This repository template helps you create gitlab runner on your aws account via AWS CDK one line.
- VPC
- Public Subnet (2)
- EC2 (1 T3.micro)
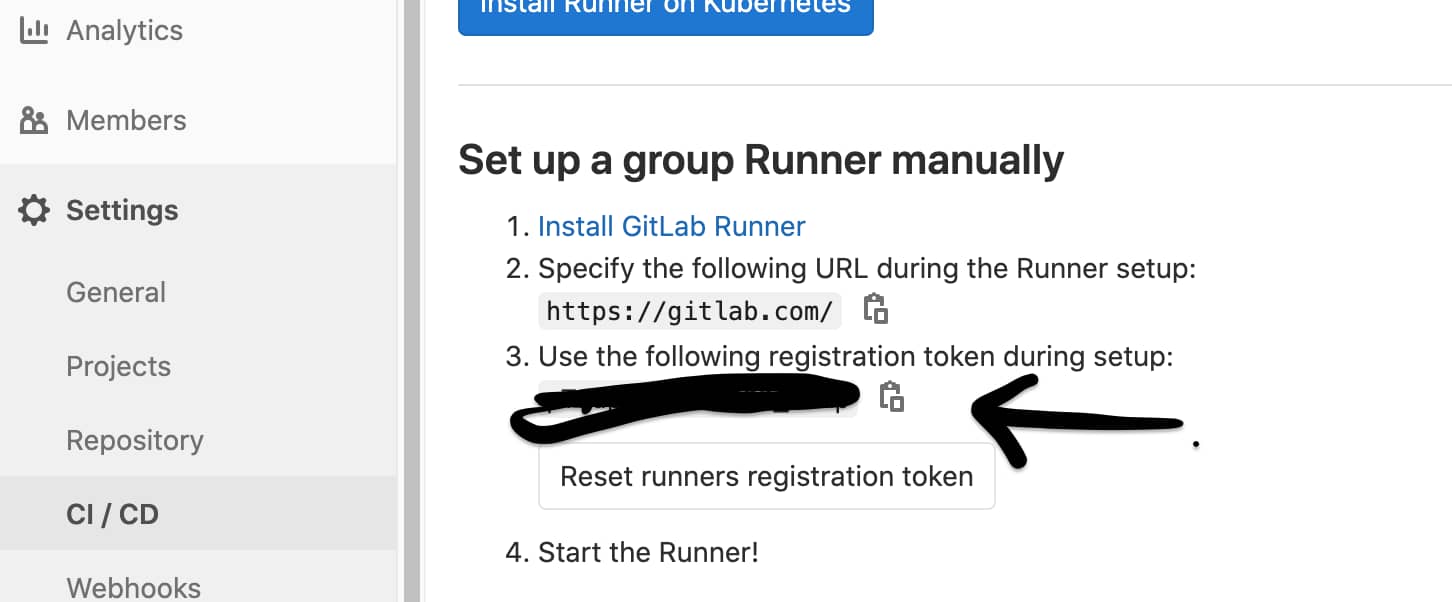
Project > Settings > CI/CD > Runners
Replace your gitlab runner token in $GITLABTOKEN
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
// If want change instance type to t3.large .
new GitlabContainerRunner(this, 'runner-instance', { gitlabtoken: '$GITLABTOKEN', ec2type:'t3.large' });
// OR
// Just create a gitlab runner , by default instance type is t3.micro .
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
new GitlabContainerRunner(this, 'runner-instance', { gitlabtoken: '$GITLABTOKEN' });})If you want change what you want tag name .
// If you want change what your self Gitlab Server Url .
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
new GitlabContainerRunner(this, 'runner-instance-change-tag', {
gitlabtoken: '$GITLABTOKEN',
gitlaburl: 'https://gitlab.my.com/',
});If you want change what you want tag name .
// If you want change what you want tag name .
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
new GitlabContainerRunner(this, 'runner-instance-change-tag', {
gitlabtoken: '$GITLABTOKEN',
tags: ['aa', 'bb', 'cc'],
});If you want add runner other IAM Policy like s3-readonly-access.
// If you want add runner other IAM Policy like s3-readonly-access.
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
import { ManagedPolicy } from '@aws-cdk/aws-iam';
const runner = new GitlabContainerRunner(this, 'runner-instance-add-policy', {
gitlabtoken: '$GITLABTOKEN',
tags: ['aa', 'bb', 'cc'],
});
runner.runnerRole.addManagedPolicy(
ManagedPolicy.fromAwsManagedPolicyName('AmazonS3ReadOnlyAccess'),
);If you want add runner other SG Ingress .
// If you want add runner other SG Ingress .
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
import { Port, Peer } from '@aws-cdk/aws-ec2';
const runner = new GitlabContainerRunner(this, 'runner-add-SG-ingress', {
gitlabtoken: 'GITLABTOKEN',
tags: ['aa', 'bb', 'cc'],
});
// you can add ingress in your runner SG .
runner.defaultRunnerSG.connections.allowFrom(
Peer.ipv4('0.0.0.0/0'),
Port.tcp(80),
);2020/06/27 , you can use your self exist VPC or new VPC , but please check your
vpc public SubnetAuto-assign public IPv4 address must be Yes ,orvpc private Subnetroute table associatednat gateway.
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
import { Port, Peer, Vpc, SubnetType } from '@aws-cdk/aws-ec2';
import { ManagedPolicy } from '@aws-cdk/aws-iam';
const newvpc = new Vpc(stack, 'VPC', {
cidr: '10.1.0.0/16',
maxAzs: 2,
subnetConfiguration: [
{
cidrMask: 26,
name: 'RunnerVPC',
subnetType: SubnetType.PUBLIC,
},
],
natGateways: 0,
});
const runner = new GitlabContainerRunner(this, 'testing', {
gitlabtoken: '$GITLABTOKEN',
ec2type: 't3.small',
selfvpc: newvpc,
});2020/06/27 , you can use your self exist role assign to runner
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
import { Port, Peer } from '@aws-cdk/aws-ec2';
import { ManagedPolicy, Role, ServicePrincipal } from '@aws-cdk/aws-iam';
const role = new Role(this, 'runner-role', {
assumedBy: new ServicePrincipal('ec2.amazonaws.com'),
description: 'For Gitlab EC2 Runner Test Role',
roleName: 'TestRole',
});
const runner = new GitlabContainerRunner(stack, 'testing', {
gitlabtoken: '$GITLAB_TOKEN',
ec2iamrole: role,
});
runner.runnerRole.addManagedPolicy(
ManagedPolicy.fromAwsManagedPolicyName('AmazonS3ReadOnlyAccess'),
);2020/08/22 , you can change you want ebs size.
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
new GitlabContainerRunner(stack, 'testing', {
gitlabtoken: '$GITLAB_TOKEN',
ebsSize: 50,
});2020/08/27 , you can use spotfleet instance be your gitlab runner, after create spotfleet instance will auto output instance id .thank @pahud again ~~~
import { GitlabContainerRunner, BlockDuration } from 'cdk-gitlab-runner';
const runner = new GitlabContainerRunner(stack, 'testing', {
gitlabtoken: 'GITLAB_TOKEN',
ec2type: 't3.large',
blockDuration: BlockDuration.ONE_HOUR,
spotFleet: true,
});
// configure the expiration after 1 hours
runner.expireAfter(Duration.hours(1));2020/11/19, you setting job runtime bind host volumes. see more https://docs.gitlab.com/runner/configuration/advanced-configuration.html#the-runnersdocker-section
import { GitlabContainerRunner, BlockDuration } from 'cdk-gitlab-runner';
const runner = new GitlabContainerRunner(stack, 'testing', {
gitlabtoken: 'GITLAB_TOKEN',
ec2type: 't3.large',
dockerVolumes: [
{
hostPath: '/tmp/cahce',
containerPath: '/tmp/cahce',
},
],
});2020/11/19, support runner auto unregister runner when cdk app destroy.
About change instance type
import { InstanceType, InstanceClass, InstanceSize } from '@aws-cdk/aws-ec2';
import { GitlabContainerRunner } from 'cdk-gitlab-runner';
// If want change instance type to t3.large .
new GitlabContainerRunner(this, 'runner-instance', {
gitlabtoken: '$GITLABTOKEN',
ec2type: InstanceType.of(InstanceClass.T3, InstanceSize.LARGE),
});import { GitlabContainerRunner } from 'cdk-gitlab-runner';
// If want change instance type to t3.large .
new GitlabContainerRunner(this, 'runner-instance', {
gitlabtoken: '$GITLABTOKEN',
ec2type: 't3.large',
});dockerjob:
image: docker:18.09-dind
variables:
tags:
- runner
- awscdk
- gitlab
variables:
DOCKER_TLS_CERTDIR: ""
before_script:
- docker info
script:
- docker info;
- echo 'test 123';
- echo 'hello world 1228'# become to root
sudo -i
# list runner container .
root# docker ps -a
# modify gitlab-runner/config.toml
root# cd /home/ec2-user/.gitlab-runner/ && ls
config.toml