Swift implementation of classic cryptographic key exchange method.
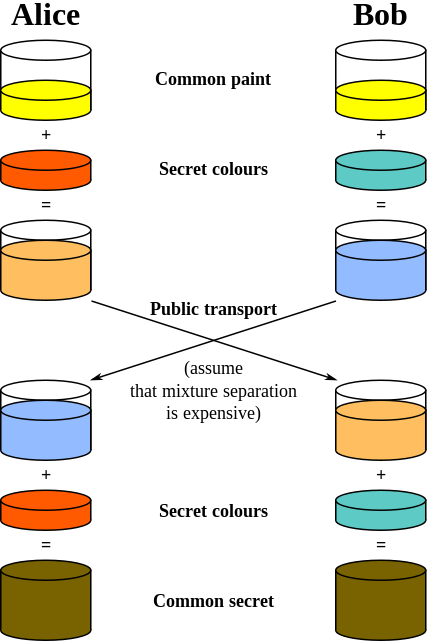
Diffie-Hellman Key Exchange allow parties to jointly establish a secure private key without sharing it in any way (Forward secrecy) and then use it for a symmetric key cipher.
-
Both parties agree on a common component, which consists of two natural numbers p (modulus) and g (base). They can be completely random to make this work, but in order to make the process significantly harder to break, p should be a prime and g should be primitive root modulo of p. Check
DHParameters.swiftfor more info. -
Then both parties generate random private keys and then compute public keys which they share with each other. Public keys are computed as follows publicKey = g^privateKey mod p
-
Afterward, both parties can compute common secret key using own private key and peer's public key. They can do it using the following formula secretKey = peerPublicKey^ownPrivateKey mod p
Underlying math:
(g^a mod p)^b mod p = g^ab mod p
(g^b mod p)^a mod p = g^ba mod p -
Now both parties can communicate using symmetric cryptography using a jointly established private key.
This protocol is considered secure (check disclaimer), because it's relatively hard for eavesdroppers to compute a common secret key knowing only public keys if p is big enough.
Don't use it in a production environment. Generated keys are very small (Int64) thus making them easily breakable. Use already generated RFC primes, but even them may not be strong enough.
Greg (Grzegorz) Surma