Wally is a static analysis tool for mapping function paths in code. It can be used for:
- HTTP and gRPC route detection
- Attack surface mapping.
- Automating the initial stages of threat modeling by mapping RPC and HTTP routes in Go code.
- Planning fuzzing efforts by examining the fault tolerance of call paths in code.
demo_ui.mov
Read about this graph and how to explore it in the Exploring the graph with wally server section
Because Wally is a cartographer, I like Monkey Island, and I wanted it to be called that :).
So you are analyzing a Go-based application and you need to find all HTTP and RPC routes. You can run grep or ripgrep to find specific patterns that'd point you to routes in the code but:
- You'd need to parse through a lot of unnecessary strings.
- You may end up with functions that are similar to those you are targeting but have nothing to do with HTTP or RPC.
- Grep won't solve constant values that indicate methods and route paths.
Wally currently supports the following features:
- Discover HTTP client calls and route listeners in your code by looking at each function name, signature, and package to make sure it finds the functions that you actually care about.
- Wally solves the value of compile-time constant values that may be used in the functions of interest. Wally does a pretty good job at finding constants and global variables and resolving their values for you so you don't have to chase those manually in code.
- Determine possible paths to a target function and examine the fault tolerance of such path. This is particularly useful when determining fuzzing targets or evaluating of panics discovered during fuzzing efforts.
- Wally will report the enclosing function where the function of interest is called.
- Wally will also give you all possible call paths to your functions of interest. This can be useful when analyzing monorepos where service A calls service B via a client function declared in service B's packages. This feature requires that the target code base is buildable.
- Wally will output a nice PNG graph of the call stacks for the different routes it finds.
- Determine which callpaths in code are tolerant to panics or application crashes due to bugs like nil dereferences
You are conducting an analysis of a monorepo containing multiple microservices. Often, these sorts of projects rely heavily on gRPC, which generates code for setting up gRPC routes via functions that call Invoke. Other services can then use these functions to call each other.
One of the built-in indicators in wally will allow it to find functions that call Invoke for gRPC routes, so you can get a nice list of all gRPC method calls for all your microservices. Further, with --ssa you can also map the chains of methods gRPC calls necessary to reach any given gRPC route. With wally, you can then answer:
- Can users reach service
Yhosted internally via serviceAhosted externally? - Which service would I have to initialize a call to send user input to service
X? - What functions are there between service
Aand serviceYthat might sanitize or modify the input set to serviceA?
Say you are evaluating some microservices code in a monorepo and found several functions that seemed like good fuzzing targets due to their complexity and the type of data they handle. However, before fuzzing just for fuzzing’s sake, you want to answer the following:
- What are the different ways in which this function can be reached?
- For instance, can it only be reached via a gRPC or HTTP call that eventually lands at the target function, or is there some other process (say, a task run daily by a different process) that can call it with user input (e.g., pulled from a user database) via a different call path?
- If I find a panic here, how much would it matter? That is, would this be recovered by a function in the call path with a recover() in a defer block?
<<<<<<< HEAD To learn how to answer the above questions, jump to the section on using wally to detect fault tolerance of call paths
To learn how to answer the above questions, jump to the section on using wally to detect fault tolerance of call paths
main
Wally needs a bit of hand-holding. Though it can also do a pretty good job at guessing paths, it helps a lot if you tell it the packages and functions to look for, along with the parameters that you are hoping to discover and map. So, to help Wally do the job, you can specify a configuration file in YAML that defines a set of indicators.
Tip
<<<<<<< HEAD If you are just interested in use cases of a single function, you can run Wally on single function search mode ======= If you are just interested in use cases of a single function, you can run Wally on single function search mode
main
Wally runs a number of indicators which are basically clues as to whether a function in code may be related to a gRPC or HTTP route. By default, wally has a number of built-in indicators which check for common ways to set up and call HTTP and RPC methods using standard and popular libraries. However, sometimes a codebase may have custom methods for setting up HTTP routes or for calling HTTP and RPC services. For instance, when reviewing Nomad, you can give Wally the following configuration file with Nomad-specific indicators:
indicators:
- id: nomad-1
package: "github.com/hashicorp/nomad/command/agent"
type: ""
function: "forward"
indicatorType: 1
receiverType: "ACL" # optional
params:
- name: "method"
- id: nomad-2
package: "github.com/hashicorp/nomad/nomad"
type: ""
function: "RPC"
indicatorType: 1
params: # optional
- name: "method" # optional
- id: nomad-3
package: "github.com/hashicorp/nomad/api"
type: "s"
function: "query"
indicatorType: 1
params:
pos: 0 # optioncalNote that you can specify the parameter that you want Wally to attempt to solve the value to. If you don't know the name of the parameter (per the function signature), you can give it the position in the signature. You can then use the --config or -c flag along with the path to the configuration file.
A good test project to run it against is nomad because it has a lot of routes set up and called all over the place. I suggest the following:
- Clone this project.
- In a separate directory, clone nomad.
- Build this project by running
go build. - Navigate to the root of the directory where you cloned nomad (
path/to/nomad). - Create a configuration file named
.wally.yamlwith the content shown in the previous section of this README, and save it to the root of the nomad directory. - Run the following command from the nomad root:
$ <path/to/wally/wally> map -p ./... -vvvWally can be easily run using Docker. Follow these steps:
-
Clone this project.
-
In a separate directory, clone nomad.
-
Build the Docker Image:
docker build -t go-wally . -
Run an interactive shell inside the Docker container
docker run -it go-wally /bin/sh
-
Run Wally with Docker, specifying the necessary parameters, such as the project path, configuration file, etc.:
docker run -w /<PROJECT>/ -v $(pwd):/<PROJECT> go-wally map /<PROJECT>/... -vvv
Adjust the flags (-p, -vvv, etc.) as needed for your use case.
-
If you have a specific configuration file (e.g., .wally.yaml), you can mount it into the container:
docker run -w </PROJECT> -v $(pwd):</PROJECT> -v </PATH/TO/.wally.yaml>:</PROJECT>/.wally.yaml go-wally map -c .wally.yaml -p ./... --max-paths 50 -vvv
This will run Wally within a Docker container, analyzing your Go code for HTTP and RPC routes based on the specified indicators and configurations.
-
Optionally, if you encountered any issues during the Docker build, you can revisit the interactive shell inside the container for further debugging.
-
After running Wally, you can check the results and the generated PNG or XDOT graph output, as explained in the README.
Wally should work even if you are not able to build the project you want to run it against. However, if you can build the project without any issues, you can run Wally using the --ssa flag, at which point Wally will be able to do the following:
- Solve the enclosing function more effectively using SSA.
- Output all possible call paths to the functions where the routes are defined and/or called.
When using the --ssa flag you can expect output like this:
===========MATCH===============
ID: 14554c2a-41ee-4634-831d-6fc49c70c80d
Indicator ID: 1
Package: github.com/hashicorp/cronexpr
Function: Parse
Params:
Enclosed by: (*github.com/hashicorp/nomad/nomad/structs.PeriodicConfig).Validate
Position /Users/hex0punk/Tests/nomad/nomad/structs/structs.go:5638
Possible Paths: 1
Path 1 (filter limited):
[Validate] nomad/structs/structs.go:5614:26 --->
===========MATCH===============
ID: 6a876579-6b72-4501-af5b-5028c84a1c77
Indicator ID: 1
Package: github.com/hashicorp/cronexpr
Function: Parse
Params:
Enclosed by: (*github.com/hashicorp/nomad/nomad/structs.PeriodicConfig).Validate
Position /Users/hex0punk/Tests/nomad/nomad/structs/structs.go:5644
Possible Paths: 1
Path 1 (filter limited):
[Validate] nomad/structs/structs.go:5614:26 --->
===========MATCH===============
ID: eeaa94b1-28a8-41b8-a1e3-7a0d665a1e4d
Indicator ID: 1
Package: github.com/hashicorp/cronexpr
Function: Parse
Params:
Enclosed by: github.com/hashicorp/nomad/nomad/structs.CronParseNext
Position /Users/hex0punk/Tests/nomad/nomad/structs/structs.go:5677
Possible Paths: 28
Path 1 (RECOVERABLE):
nomad.[Plan] nomad/job_endpoint.go:1949:57 --->
structs.[Next] nomad/structs/structs.go:5693:24 --->
[CronParseNext] (recoverable) nomad/structs/structs.go:5670:6 --->
Path 2 (RECOVERABLE):
nomad.[Plan] nomad/job_endpoint.go:1949:57 --->
structs.[Next] nomad/structs/structs.go:5699:27 --->
[CronParseNext] (recoverable) nomad/structs/structs.go:5670:6 --->
Path 3 (node limited) (RECOVERABLE):
nomad.[leaderLoop] nomad/leader.go:247:34 --->
nomad.[establishLeadership] nomad/leader.go:412:33 --->
nomad.[SetEnabled] nomad/periodic.go:167:3 --->
nomad.[run] nomad/periodic.go:332:14 --->
nomad.[dispatch] nomad/periodic.go:342:38 --->
structs.[Next] nomad/structs/structs.go:5693:24 --->
[CronParseNext] (recoverable) nomad/structs/structs.go:5670:6 --->When running Wally in SSA mode against large codebases wally might run get lost in external libraries used by the target code. In most cases, you'd want to filter analysis to only the module you want to target. For instance, when using wally to find HTTP and gRPC routes in nomad, you'd want to type the command below.
$ wally map -p ./... --ssa -vvv -f "github.com/hashicorp/nomad/" --max-paths 50Where -f defines a filter for the call stack search function. If you don't do this, wally may end up getting stuck in some loop as it encounters recursive calls or very lengthy paths in scary dependency forests.
Important
If using -f is not enough, and you are seeing Wally taking a very long time in the "solving call paths" step, Wally may have encountered some sort of recursive call. In that case, you can use --max-paths and an integer to limit the number of recursive calls Wally makes when mapping call paths (50 tends to be a good number). This will limit the paths you see in the output, but using a high enough number should still return helpful paths. Experiment with --max-paths, --max-funcs, -f, or all three to get the results you need or expect.
Wally has the following options to limit the search. These options can help refine the results, but can be used for various experimental uses of Wally as well.
-f: filter string which tells wally the path prefix for packages that you are interested in. Typically you'd want to enter the full path for the Go module you are targetting, unless you are interested in paths that may reach to standard Go functions (i.e.runtime) via closures, etc.max-paths: maximum number of paths per match which wally will collect. This is helpful when the generate callgraphs report cyclic functionsmax-funcs: maxium number of functions or nodes reported per paths. We recommed you use this if you run wally without a filter using-fskip-closures: The default algorithm tries to be complete by returning possible ways in which closures can be used in the program, even if the path is not realistic given the program you are analyzing. This option reduces inaccurate paths by avoiding invalid paths from closures and instead skipping the enclosed function. Note: This option is only supported by the BFS/default search algorithm.limiter-mode: See explanation below
At its core, Wally uses various algorithms available via the golang.org/x/tools/go/callgraph library. These algorithms can generate spurious results at times which results in functions that go past main at the top of callpaths. To wrangle some of these sort of results, we perform a basic set of logical checks to eliminate or limit incorrect call path functions/nodes. You can specify how the limiting is done using the --limiter flag, followed by one of the modes levels below:
0(none): Wally will construct call paths even past main if reported by the chosentools/go/callgraphalgorithm.1(normal): This is the default mode and the preferred mode when you are interested in confirming callpath fault tolerance. Wally will stop constructing call paths once it sees a call to either:- A function node A originating in the
mainfunction, followed by a call to node B not in themainfunction belonging to the same package - A function node A originating in the
mainpackage followed by a call to node B inside themainfunction of a different package - A function node A originating in the
mainpacckage followed by a function/node B not in the same package unless function/node A is a closure.
- A function node A originating in the
2(high): Wally will stop once it sees a function nodeAin themainpackage followed by a call to B in any other package other than themainpackage where A was found.3(strict): Same asskip-closuresplus all the restrictions above. Note: This option is only supported by the BFS/default search algorithm.
Rather than using a yaml configuration file, you can use wally map search for mapping paths to individual functions. For instance:
$ wally map search -p ./... --func Parse --pkg github.com/hashicorp/cronexpr --max-funcs 7 --max-paths 50 -f github.com/hashicorp/ -vvvThe options above map to the following
-p ./...: Target code is in the current directory--func Parse: We are interested only in theParsefunction--pkg github.com/hashicorp/cronexpr: Of packagegithub.com/hashicorp/cronexpr--max-funcs 7: We only want up to 7 functions per path--max-paths 50: Limit the paths to 50-vvv: Very, very verbose-f github.com/hashicorp/: This tells Wally that we are only interested in paths within packages that start withgithub.com/hashicorp/. This avoids getting paths that reach beyond the scope we are interested in. Otherwise, we'd get nodes in standard Go libraries, etc.
Wally can now tell you which paths to a target function will recover in case of a panic triggered by that target function. A detailed explanation can be found here.
<<<<<<< HEAD Using the single function search mode, we can determine which call paths to a given target function would recover in response to a panic
Using the single function search mode, we can determine which call paths to a given target function would recover in response to a panic
main
$ wally map search -p ./... --func PrintOrPanic --pkg github.com/hex0punk/wally/sampleapp/printer -f github.com/hex0punk/wally/sampleapp -vvv
===========MATCH===============
ID: f9241d61-d19e-4847-b458-4f53a86ed5c5
Indicator ID: 1
Package: github.com/hex0punk/wally/samppleapp/printer
Function: PrintOrPanic
Params:
Enclosed by: github.com/hex0punk/wally/samppleapp.printCharSafe$1
Position /Users/alexuseche/Projects/wally/sampleapp/main.go:17
Possible Paths: 1
Path 1 (RECOVERABLE):
main.[main] main.go:11:15 --->
main.[`printCharSafe`] main.go:16:16 --->
safe.[RunSafely] (recoverable) safe/safe.go:12:4 --->
main.[printCharSafe$1] main.go:16:17 --->
===========MATCH===============
ID: eb72e837-31ba-4945-97b1-9432900ae3f9
Indicator ID: 1
Package: github.com/hex0punk/wally/samppleapp/printer
Function: PrintOrPanic
Params:
Enclosed by: github.com/hex0punk/wally/samppleapp.printChar
Position /Users/alexuseche/Projects/wally/sampleapp/main.go:22
Possible Paths: 1
Path 1:
main.[main] main.go:12:11 --->
main.[printChar] main.go:21:6 --->
Total Results: 2Paths marked with (RECOVERABLE) will be fault tolerant. The function containing the recover() block is marked in the results as (recoverable)
To make visualization of callpaths easier, wally can lunch a server on localhost when via a couple methods:
After an analysis by passing the --server flag to the map command. For instance:
$ wally map -p ./... -c .wally.yaml --ssa -f "github.com/hashicorp/nomad" --serverOr, using the server subcommand and passing a wally json file:
$ wally server -p ./nomad-wally.json -P 1984Next, open a browser and head to the address in the output.
Graphs are generated using the cosmograph library. Each node represents a function call in code. The colors are not random. Each color has a a different purpose to help you make good use of the graph.
Finding node. This is a node discovered via wally indicators. Every finding node is the end of a path
This node is the root of a path to a finding node.
Intermediate node between a root and a finding node.
This node servers both as the root node to a path and an intermediary node for one or more paths
Clicking on any node will highlight all possible paths to that node. Click anywhere other than a node to exist the path selection view.
Clicking on any finding node will populate the section on the left with information about the finding.
Start typing on the search bar on the left to find a node by name.
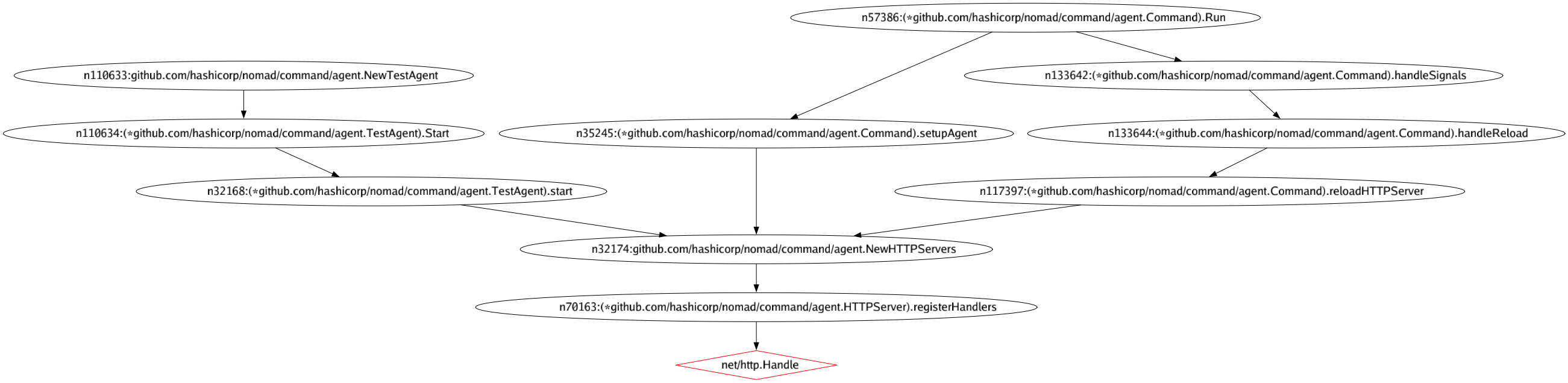
When using the --ssa flag, you can also use -g or --graph to indicate a path for a PNG or XDOT containing a Graphviz-based graph of the call stacks. For example, running:
$ wally map -p ./... --ssa -vvv -f "github.com/hashicorp/nomad/" -g ./mygraph.pngFrom nomad/command/agent will output this graph:
Specifying a filename with a .xdot extension will create an xdot file instead.
- You can specify which algorithm to use for the intial callgraph generation using
--callgraph-alg. This is the algorithm used by thegolang.org/x/tools/function. Options includecha(default),rta, andvta. - By default, wally uses a breathd search first algorithm to map all paths. You can instead use depth first search using
--search-alg dfs - Whenever Wally sees it reaches a
mainfunction, it will stop going further back in the tree to avoid reporting inaccurate paths. If you wish, you can override this by using the--continue-after-mainflag, allowing you to see some interesting but less likely paths.
At its core, Wally is, essentially, a function mapper. You can define functions in configuration files that have nothing to do with HTTP or RPC routes to obtain the same information that is described here.
You can add logging statements as needed during development in any function with a Navigator receiver like this: n.Logger.Debug("your message", "a key", "a value").
At the moment, wally will often give you duplicate stack paths, where you'd notice a path of, say, A->B->C is repeated a couple of times or more. Based on my testing and debugging this is a drawback of the cha algorithm from Go's callgraph package, which wally uses for the call stack path functionality. I am experimenting with other available algorithms in go/callgraph/ to determine what the best option to minimize such issues (while getting accurate call stacks) could be and will update wally's code accordingly. In the case that we stick to the cha algorithm, I will write code to filter duplicates.
This is often caused by issues in the target code base. Make sure you are able to build the target codebase. You may want to run go build and fix any issues reported by the compiler. Then, run wally again against it.
See the section on Filtering call path analysis
Viewing the description of each command
$ wally map --help$ wally map search --help$ wally map --helpFeel free to open issues and send PRs. Please.