This repository contains demo applications that demonstrates how to integrate the following OAuth 2.0 flows into your Spring Boot Application:
- Authorization Code Flow
- Client Credentials Flow
SPA Demo to show Authorization Code Flow with PKCE can be found here
- JDK 15
- Download and install Lombok plugin
- Enable Annotation Processors
- Go to Setting > Build, Execution, Deployment > Compiler > Annotation Processors
- Check Enable annotation processing
Gradle is used as a build automation tool. Several major IDEs allow you to import Gradle builds and interact with them. IntelliJ IDEA supports a fully-functional integration with Gradle.
Docker is a software platform that allows us to build, test, and deploy applications quickly.
$ gradlew clean build
This project contains several modules, here are the main ones you to focus on and run:
| MODULE | DESCRIPTION |
|---|---|
| hello-okta-api | REST API Backend Server. Exposes domain API over REST. Secured by Okta. |
| hello-okta-bff | BFF (Backend for Frontend) Server. Aggregates data from downstream services (for example hello-okta-api) providing API tailored to Front-end (SPA) needs. Secured by Okta. |
| hello-okta-api-client | REST API Server Client. |
Other modules contains shared source code.
- API module:
$ gradlew hello-okta-api:dependencies > api-dependencies.txt
- BFF module:
$ gradlew hello-okta-bff:dependencies > bff-dependencies.txt
There are 2 runnable modules in this project:
Each of them contains instructions how to Run Application on localhost in README.md file.
Note, both of them should be up and running to see the demo.
- Spring Boot : Application framework
- Spring Cloud Sleuth : Distributed tracing tool for Spring Cloud
- Lombok : Utility library for Java language
- GraphQL : API query runtime
- Feign : Declarative REST Client
- WireMock : Simulator for HTTP-based APIs
- Springdoc OpenAPI 3.0 : Spring Boot RESTful API Documentation
- Checkstyle
- Helm : Package manager for Kubernetes
Head on over to developer.okta.com to create a free-forever developer account. Look for the email to complete the initialization of your Okta org.
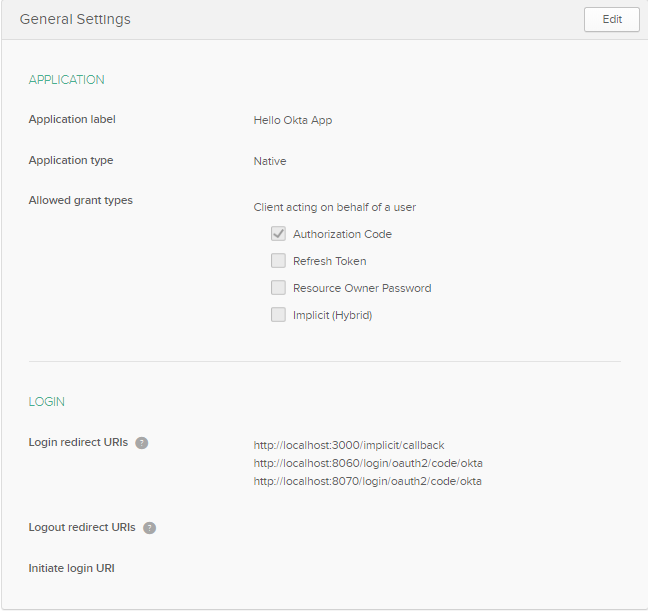
Login to your Okta account. Navigate to Applications in the admin console and click: Add Application. Choose Native and click Next.
Populate the fields with these values:
| FIELD NAME | VALUE |
|---|---|
| Name | Hello Okta App |
| Login redirect URIs | http://localhost:8060/bff/swagger-ui/oauth2-redirect.html http://localhost:8070/api/swagger-ui/oauth2-redirect.html http://localhost:3000/implicit/callback https://kubernetes.docker.internal/bff/swagger-ui/oauth2-redirect.html https://kubernetes.docker.internal/api/swagger-ui/oauth2-redirect.html https://kubernetes.docker.internal/implicit/callback |
| Logout redirect URIs | http://localhost:3000 https://kubernetes.docker.internal |
| Allowed grant types | Authorization Code |
Click Done.
General Settings tab will be displayed:
Scroll down to the Client Credentials section and copy the Client ID. This value will be used by our app.
Make sure that:
- Initiate login URI is empty
- Use PKCE (for public clients) radio button is selected as Client authentication in Client Credentials section.
This Application will be used for Server-to-Server Communication between Client and Server application back-ends using Client Credentials authorization flow.
Navigate to Applications in the admin console and click: Add Application. Choose Service and click Next.
Populate the fields with these values:
| FIELD NAME | VALUE |
|---|---|
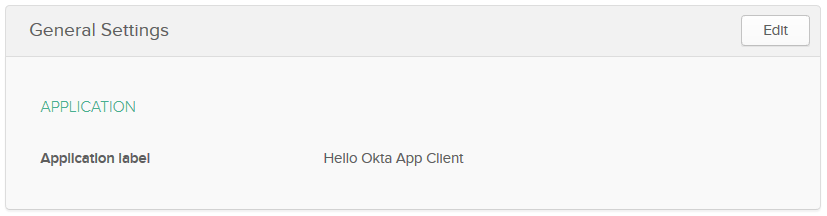
| Name | Hello Okta App Client |
Click Done.
General Settings tab will be displayed:
Scroll down to the Client Credentials section and copy the Client ID and Client Secret. These values will be used by our app.
Navigate to API > Authorization Servers. Click Add Authorization Server. Fill in the values:
| FIELD NAME | VALUE |
|---|---|
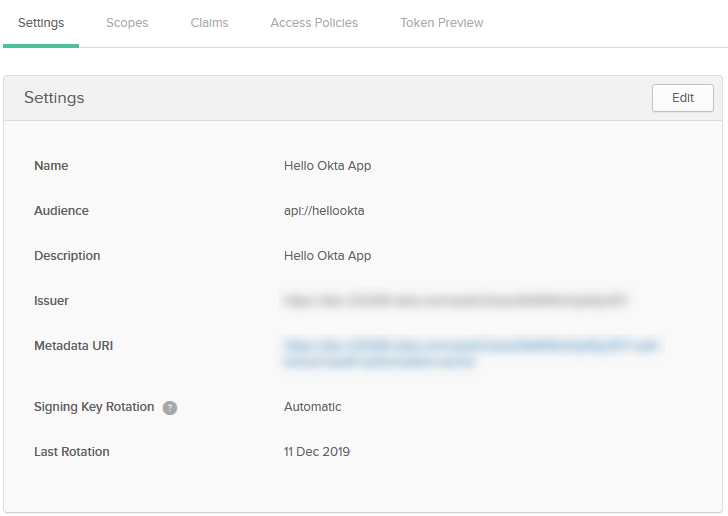
| Name | Hello Okta App |
| Description | Hello Okta App |
| Audience | api://hellookta |
Click Done.
Settings tab will be displayed:
Copy the Issuer URL. This value will be used by our app.
Create a custom scope for our consumer application to restrict access token to this example.
From the menu bar select API > Authorization Servers.
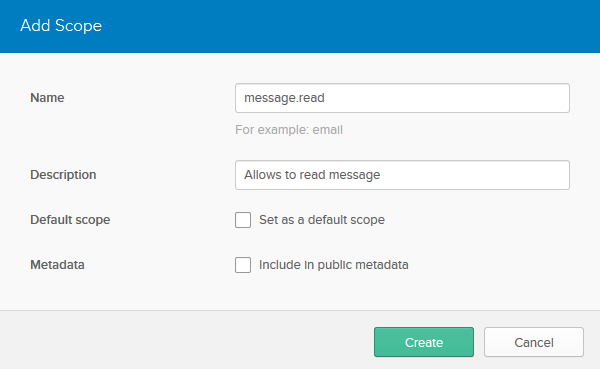
Edit the authorization server created in the previous step by clicking on the edit pencil, then click Scopes > Add Scope.
Fill out the name field with message.read and press Create:
To include custom claims in an ID token or an access token, they should be added to our Custom Authorization Server.
Let's add a Groups claim to ID tokens and access tokens to perform authentication and authorization using the out Custom Authorization Server.
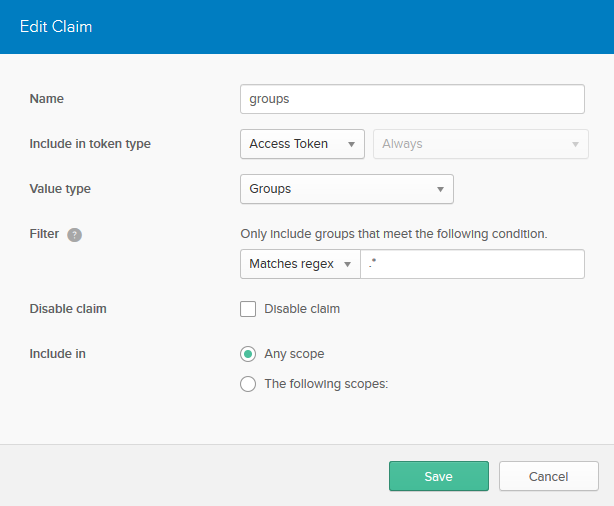
Click Claims > Add Claim. Fill in the fields with these values (leave those not mentioned as their defaults):
| FIELD NAME | VALUE |
|---|---|
| Name | groups |
| Include in token type | Access TokenAlways |
| Value type | Groups |
| Filter | Matches regex .* |
Click Create.
Created Claim will look like:
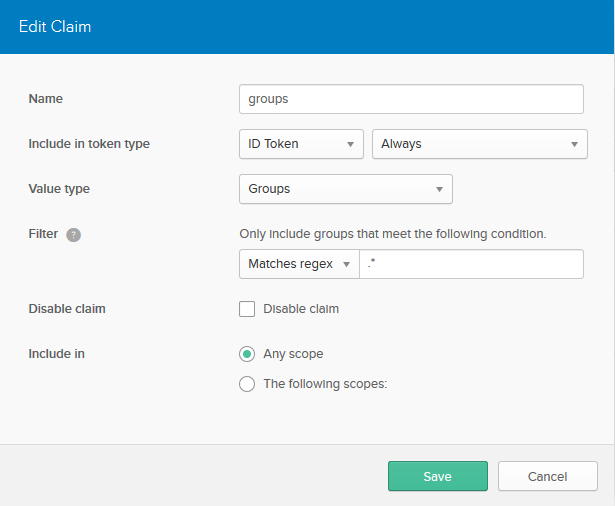
Click Claims > Add Claim. Fill in the fields with these values (leave those not mentioned as their defaults):
| FIELD NAME | VALUE |
|---|---|
| Name | groups |
| Include in token type | ID TokenAlways |
| Value type | Groups |
| Filter | Matches regex .* |
Click Create.
Created Claim will look like:
Okta Access Policies allows to restrict access to application resources. Each Access Policy applies to a particular OpenID Connect application. Access Policies are containers for rules. Rules define different access depending on the nature of the token request.
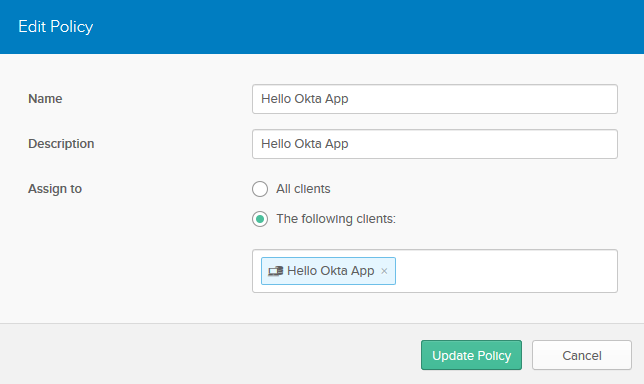
Click the Access Policies tab. Click Add Policy. Fill in the fields with these values:
| FIELD NAME | VALUE |
|---|---|
| Name | Hello Okta App |
| Description | Hello Okta App |
| Assign to | The following clients: Hello Okta App |
Click Create Policy.
Created Policy will look like:
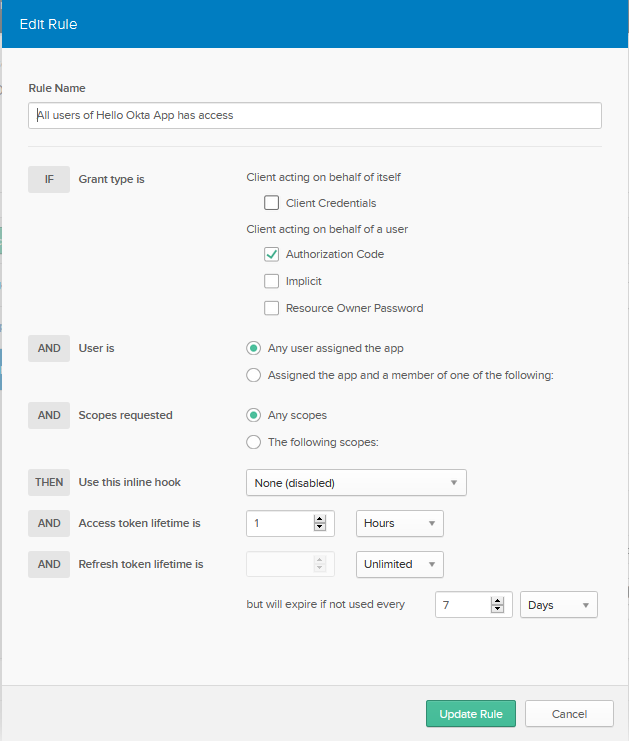
Click Add Rule. Fill in the fields with these values:
| FIELD NAME | VALUE |
|---|---|
| Name | All users of Hello Okta App has access |
| Grant type is | Authorization Code |
| Scopes requested | The following scopes: OIDC default scopes |
Click Create Rule.
Created Rule should look like:
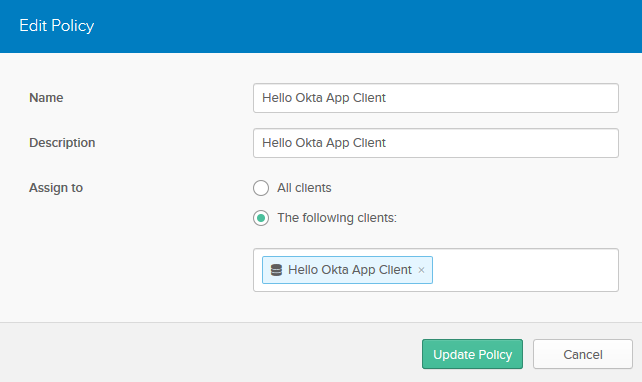
Click the Access Policies tab. Click Add Policy. Fill in the fields with these values:
| FIELD NAME | VALUE |
|---|---|
| Name | Hello Okta App Client |
| Description | Hello Okta App |
| Assign to | The following clients: Hello Okta App Client |
Click Create Policy.
Created Policy will look like:
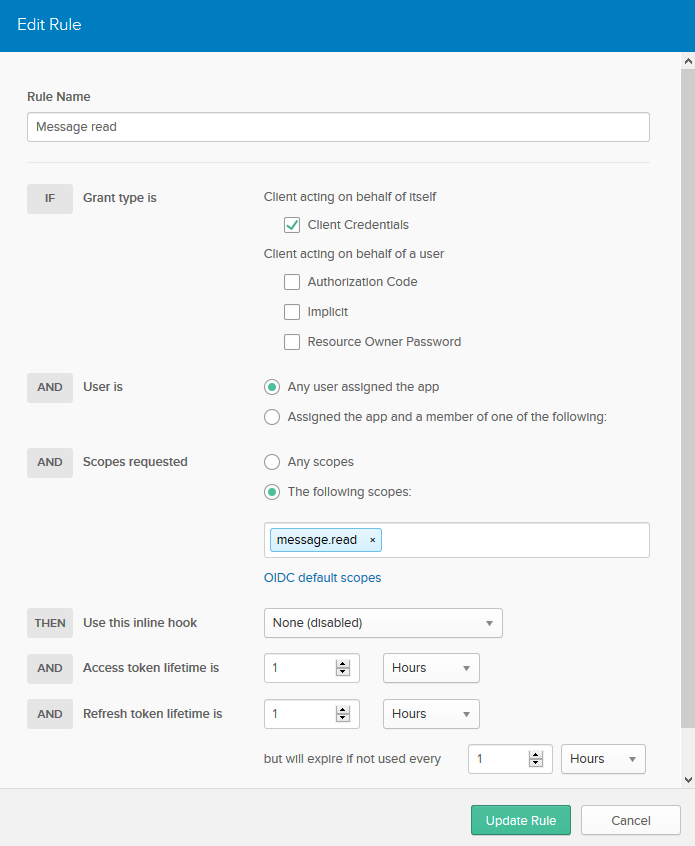
Click Add Rule. Fill in the fields with these values:
| FIELD NAME | VALUE |
|---|---|
| Name | Message read |
| Grant type is | Client Credentials |
| Scopes requested | The following scopes: message.read |
Click Create Rule.
Created Rule should look like:
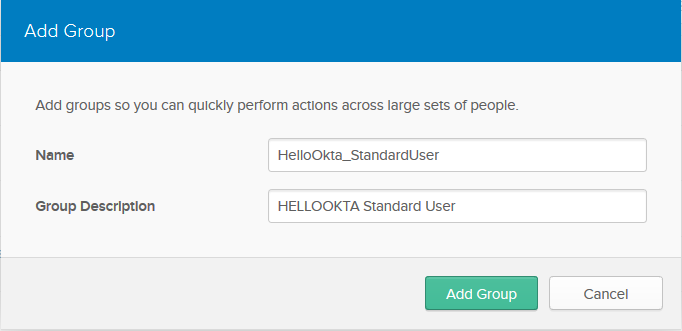
Navigate to Users > Groups. Click Add Group. Fill in the values:
| FIELD NAME | VALUE |
|---|---|
| Name | HelloOkta_StandardUser |
| Group Description | HELLOOKTA Standard User |
Click Add Group.
- Navigate to Users > Groups.
- Click on the HelloOkta_StandardUser group.
- Click on the Manage People button.
- Use the search box to find your user and add yourself to the group.
- Click Save button
- Navigate to API > Trusted Origins.
- Add the following 2 Origins with both
CORSandRedirect:
API
- Copy
.env.dev.sampleto.env.devunderhello-okta-api/env - Fill in your configuration properties instead of
???
BFF
- Copy
.env.dev.sampleto.env.devunderhello-okta-bff/env - Fill in your configuration properties instead of
???
To build API and BFF images:
docker-compose build api
docker-compose build bff
Note, app.jar should be built first from the parent directory using the following command:
gradlew clean build
To bring up API and BFF services:
docker-compose up api
docker-compose up bff
To bring up all the services:
docker-compose up -d
See README.md to deploy application to Kubernetes Cluster (Docker Desktop)