching assigned public EIP
Matching assigned public EIP