How to use Amazon GuardDuty and AWS Web Application Firewall to Automatically Block Suspicious Hosts
This solution uses Amazon GuardDuty to automatically update AWS Web Application Firewall Access Control Lists (WAF ACLs) and VPC Network Access Control Lists (NACLs) in response to GuardDuty findings. After GuardDuty detects a suspicious activity, the solution updates these resources to block communication from the suspicious host while additional investigation and remediation may be performed.
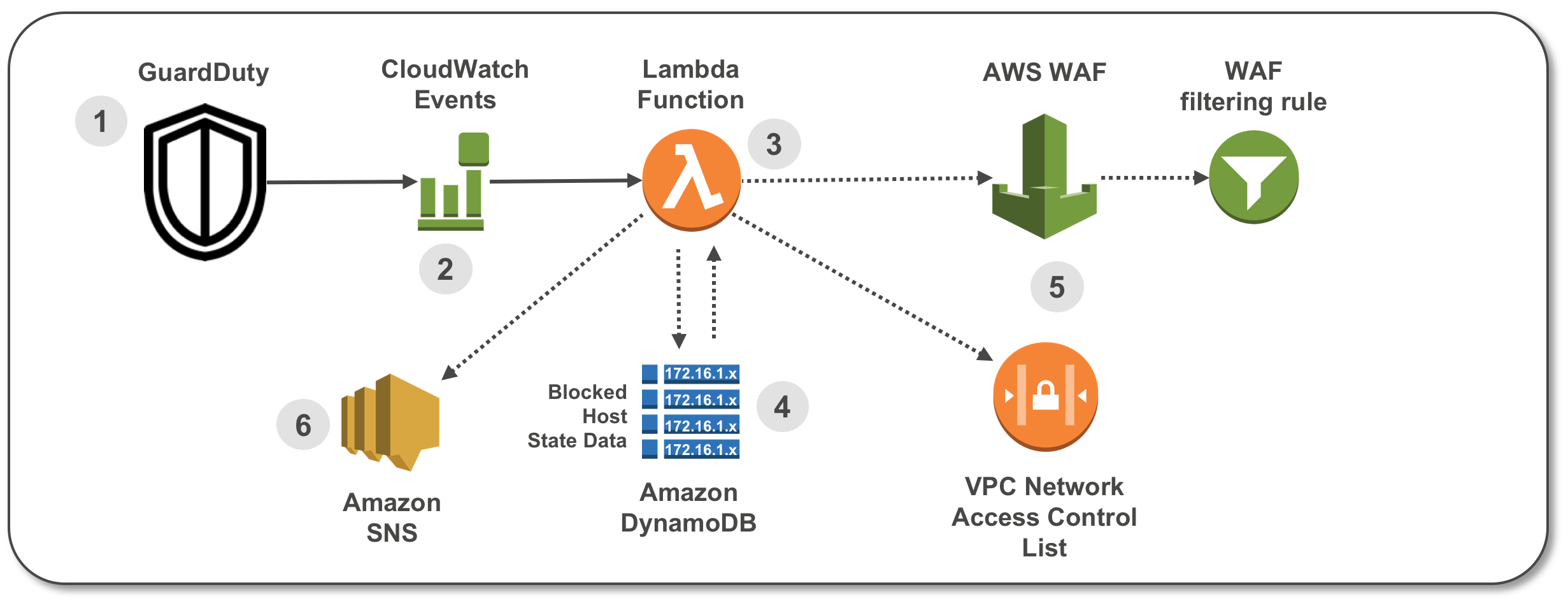
Here’s how the solution works, as shown in the diagram:
- A GuardDuty Finding is raised with suspected malicious activity.
- A CloudWatch Event is configured to filter for GuardDuty Finding type.
- A Lambda function is invoked by the CloudWatch Event and parses the GuardDuty Finding.
- State data for blocked hosts is stored in DynamoDB table. The Lambda function checks the state table for existing host entry.
- The Lambda function creates a filter in a WAF ACL and in a VPC NACL. Older entries are aged out to create a “sliding window” of blocked hosts.
- A notification email is sent via Amazon Simple Notification Service (SNS).
This sample code is made available under a modified MIT license. See the LICENSE file.