SnakeYAML-CVE-2022-1471-POC
Either build the jar on your host with mvn clean compile assembly:single
Or use docker to build an image with docker build -t snakeyaml .
Run the container with docker run --rm -p8080:8080 snakeyaml
or the jar if you built on your host with java -jar target/snakeyaml-1.0-SNAPSHOT-jar-with-dependencies.jar
Send a get request to serialize object of student class and send yaml as response
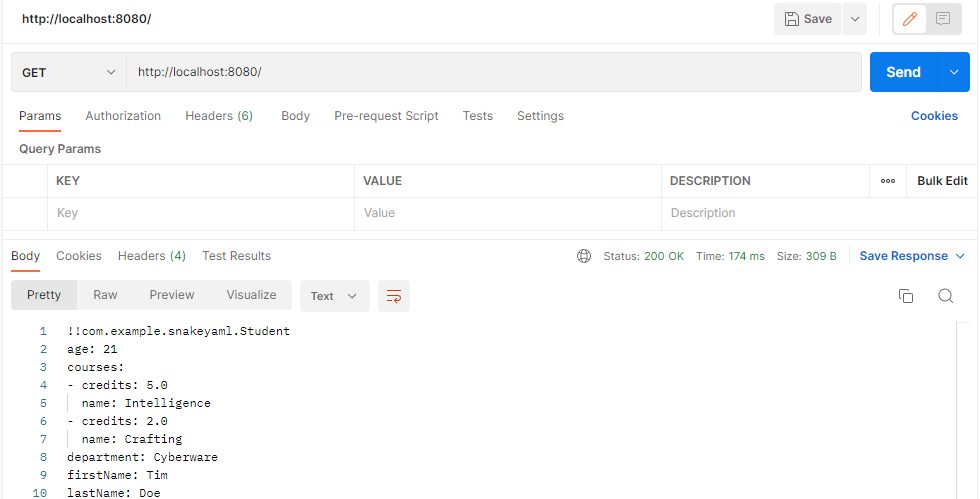
Send a post request with yaml to read YAML object as custom java object - deserialization
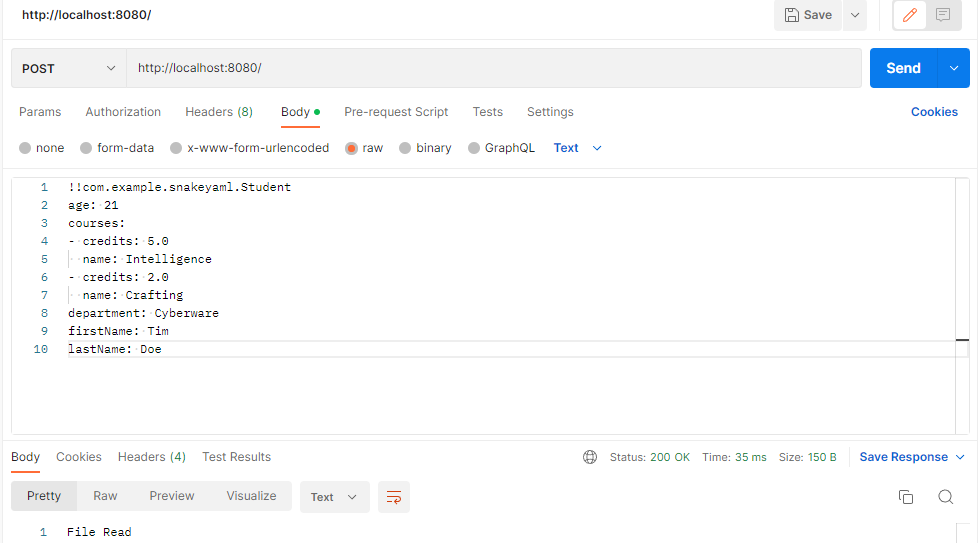
Execute python3 -m http.server 8000 to run the http server
Send a post request with yaml containing exploit

You should observe a HTTP GET request on the listner