Provides a lab environment for demonstrating governance and compliance for a Java application deployed to the VMware Tanzu Platform. The lab builds upon the great work my colleauges have done on TKG Lab and on creating an end-to-end demonstration of the developer and operator experience showcasing Tanzu.
The Lab uses the Spring Pet Clinic application as the codebase for the demonstration.
This lab is designed to explore and demonstrate the governance points in the Tanzu portfolio. It incorporates some additional capabilities, like static and dynamic application scanning, to highlight the full context in which the Tanzu capabilities operate and establish a real-life layering of controls.
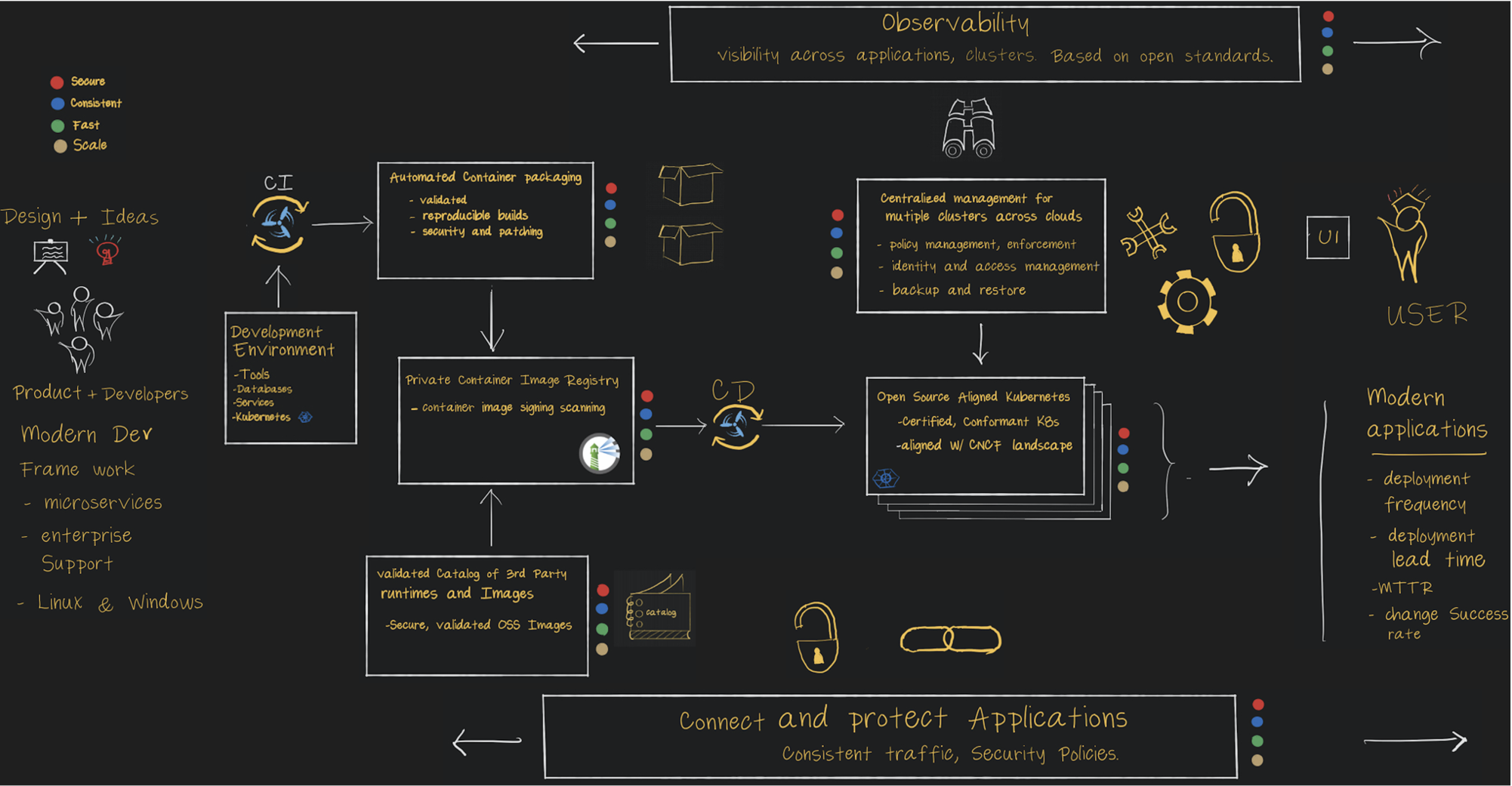
The high-level architecture of the Tanzu portfolio and its capabilities is shown in the Tanzu Overview Whiteboard
many Tanzu components provide automated governance controls that increase security, consistency, and resiliency to the process you use to build, run, and manage software workloads.
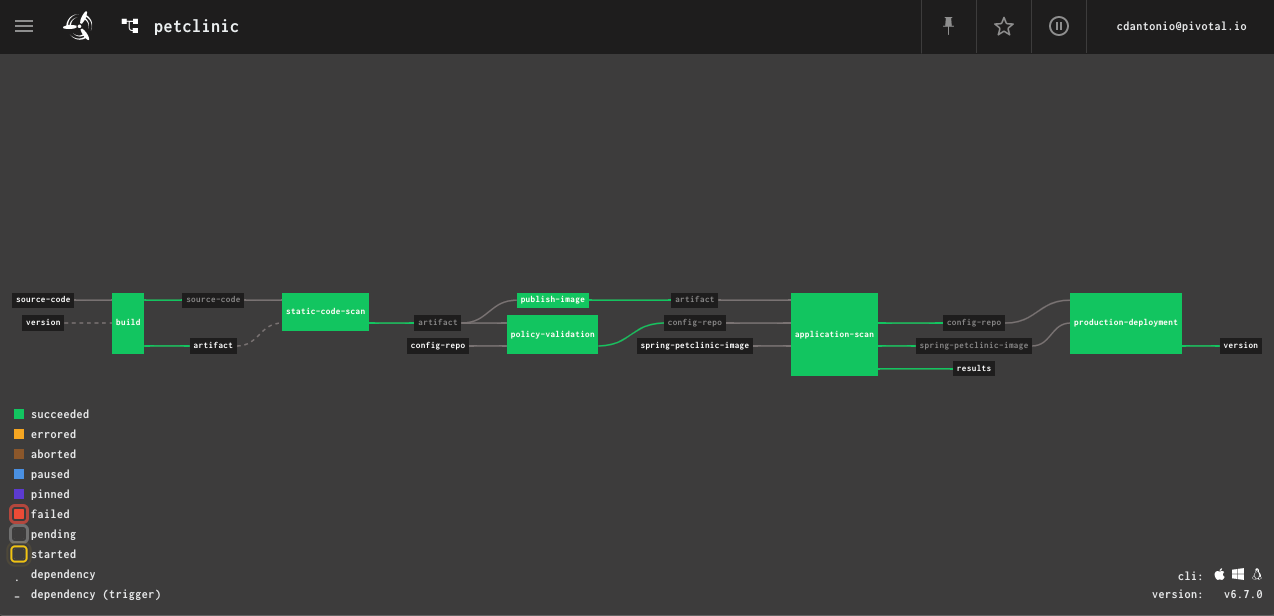
VMware's open source Concourse orchestrates the CI/CD pipeline that builds, validates, and deploys the application. The pipeline uses Tanzu Build Service and it's cloud-native buildpacks to assure the container is build with a trusted version of the JDK and the underlying operating system.
The pipeline uses additional open source tools to assure that both the application and the Kubernetes objects that deploy it are secure. Sonarqube scans the Java code before it passing the JAR file to TBS to containerize. Before deploying the container, Conftest checks the Kubernetes manifests to assure they are compliant with the workload polices we'll later enforce at runtime.
After building the images and confirming tha the Kubernetes manifests pass muster, the pipeline does a staging deployment and runs the open source OWASP ZAP to do a quick scan of the running application. This is not a deep penetration test but gives a quick analysis of whether the application is safe as deployed.
Lastly, the code is deployed to TKG. The pipeline ends there, but other controls are at play both as part of the deployment and as part of the ongoing management of the workload.
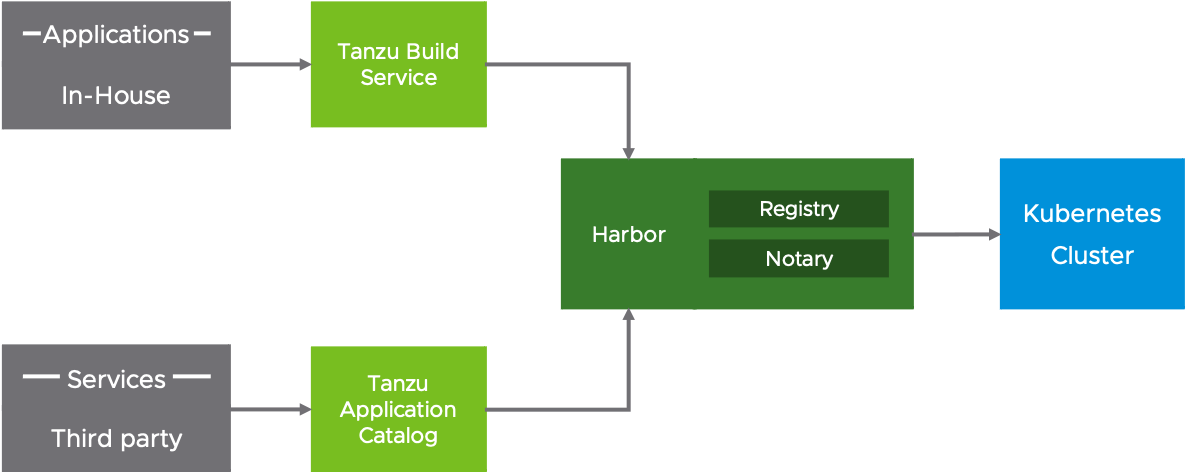
Using Tanzu Build Service we assure that our in-house workloads are containerized with a set of trusted dependencies. Our workload and the services supporting our pipeling depend on open source databases to store their data. We use images and Helm charts from Tanzu Application Catalog to assure we can trust these dependencies.
Part of setting up the lab is replicating trusted images from TAC into our private registry to comply with our policies.
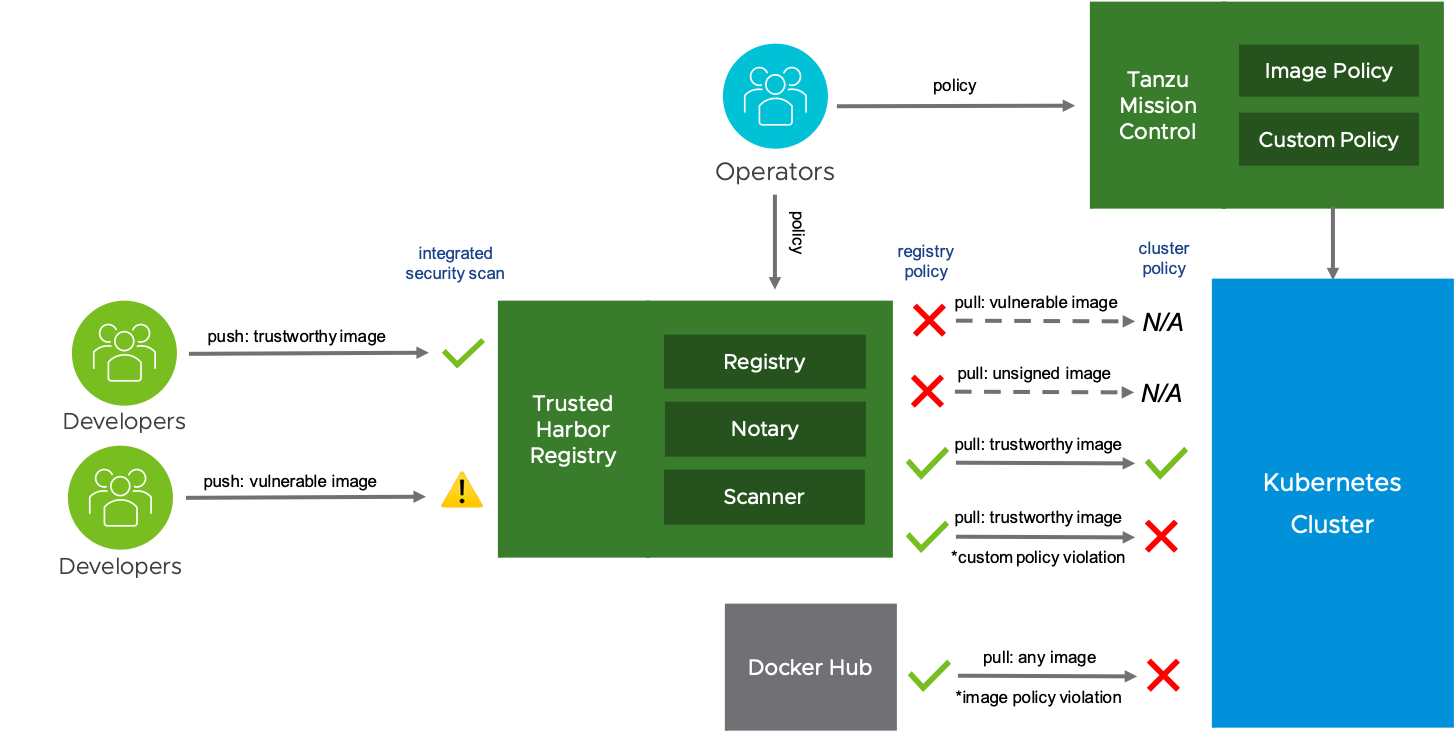
To assure that our running workloads are compliant and secure, we use the open source Harbor registry (sponsored primarily by VMware) together with Tanzu Mission Control.
Harbor scans our workloads to help us to understand the CVEs that are present in each container workload. It also prevents workloads with CVEs above a certain level from executing. Workloads are cleared by Harbor are subject to additional policy enforced by TMC.
TMC ensures that our workload namespaces only allow workloads pulled from the Harbor registry to run. It also validates the deployment and ingress objects against policies that assure that a minimum number of replicas run and that HTTPS is used to access the code.
See the step by step instructions on how to configure the lab.