Customizable Bootloader for STM32 microcontrollers. This example demonstrates how to perform in-application-programming of a firmware located on external SD card with FAT32 file system.
- Configurable application space
- Checksum verification
- Flash protection check, write protection enable/disable
- Extended error handling, fail-safe design
- Bootloader firmware update and the ability to perform full chip re-programming: enter ST's built-in bootloader from software (without triggering the BOOT pin)
- SWO tracing for easier debugging and development
- Easy to customize and port to other microcontrollers
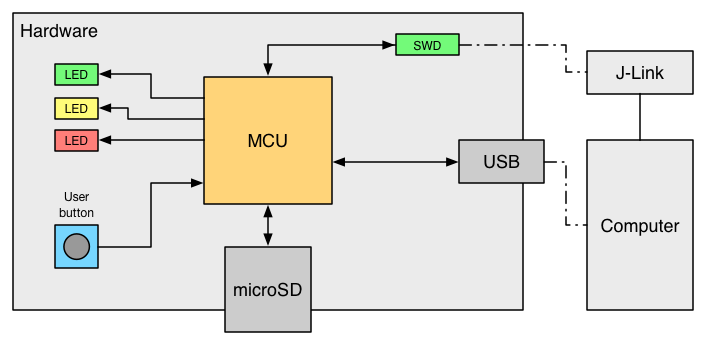
This demo is implemented on a custom hardware (see Figure 1) equipped with a STM32L476VG microcontroller [1, 2]. The microSD card is connected to the MCU over SDIO interface. The implementation uses the official HAL library of ST [3] and is compiled with IAR EWARM. Programming and debugging is performed over SWD with a SEGGER J-Link debug probe.
Note: release v1.03 introduces support for the new STM32L496VG microcontroller [7]. The individual build configurations for different microcontrollers can be selected with a single click in IAR.
Figure 1: System overview
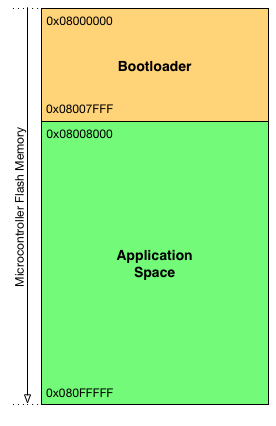
The microcontroller flash is organized as follows: by default the first 32kBytes (16 pages) of the flash is reserved for the bootloader and the rest of the flash is the application space.
Figure 2: Flash organization
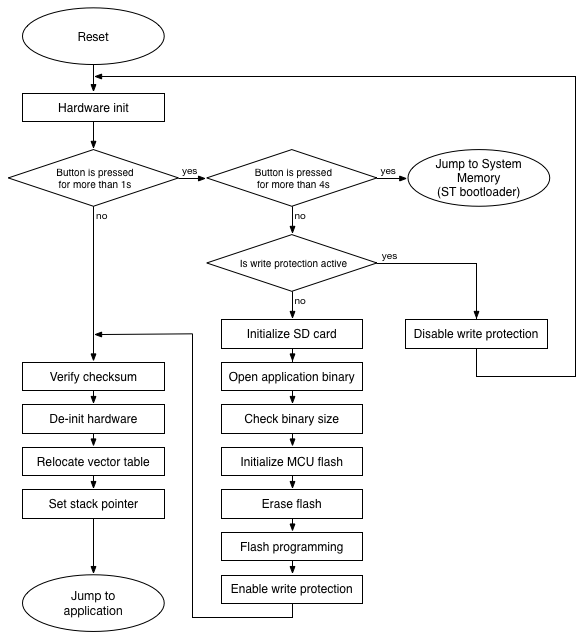
After power-up, the bootloader starts. All three LEDs are flashed for a second, then the bootloader checks for user-interaction:
-
If the button is not pressed, then the bootloader tries to launch the application: First it checks the application space. If there is a firmware located in the application space, the bootloader calculates the checksum over the application space and compares with the application checksum (if the checksum feature is enabled). Finally, the bootloader prepares for the jump by resetting the peripherals, disabling the SysTick, setting the vector table and stack pointer, then the bootloader performs a jump to the application.
-
If the button is pressed and released within 4 seconds: the bootloader tries to update the application firmware by performing the following sequence:
- Checks for write protection. If the application space is write-protected, then the red LED is switched on and the yellow LED is flashed for five seconds. If the button is pressed within this interval, the bootloader disables the write protection by re-programming the flash option bytes and performs a system reset (required after flash option bytes programming). Please note that after disabling the write protection, the user has to invoke the application update procedure again by pressing the button in order to continue the firmware update.
- Initializes SD card, looks for application binary and opens the file.
- Checks the file size whether it fits the application space in the microcontroller flash.
- Initializes microcontroller flash.
- Erases the application space.
- Performs flash programming.
- Enables write protection of application space if this feature is enabled in the configuration.
- After successful in-application-programming, the bootloader launches the application.
-
If the button is pressed for more than 4 seconds: the bootloader launches ST's built-in bootloader located in the internal boot ROM (system memory) of the chip. For more information, please refer to [4]. With this method, the bootloader can be updated or even a full chip re-programming can be performed easily, for instance by connecting the hardware to the computer via USB and using DFU mode [5, 6].
Figure 3: Bootloader sequence
stm32-bootloader/
|—— Drivers/
|—— EWARM/
|—— Inc/
|—— Middlewares/
`—— Src/
Drivers and Middlewares folders contain the CMSIS, HAL and FatFs libraries for the microcontroller. The bootloader source code and corresponding header files can be found in Src and Inc folders respectively.
The bootloader can be easily customized and tailored to the required hardware and environment, i.e. to perform firmware updates over various interfaces or even to implement over-the-air (OTA) updates if the hardware incorporates wireless communication modules. In order to perform successful in-application-programming, the following sequence has to be kept:
- Check for flash write protection and disable it if necessary.
- Initialize flash with
Bootloader_Init(). - Erase application space with
Bootloader_Erase()(optional, but recommended). - Prepare for programming by calling
Bootloader_FlashBegin(). - Perform programming by repeatedly calling the
Bootloader_FlashNext(uint64_t data)function. The programming procedure requires 8 bytes of data (double word) to be programmed at once into the flash. This function automatically increases the address where the data is being written. - Finalize programming by calling
Bootloader_FlashEnd().
The application image has to be in binary format. If the checksum verification is enabled, the binary must include the checksum value at the end of the image. When creating the application image, the checksum has to be calculated over the entire image (except the checksum area) with the following parameters:
- Algorithm: CRC32
- Size: 4 bytes
- Initial value: 0xFFFFFFFF
- Bit order: MSB first
Important notice: in order to perform a successful application jump from the bootloader, the vector table of the application firmware should be relocated. When creating an application, the microcontroller startup code sets the vector table location to 0x00000000 in the system_stm32xxxx.c file by default. This has to be either disabled (the bootloader can be configured to perform the vector table relocation before the jump) or manually set to the appropriate value which is the start address of the application space.
The bootloader can be widely configured in the bootloader.h file. The file includes detailed comments and descriptions related to the configurable parameters and definitions.
[1] STM32L476VG, http://www.st.com/en/microcontrollers/stm32l476vg.html
[2] RM0351, “STM32L4x5 and STM32L4x6 advanced ARM®-based 32-bit MCUs Reference Manual”, http://www.st.com/resource/en/reference_manual/dm00083560.pdf
[3] UM1884, “Description of STM32L4 HAL and Low Layer drivers”, http://www.st.com/resource/en/user_manual/dm00173145.pdf
[4] AN2606, "STM32 microcontroller system memory boot mode", http://www.st.com/resource/en/application_note/cd00167594.pdf
[5] AN3156, "USB DFU protocol used in the STM32 bootloader", http://www.st.com/resource/en/application_note/cd00264379.pdf
[6] UM0412, "Getting started with DfuSe USB device firmware upgrade", http://www.st.com/resource/en/user_manual/cd00155676.pdf
[7] STM32L496VG, http://www.st.com/en/microcontrollers/stm32l496vg.html