Basic project about an e-commerce REST API:
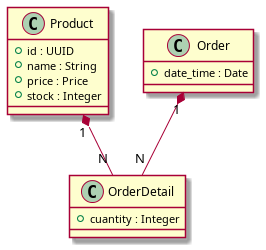
Class diagram:
Components:
- REST API (backend):
- Database:
- PostgreSQL 14.1
- Web Server:
- NGINX 1.21.4
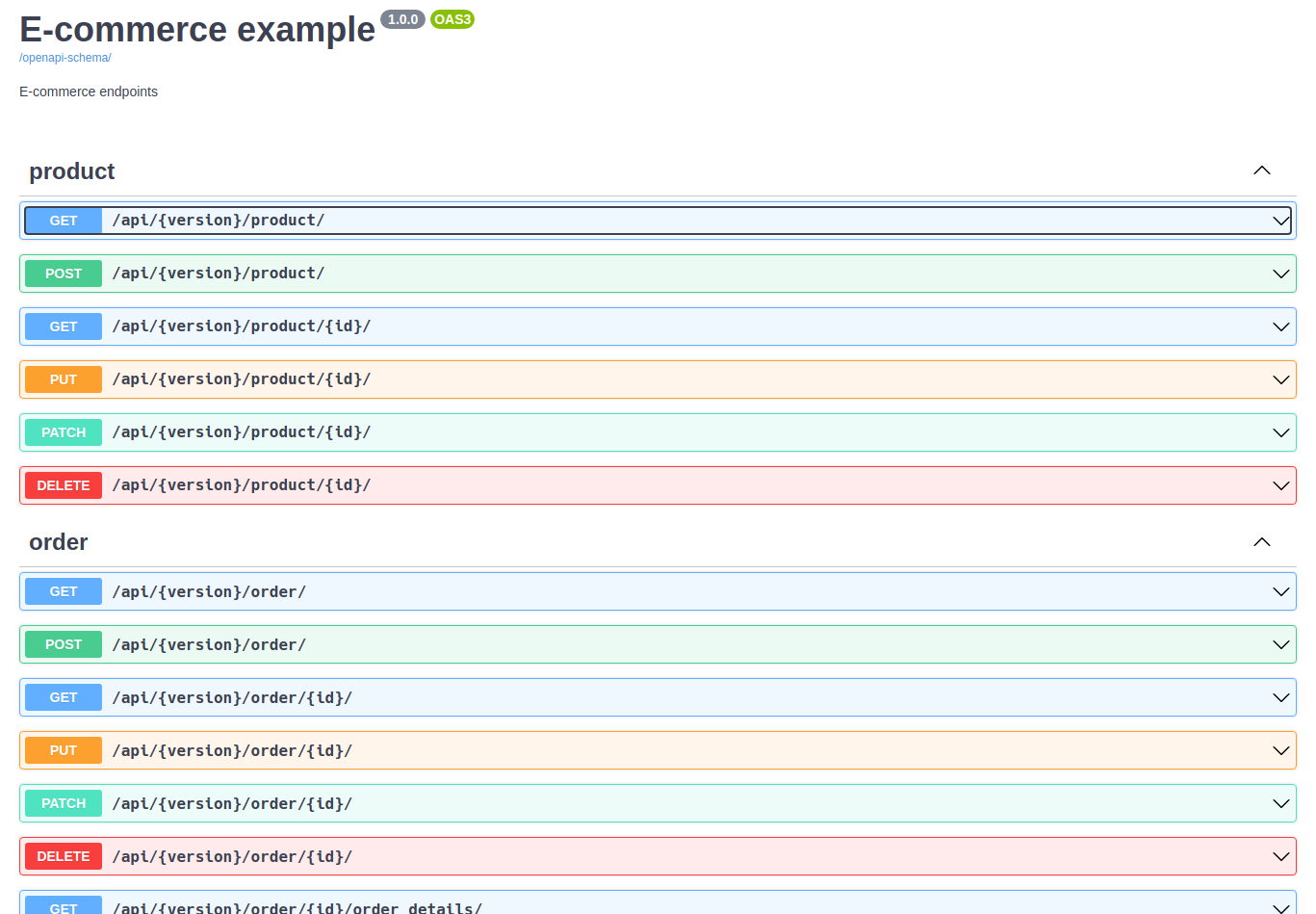
bash install.shHere are some examples of how to use the Rest API: https://localhost/swagger-ui/ (jq is required)
export $(grep -v '^#' .env | xargs)JWT_TOKEN=$(
curl -k -s -X POST \
'https://localhost/api/token/' \
-H 'Content-Type: application/json' \
-d "{
\"username\": \"${DJANGO_SUPERUSER_USERNAME}\",
\"password\": \"${DJANGO_SUPERUSER_PASSWORD}\"
}" \
| jq -r '.access'
) && echo "JWT token: ${JWT_TOKEN}"PRODUCT_ID=$(
curl -k -s -X POST \
'https://localhost/api/v1/product/' \
-H 'Content-Type: application/json' \
-H "Authorization: Bearer ${JWT_TOKEN}" \
-d '{
"name": "test 1.1",
"price": "1200.99",
"stock": 10
}' \
| jq -r '.id'
) && echo "product ID: ${PRODUCT_ID}"PUT
curl -k -s -X PUT \
"https://localhost/api/v1/product/${PRODUCT_ID}/" \
-H 'Content-Type: application/json' \
-H "Authorization: Bearer ${JWT_TOKEN}" \
-d '{
"name": "test 1.2",
"price": "1500",
"stock": 10
}' | jqPATCH
curl -k -s -X PATCH \
"https://localhost/api/v1/product/${PRODUCT_ID}/" \
-H 'Content-Type: application/json' \
-H "Authorization: Bearer ${JWT_TOKEN}" \
-d '{
"price": 1700
}' | jqSwagger UI: https://localhost/swagger-ui/
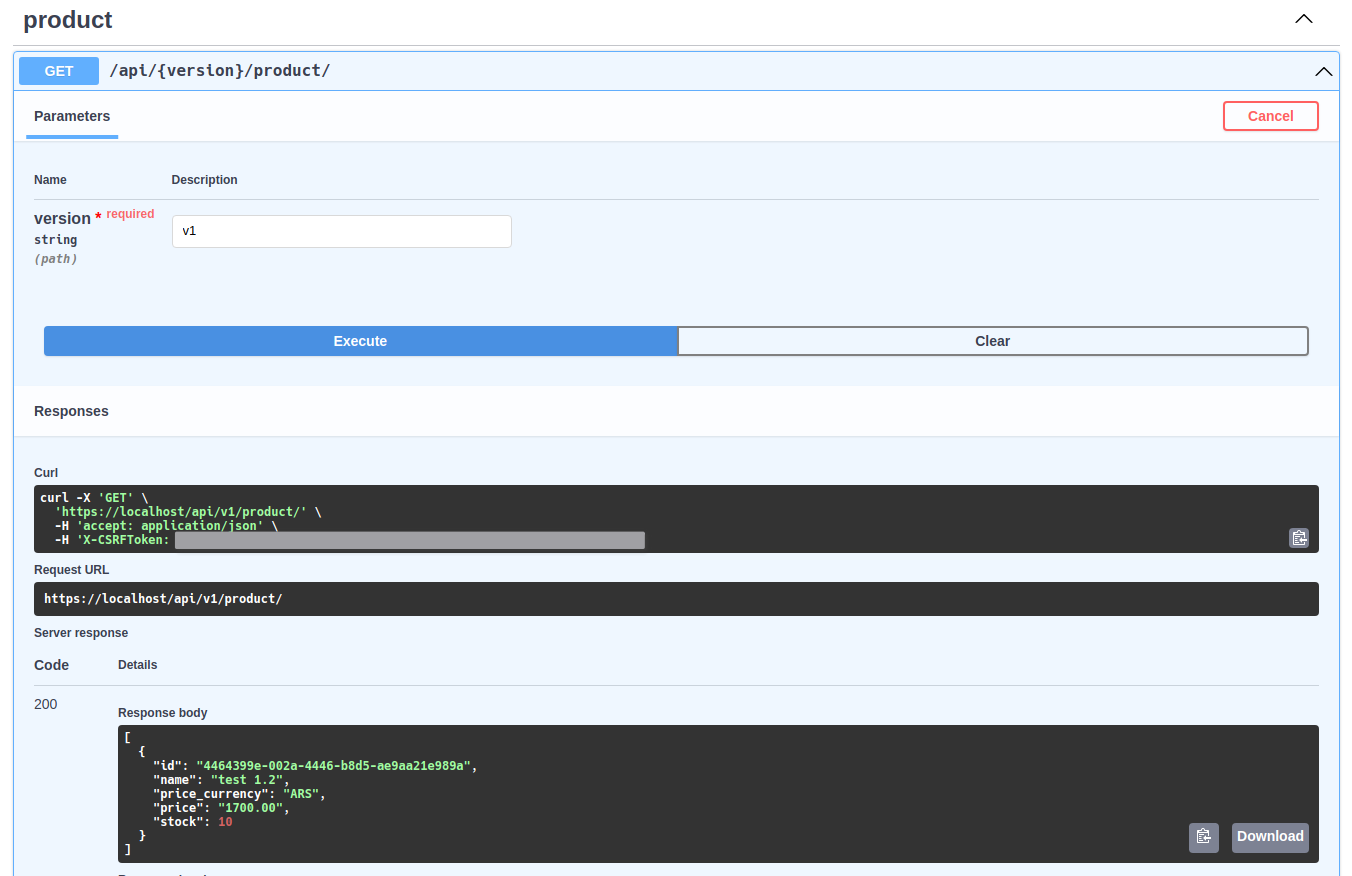
product list:
run backend unit testing:
docker-compose exec backend python manage.py testCheckers statically analyzes the code to find problems.
# run shellcheck, pylint, prospector, black and isort
docker-compose exec backend bash code_checkers.shTools used:
-
shellcheck: ShellCheck is a GPLv3 tool that gives warnings and suggestions for bash/sh shell scripts.
-
pylint: Pylint is a Python static code analysis tool which looks for programming errors, helps enforcing a coding standard, sniffs for code smells and offers simple refactoring suggestions.
-
black: Black is the uncompromising Python code formatter.
-
isort: Python utility / library to sort imports alphabetically, and automatically separated into sections and by type.
-
prospector: Prospector is a tool to analyse Python code and output information about errors, potential problems, convention violations and complexity.
Tools executed by Prospector:
- bandit: Bandit is a tool designed to find common security issues.
- dodgy: It is a series of simple regular expressions designed to detect things such as accidental SCM diff checkins, or passwords or secret keys hard coded into files.
- mccabe: Complexity checker.
- mypy: Mypy is an optional static type checker for Python.
- pep257: pep257 is a static analysis tool for checking compliance with Python PEP 257.
- pep8: pep8 is a tool to check your Python code against some of the style conventions in PEP 8.
- pyflakes: Pyflakes analyzes programs and detects various errors.
- pyroma: Pyroma is a product aimed at giving a rating of how well a Python project complies with the best practices of the Python packaging ecosystem, primarily PyPI, pip, Distribute etc, as well as a list of issues that could be improved.