Tenda N300 Authentication Bypass via Malformed HTTP Request Header Python POC
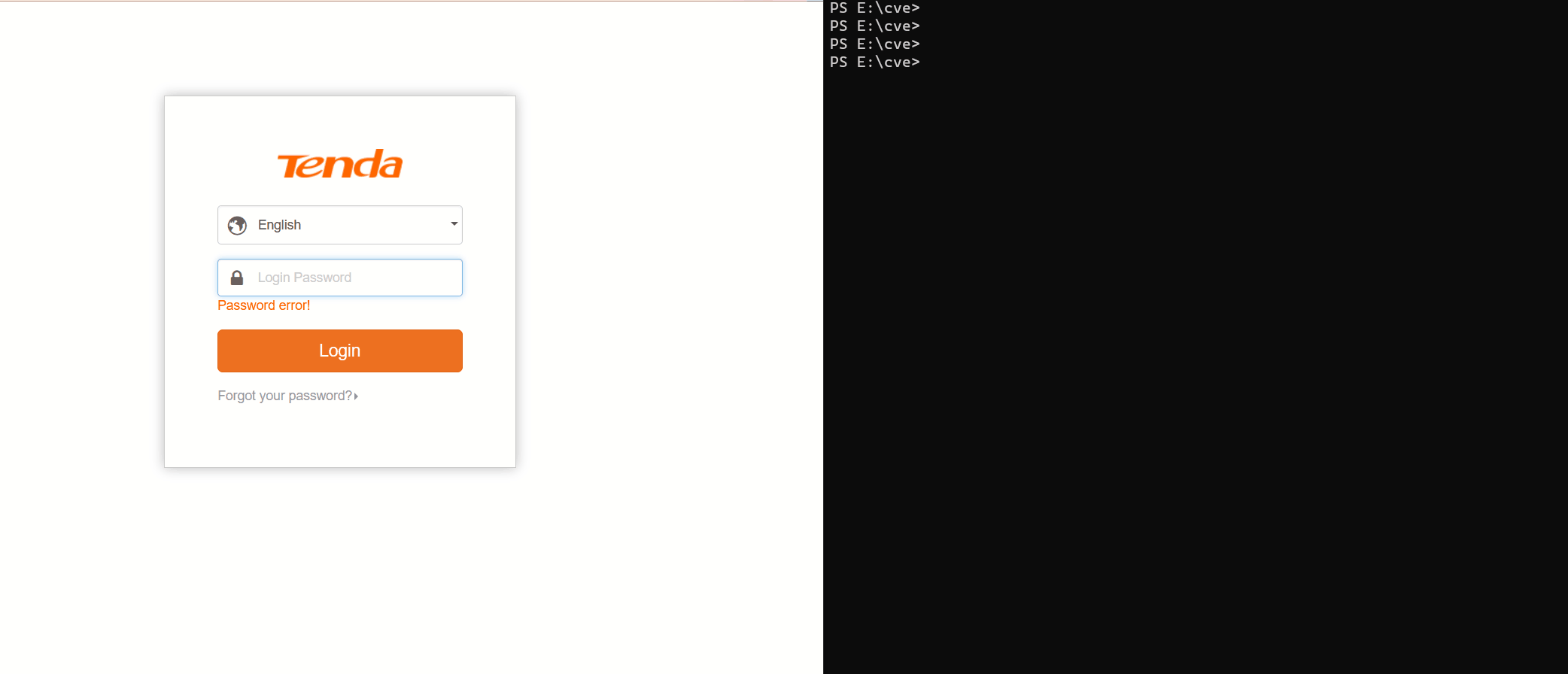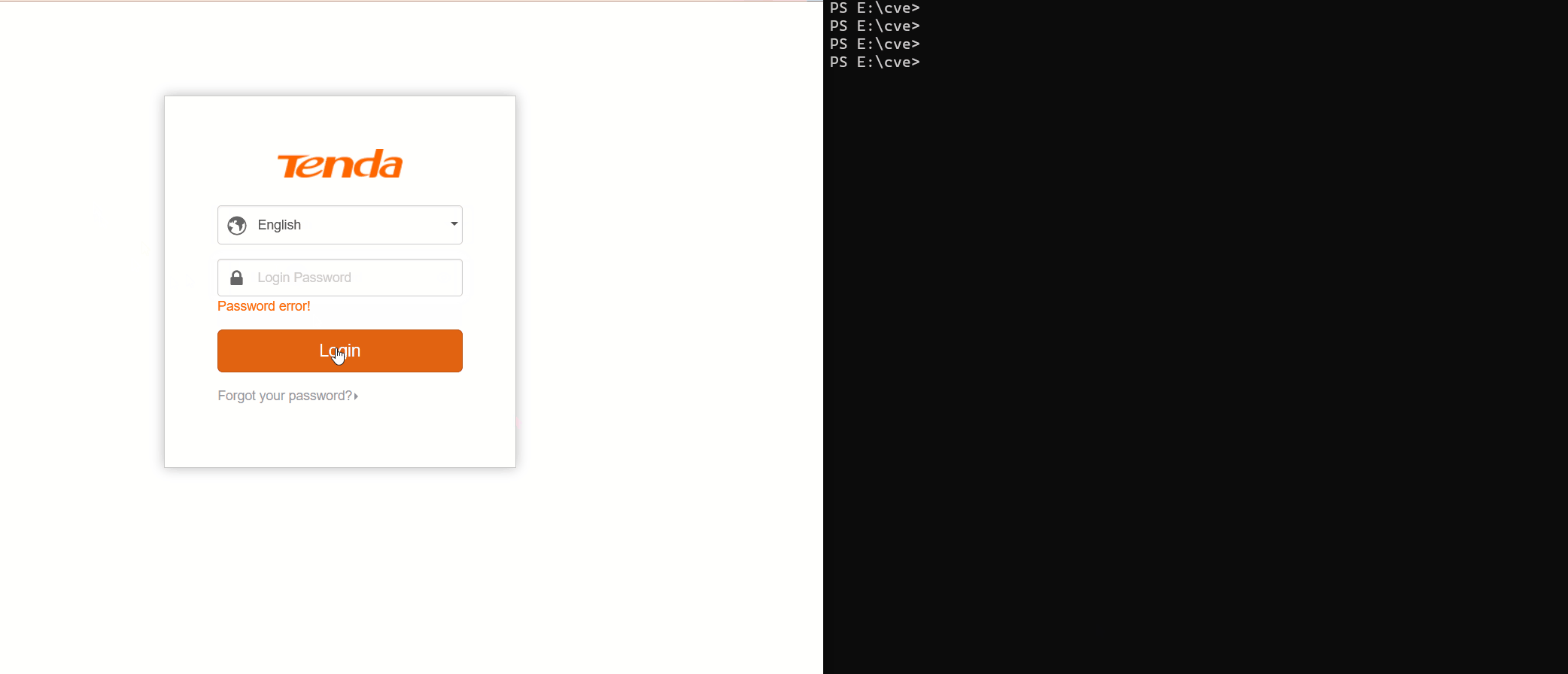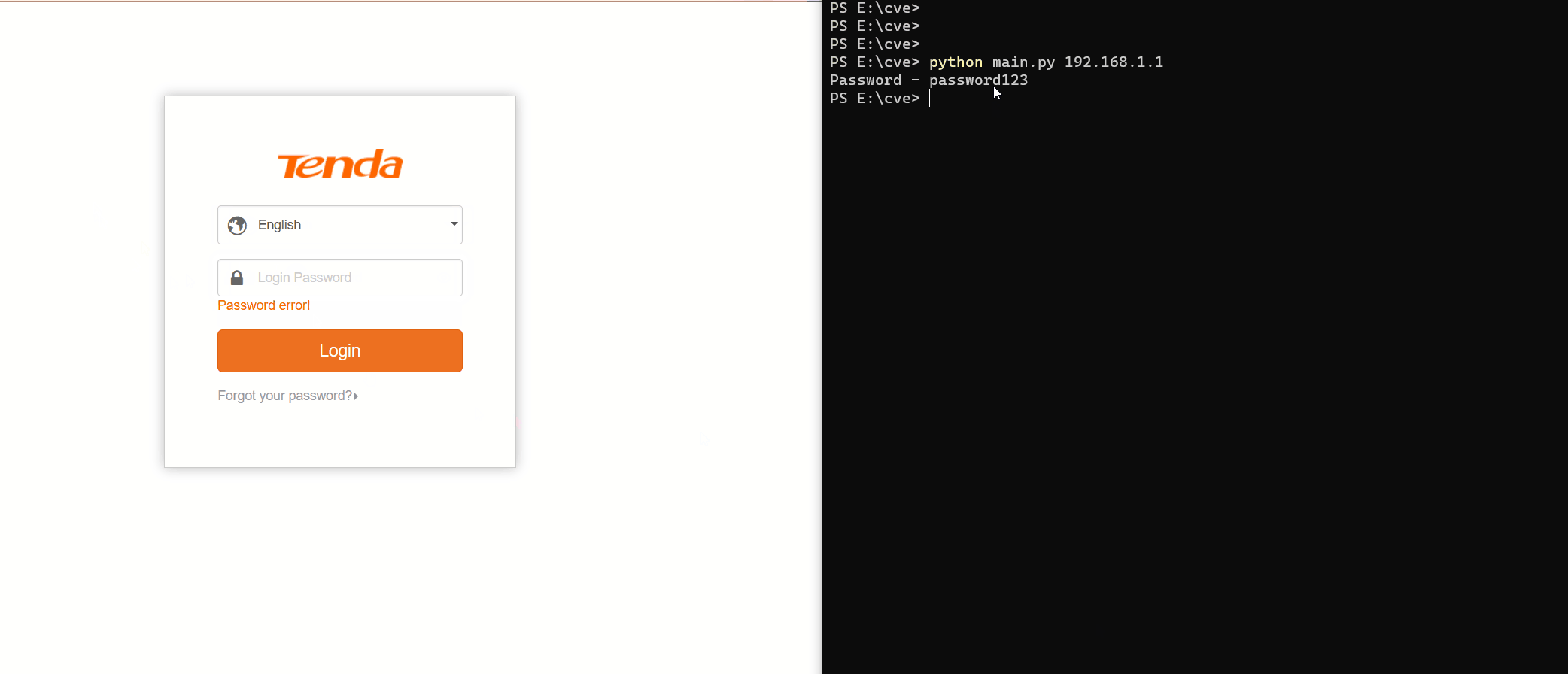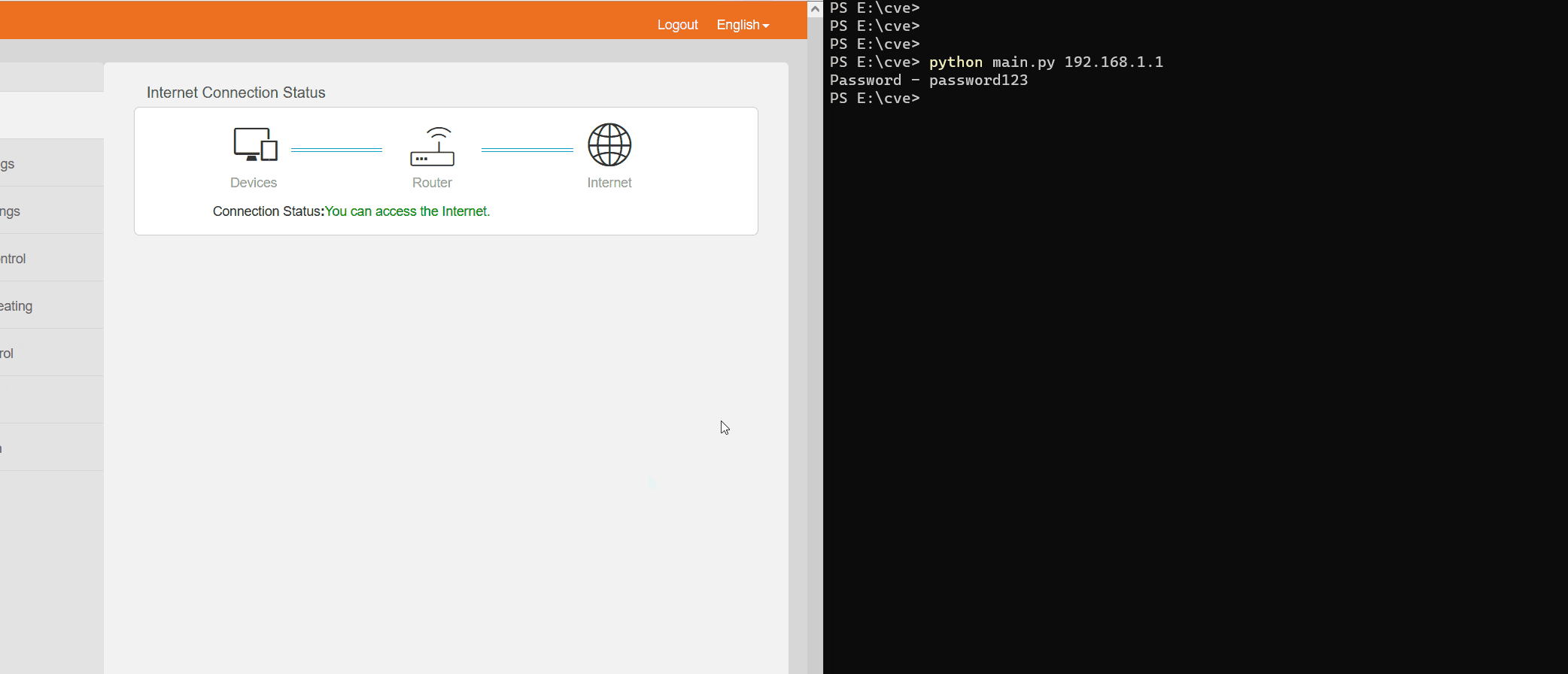
Tenda N300 F3 12.01.01.48 devices allow remote attackers to obtain sensitive information (possibly including an http_passwd line) via a direct request for cgi-bin/DownloadCfg/RouterCfm.cfg, a related issue to CVE-2017-14942. NOTE: the vulnerability report may suggest that either a ? character must be placed after the RouterCfm.cfg filename, or that the HTTP request headers must be unusual, but it is not known why these are relevant to the device's HTTP response behavior.
Original PoC Author: Michelle Bonilla
After so much time since this CVE was published, the vulnerability has still not been fixed! (Last Firmware Version: V12.01.01.42_multi)
python3 main.py <router ip>👤 dumitory-dev
Give a ⭐️ if this project helped you!
This project is MIT licensed.