Batch create CSRs and batch merge signed certs with keys to create PKCS12 files.
·
Report Bug
·
Request Feature
Table of Contents
This project was initially created to reduce clicking on large Cisco Secure Network Analytics (formerly Stealthwatch) deployments, but it can be used to batch create CSR's and create PKCS12 certificates for import for any purpose.
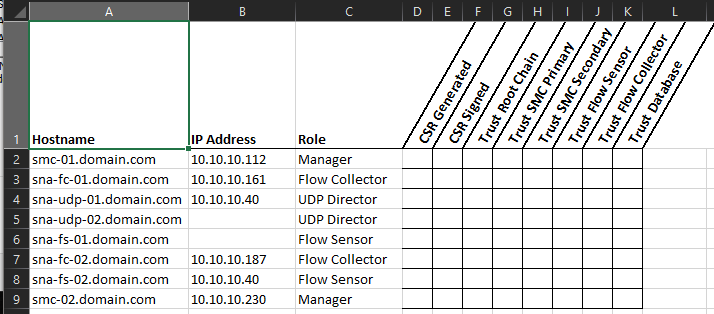
Given it was originally created for a Cisco SNA deployment, the source .xlsx file included also includes a checklist to track activities completed with each SNA cluster member. Feel free to modify any column other than Column A or B. SNA's identity certs are generated with a SAN field containing the DNS name of the appliance and a SAN field with the IP Address of the appliance.
The script will read the hostnames from Column A and create a directory for each host where the certificate keys and CSRs will be kept.
When you receive your signed Base 64 certificates, place them each in their respective directory and run pfxcreator.py to create your pfx files. You must have a valid Base 64 PEM as well as your key file in the hosts directory for this to work. The pfx files will be created in their respective directories.
Ensure your workstation has OpenSSL installed and up-to-date.
Clone the repo. Install any required libraries you may be missing.
Dependencies:
- pyOpenSSL==22.0.0
- openpyxl==3.0.9
- Clone the repo
git clone https://github.com/gobblegoob/CSRCreator.git
- Install the requirements
pip install -r requirements.txtIn brief:
- Add your hostnames and FQDN plus server IP addresses to the SNA Certificate Checklist.xlsx file
- Run certmanager.py
- Ensure your certificate attributres are correct either from within the app, or editing the script to change the default settings
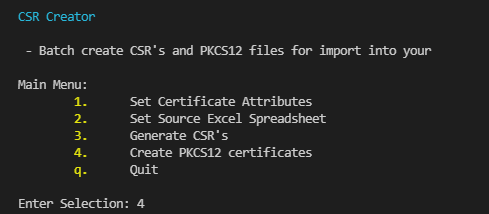
- Generate CSRs by selecting option 3. You can leave the script running or close it when done
- A directory is created for each server. Each directory contains a key file and a CSR.
- Have your CA sign your CSRs and place the signed certificate in its corresponding directory
- Run certmanager.py and select option 4 to create your pfx files
- Import your pfx files - Default passphrase is password123
Modify the included xlsx file SNA Certificate Checklist.xlsx. Fill out column A with your hostnames and column B with your IP addresses. This will populate the certificate CN and SAN Fields.
Launch certmanager.py. You will be granted with a text based interface that will guide you through the process.
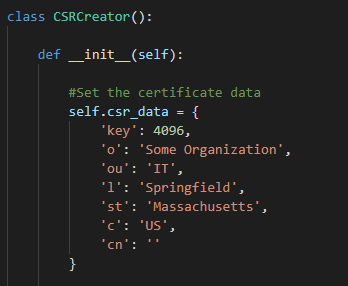
You can set certificate attributes. If you wish to modify the default set, edit the csr_data dictionary in csrcreator.py. You also can't directly edit the CN or Key attributes. The key is defaulted to 4096. The source excel spreadsheet is simply an excel spreadsheet used as a checklist for certificate activities on a distributed Cisco Secure Network Analytics deployment. It can be modified for your use as long as the hostnames are in column A. Row 1 is a header and will not be read into the program. Will parse your source list of hostnames and create a directory for each host. Each directory will hold the CSR file and the Key file. Important! ensure that the signed PEM files are Base 64 encoded. Note: The script will create a json file that will store path and hostname data to account for the time taken to get the certificates signed. Please don't delete this file till you no longer need it. It is saved in the root path for the application and will be named csr_list_[DATE].jsonA note about certificate EKUs
- Ensure you're using the correct EKU's. Cisco SNA requires Client and Server EKUs.
The CSR's will be created with the following fields:
- CN: Appliance FQDN
- SAN: Appliance FQDN
- SAN: Appliance IP address
You will receive output that will let you know if there are any errors.
You are now ready to install the certificiates where needed.
I'm not sure what this does, but I hope it's not dangerous.There are a couple defaults you might want to edit.
The certificate attributes in the CN field will need to be updated. If you wish to alter the defaults so you don't have to change them every time you launch the application, you can do that by modifying the following:
csrcreator.pyThe csr_data dictionary in the __init__() function hosts the default data. Modify as needed.
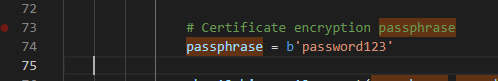
The pkcs12 file you get signed will be encrypted with a passphrase. The default is password123. If you wish to change the default passphrase, you an do so by modifying the following:
pfxcreator.pyThe passphrase variable in the generate_pkcs12() function. You can search for it. Note, it must be in bits.
- Use Excel checklist to import host list
- Include a script for automatically signing CSR's from AD based Certificate Authority
- Allow a user to set their own source spreadsheet
- Allow for the addition of SAN fields and other attributes in CSR
- GUI
- Improved error handling
- Support for Elliptic Curve Certificates
See the open issues for a full list of proposed features (and known issues).
Distributed under the MIT License. See LICENSE.txt for more information.
Project Link: https://github.com/gobblegoob/CSRCreator