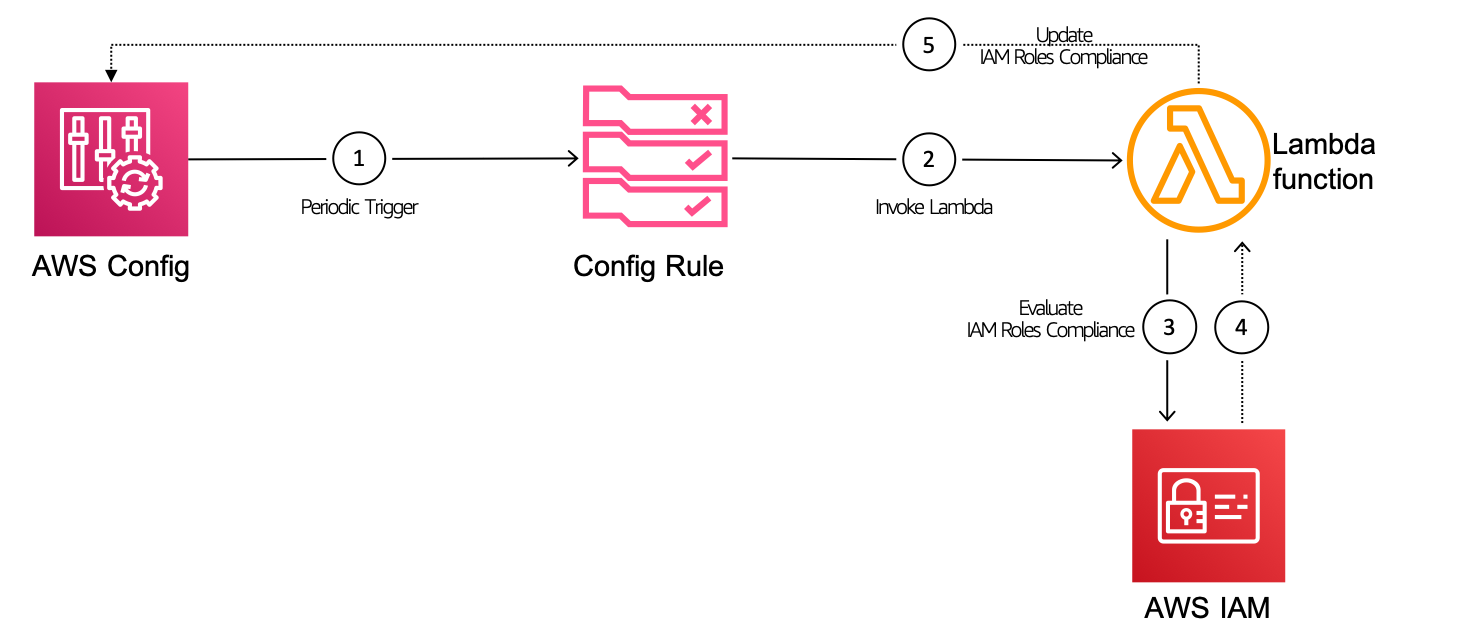
Identify IAM Roles that have not been used for x amount of time (for example, since last 30 days). We will use the role last used API and continuously monitor role activity using AWS Config. You can extend this solution to push the NON COMPLIANT information to SNS and get the necessary teams involved in the clean up operation.
Follow this article in Youtube
-
This demo, instructions, scripts and cloudformation template is designed to be run in
us-east-1. With few modifications you can try it out in other regions as well(Not covered here).- AWS CLI pre-configured - Get help here
-
Make sure you have
AWS CLIprofile configured. You should have at minimum these permissions before executing below commands# Clone the repo git clone https://github.com/miztiik/serverless-monitor-for-unused-iam-roles.git cd serverless-monitor-for-unused-iam-roles # Setup some global variables dir_name="mystique-infosec" custom_rule_name="monitor_unused_iam_roles" # If you dont have venv installed already # pip install virtualenv python3 -m venv ${dir_name} cd ${dir_name} source bin/activate pip3 install rdk # Configure AWS Profile rdk init # Lets create a LOCAL rule rdk create ${custom_rule_name} --runtime python3.7 --resource-types AWS::IAM::Role
-
Copy the file under
lambda_srcto the directory${custom_rule_name}directory that was created now. Thecustom_rule_nameand this file-name should be the SAME. -
rdk deploy ${custom_rule_name} -
- Create a new role(or ideally any pre-existing role, which has not been used for sometime is good enough)
- Wait for
AWS Configto evaluate the role and identify it as ❌Noncompliant
-
- update the lambda
MAX_UNUSED_DAYS = 30to different time period or make it a customizable variable - Integrate SNS notification
- Quarantine old roles
- Create exception list
- update the lambda
-
- Delete CloudWatch Lambda LogGroups
- Delete the stack[s] - If you want to destroy all the resources created by the stack, Execute the below command to delete the stack, or you can delete the stack from console as well
rdk undeploy ${custom_rule_name}
Buy me a coffee ☕ through Paypal, or You can reach out to get more details through here.
- Getting Started with Custom Rules
- AWS Config Rule Development Kit
- AWS Config RDK - Getting Started - Blog
- AWS Config RDK - Getting Started - Git
- Git Repo of Config Rules in Python-01
- Git Repo of Config Rules in Python-02
Level: 200