identinet-plugin is a browser extension that displays and verifies decentralized identity information of websites. The extension originated as a did:hack project.
-
Firefox: https://addons.mozilla.org/en-US/firefox/addon/identinet/
Attention: after installing the add-on, it's currently necessary to grant the plugin access to websites. Firefox doesn't prompt the user during installation to grant these permissions.
Navigate to Tools -> Add-ons and Themes. Select the identinet add-on and switch to the "Permissions" tab. Then grant the optional permission "Access your data for all websites".
-
Chrome: https://chrome.google.com/webstore/detail/identinet/hehmpjacggciaiknjpfkiecokomeeopm
After installation, the extension is added to the list of extensions. Pin the extension to the browser bar so that it is permanently visible.
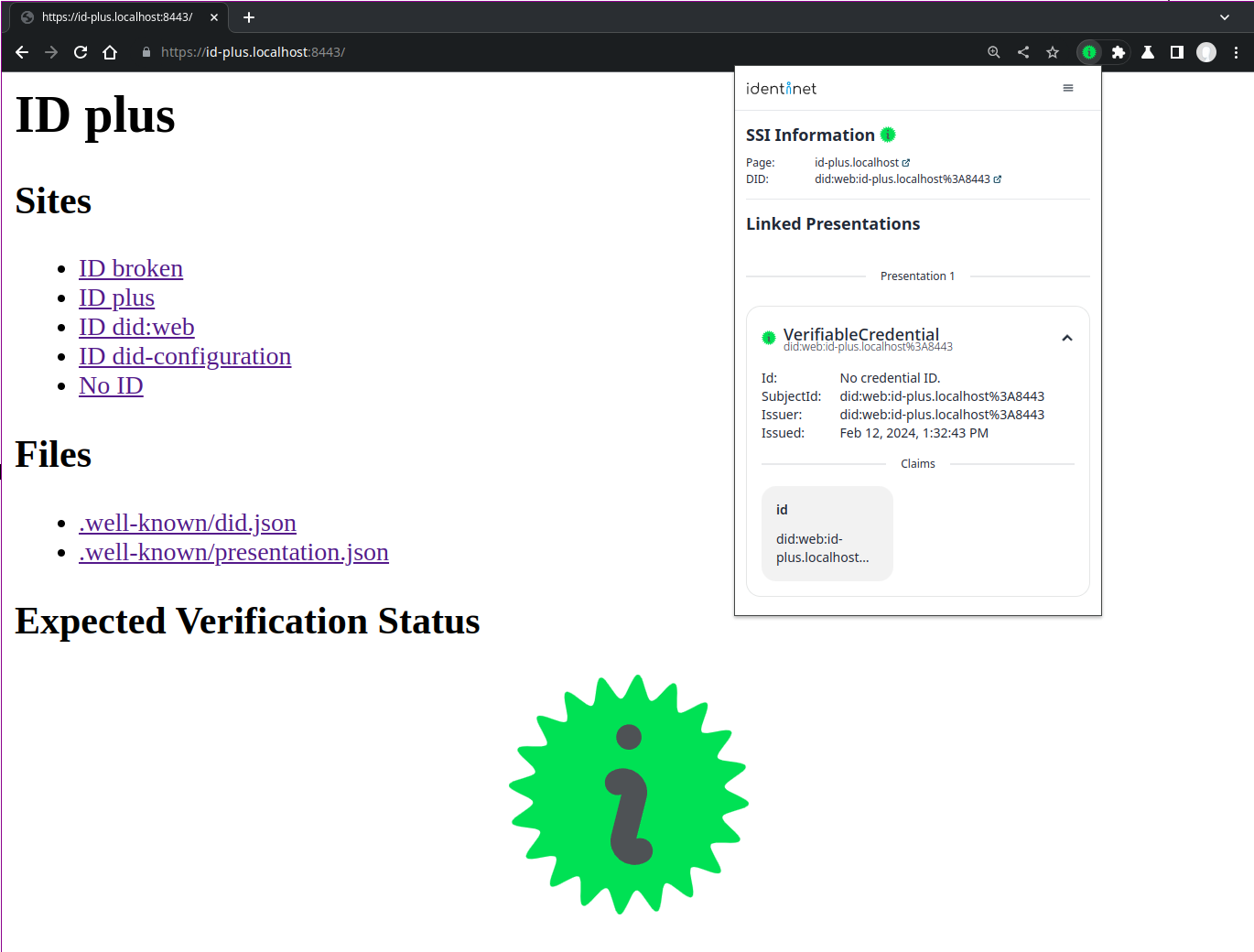
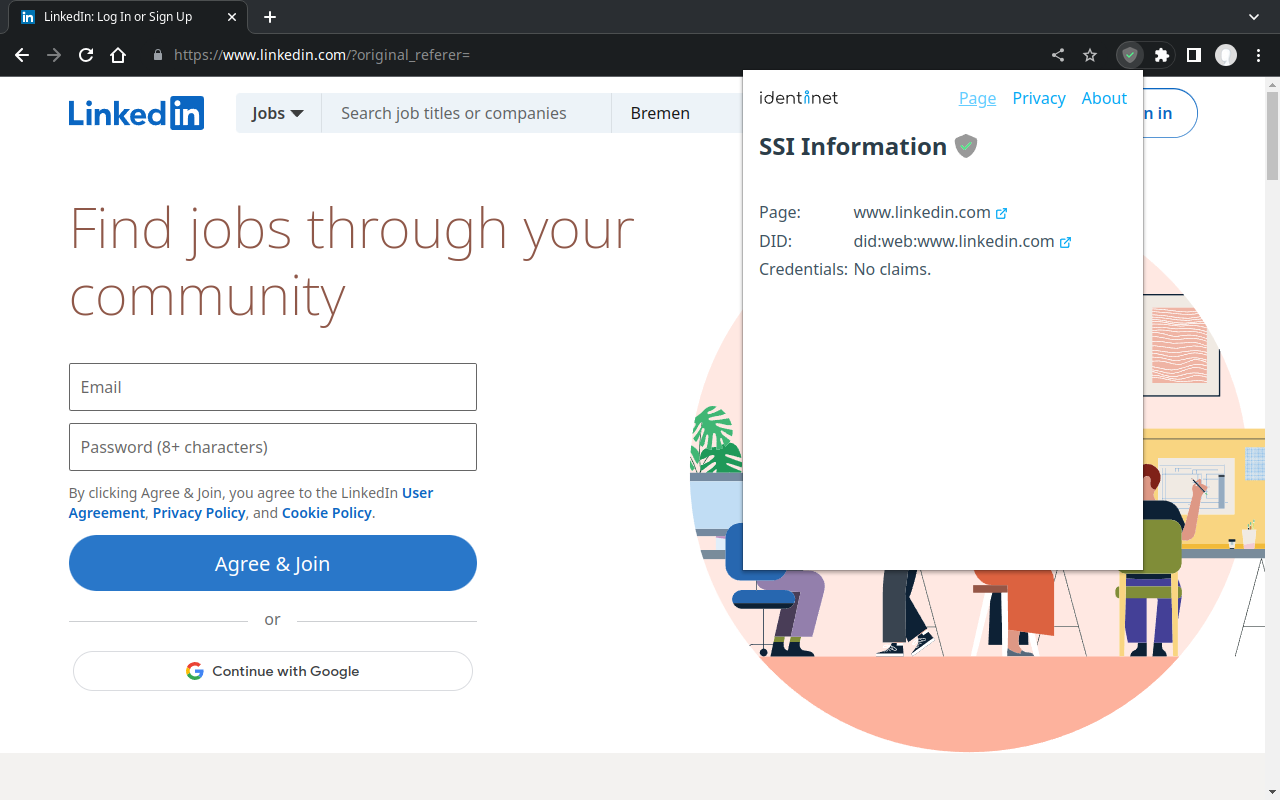
The availability of a DID document and additional credentials for the website is displayed with the following icons:
-
No DID document is available.
-
DID and credentials are available, the credentials have been successfully verified.
-
DID document incorrect or verification of credentials of failed.
Examples:
-
https://no-id-example.identinet.io/
-
https://id-example.identinet.io/ - only a DID is avaible, no credentials.
-
https://id-plus-example.identinet.io/
-
https://broken-example.identinet.io/
The extension ..
- displays the W3C DID Document that is
associated with the visited website, i.e. the DID
did:web:<domainname>who's document is stored athttps://<domainname>/.well-known/did.json. - retrieves, verifies, and displays a publicly stored
W3C Verifiable Presentation
that might contain multiple credentials. It's expected that DID
did:web:<domainname>issued the presentation and that it's publicly available athttps://<domainname>/.well-known/presentation.json.
Requirements:
- didkit CLI
- Website that's hosted at a custom domain name, e.g. example.com
jq
Create did:web DID and issue sample credential:
- Generate a key:
didkit key generate ed25519 > key.jwk - Generate a DID
did:web:<domainname>:
DOMAINNAME="<your domainname>"
DID_WEB="did:web:${DOMAINNAME}"
KEY_ID=$(didkit key to did -k key.jwk | sed -ne 's/^did:key://p')
cat <<EOF | yq > did.json
{
"@context": [
"https://www.w3.org/ns/did/v1",
"https://w3id.org/security/suites/ed25519-2020/v1",
{
"publicKeyJwk": {
"@id": "https://w3id.org/security#publicKeyJwk",
"@type": "@json"
}
}
],
"id": "${DID_WEB}",
"verificationMethod": [
{
"id": "${DID_WEB}#${KEY_ID}",
"type": "Ed25519VerificationKey2020",
"controller": "${DID_WEB}",
"publicKeyJwk": $(yq e 'del(.d)' key.jwk)
}
],
"authentication": [
"${DID_WEB}#${KEY_ID}"
],
"assertionMethod": [
"${DID_WEB}#${KEY_ID}"
]
}
EOF- Store and publish
did.jsonin the web server's root directory at path/.well-known/did.json - Verify that the DID is publicly resolveable:
didkit did-resolve "${DID_WEB}" - Issue sample credential:
cat > credential.json <<EOF
{
"@context": ["https://www.w3.org/2018/credentials/v1", "https://w3id.org/security/suites/ed25519-2020/v1"],
"type": ["VerifiableCredential"],
"issuer": "${DID_WEB}",
"issuanceDate": "$(date -u +"%Y-%m-%dT%H:%M:%SZ")",
"credentialSubject": {
"id": "${DID_WEB}"
}
}
EOF
VERIFICATION_METHOD=$(jq -r '.assertionMethod[0]' < did.json)
didkit credential issue -t Ed25519Signature2020 -k key.jwk -p assertionMethod -v "${VERIFICATION_METHOD}" < credential.json > credential_signed.json
didkit credential verify < credential_signed.json- Verify credential:
didkit vc-verify-credential < credential_signed.json - Issue presentation:
cat > presentation.json <<EOF
{
"@context": ["https://www.w3.org/2018/credentials/v1", "https://w3id.org/security/suites/ed25519-2020/v1"],
"type": ["VerifiablePresentation"],
"holder": "${DID_WEB}",
"verifiableCredential": [
$(cat credential_signed.json)
]
}
EOF
VERIFICATION_METHOD=$(jq -r '.authentication[0]' < did.json)
didkit presentation issue -t Ed25519Signature2020 -k key.jwk -p authentication -C "${DOMAINNAME}" -d "${DOMAINNAME}" -v "${VERIFICATION_METHOD}" < presentation.json > presentation_signed.json
didkit presentation verify < presentation_signed.json- Verify presentation:
didkit vc-verify-presentation < presentation_signed.json - Store and publish
presentation_signed.jsonin the web server's root directory at path/.well-known/presentation.json
- just - Task runner like make
- nu - Versatile shell (developed on version 0.80.0)
- watchexec - File watcher
- NodeJS - (version 20)
- Google Chrome or Firefox
Dependencies for running the test websites locally:
- Install node modules:
just deps - Start extension builder:
just build-watch- Firefox build directory:
.build_firefox - Chrome build directory:
.build_chrome
- Firefox build directory:
- Install browser plugin temporarily:
- Firefox:
- Open about:debugging and select "This Firefox"
- Click on "Load Temporary Add-on..." and select
manifest.jsonin the Firefox build directory - See more detailed instructions
- Chrome:
- Open chrome://extensions/
- Click on "Load unpacked" and select the Chrome build directory
- See more detailed instructions
- Firefox:
- Start website test server:
just run-websites- Then visit id-plus.localhost:8443
- Start preview server:
just run-preview - Start development
- For better debugging, read the Firefox Extension Workshop
- Manually reload extension by clicking reload (Firefox) or update (Chrome) to include changes