MultiFactor.SelfService.Windows.Portal
Also available in other languages: Русский
MultiFactor SelfService Portal is a website developed and maintained by MultiFactor for self-enrollment of a second authentication factor by users within an Active Directory corporate network.
The portal is a part of MultiFactor 2FA hybrid solution.
See documentation at https://multifactor.pro/docs/multifactor-selfservice-windows-portal/ for additional guidance on Self-Service Portal deployment.
Table of Contents
Features
- User's login and password verification in an Active Directory domain. Multiple domains are supported if a trust relationship is configured between them;
- Configuration of the second authentication factor by the end-user;
- User's password change (available only after the second-factor confirmation);
- Single Sign-On for corporate applications.
The portal is designed to be installed and operated within the corporate network perimeter.
First Steps
- Navigate to your Multifactor personal profile , and under the Resources section create a new website with the following paramteres:
Name and address:<could be any>;Token format:JwtRS256.
- Upon creation you should receive ApiKey and ApiSecret parameters. You will need these parameters to complete the installation.
Prerequisites
- Installation requires Windows server starting from 2012 R2;
- The server with the installed portal requires access to the
api.multifactor.ruhost via TCP port 443 (TLS); - You need to have a Web Server (IIS) role with Application Development -> ASP.NET 4.6 component installed on the server;
Configuration
Portal settings are stored in the web.config file in XML format.
<portalSettings>
<!--Name of your organization-->
<add key="company-name" value="ACME" />
<!--Name of your Active Directory domain to verify username and password -->
<add key="company-domain" value="domain.local" />
<!--Company logo URL address-->
<add key="company-logo-url" value="/mfa/content/images/logo.svg" />
<!-- [Optional] Require second factor for users in specified group only (Single Sign-On users). Second-factor will be required for all users by default if setting is deleted. -->
<!--add key="active-directory-2fa-group" value="2FA Users"/-->
<!-- [Optional] Use your users' phone numbers contained in Active Directory to automatically enroll your users and start send one-time SMS codes. Option is not used if settings are removed. -->
<!--add key="use-active-directory-user-phone" value="true"/-->
<!--add key="use-active-directory-mobile-user-phone" value="true"/-->
<!-- Multifactor API Address-->
<add key="multifactor-api-url" value="https://api.multifactor.ru" />
<!-- API KEY parameter from the Multifactor personal account -->
<add key="multifactor-api-key" value="" />
<!-- API Secret parameter from the Multifactor personal account -->
<add key="multifactor-api-secret" value="" />
<!-- [Optional] Access the Multifactor API via the HTTP proxy -->
<!--add key="multifactor-api-proxy" value="http://proxy:3128"/-->
<!-- Logging level: 'Debug', 'Info', 'Warn', 'Error' -->
<add key="logging-level" value="Info" />
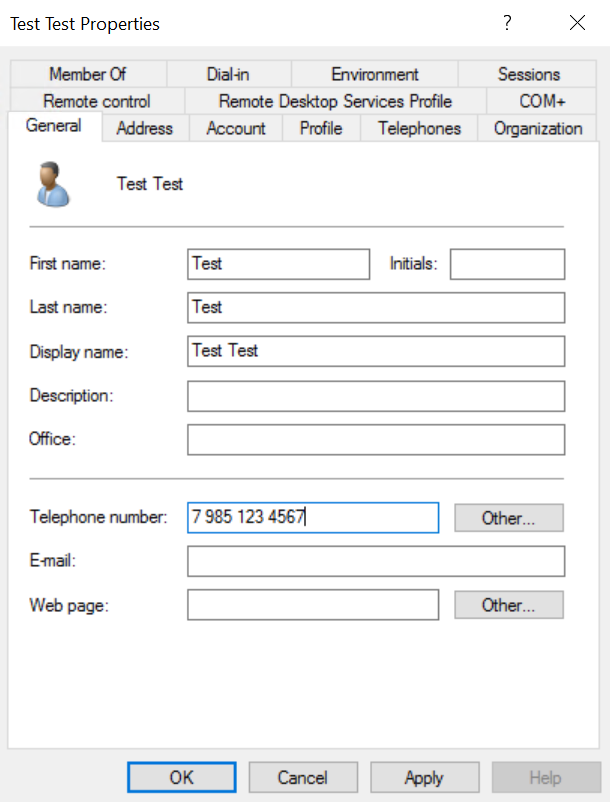
</portalSettings>If the use-active-directory-user-phone option is enabled, the component will use the phone stored in the General tab. All phone number formats are supported.
If the use-active-directory-mobile-user-phone option is enabled, the component will use the phone stored in the Telephones tab in the Mobile field. All phone number formats are supported.
Installation
-
Launch
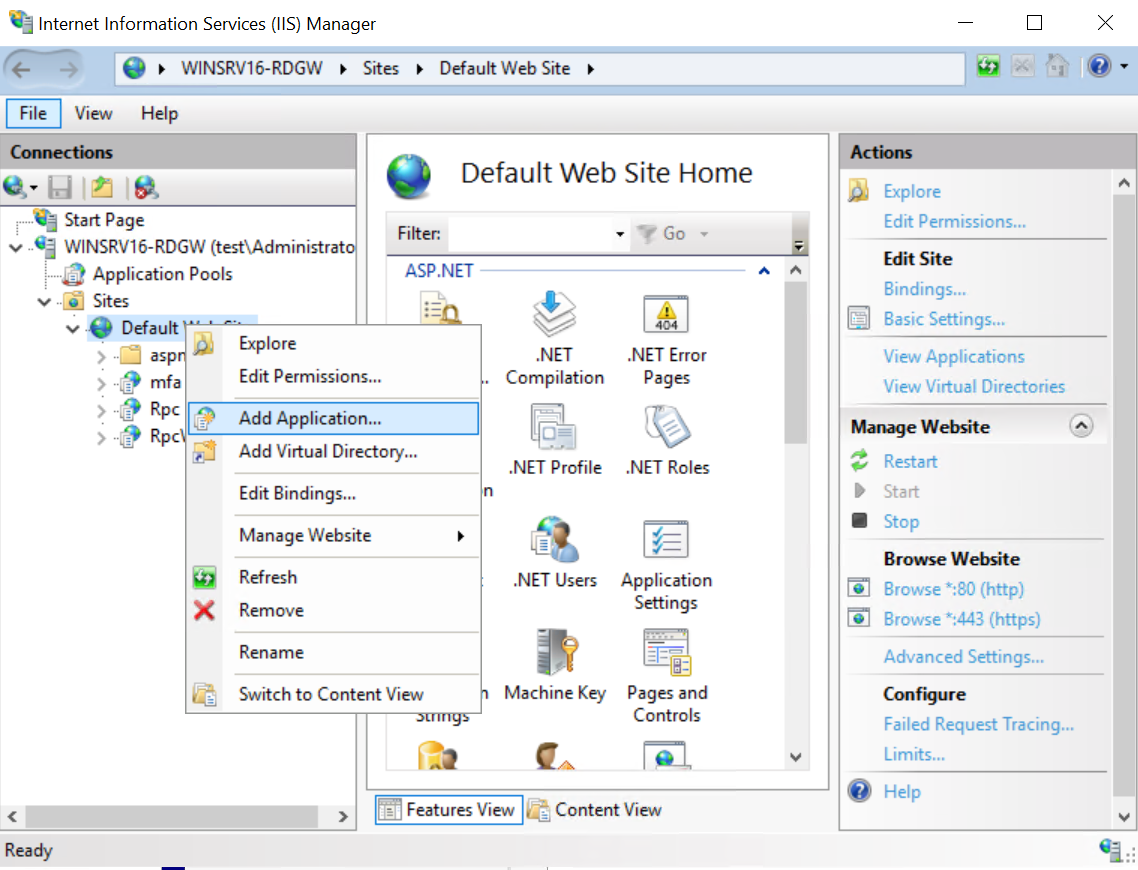
Server Manager->Tools->Internet Information Services (IIS) Manager; -
Right-click Default Web Site and select Add Application;
- Create a new application:
- Alias:
mfa - Physical path:
path to the Self-Service Portal directory
- Save and close.
Logs
The Self-Service Portal logs are located in the Logs directory. If they are not there, make sure that the directory is writable by the IIS AppPool\DefaultAppPool local user.
Access Portal
The portal can be accessed at https://yourdomain.com/mfa
Use Cases
The portal is used for self-enrollment and registration of the second authentication factor by users within the corporate network. It also acts as a Single Sign-On entry point for corporate SSO applications.
Once the second-factor is configured, users can securely connect via VPN, VDI, or Remote Desktop.
- Two Factor Authentication Windows VPN with Routing and Remote Access Service (RRAS)
- Two-factor authentication for Microsoft Remote Desktop Gateway
License
MultiFactor SelfService Portal is distributed under the MIT License. The component is a part of MultiFactor 2FA hybrid solution.