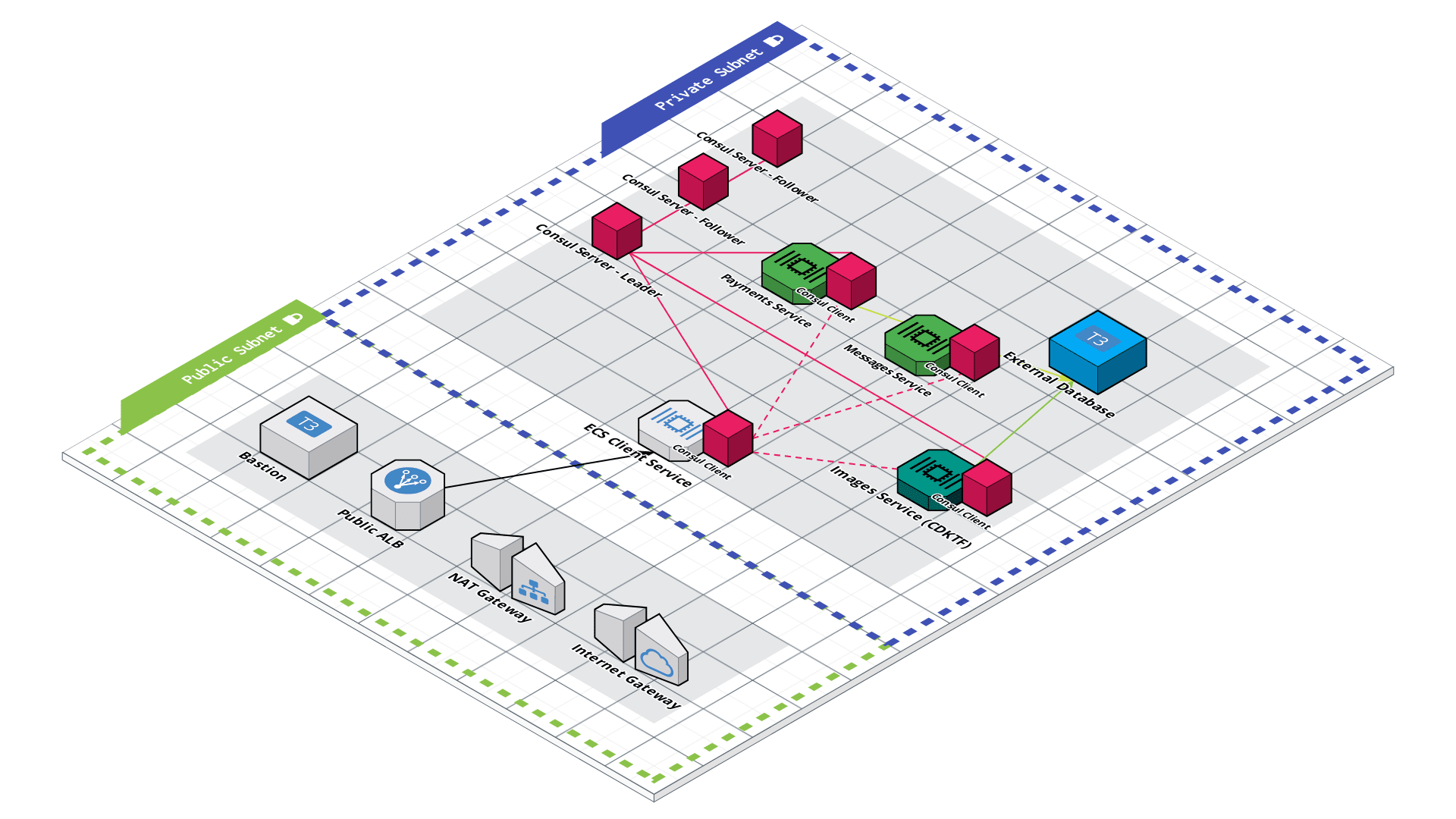
This repository demonstrates setting up an Amazon ECS microservices architecture with HashiCorp Terraform and Consul. It also goes along with two other repositories:
- deploys an additional ECS microservice via the CDK for Terraform
- creates Sentinel Policies to guard both projects in Terraform Cloud
All services use Fake Service as for demonstration purposes. You can swap them out with your own containerized services. You will need to change around port configurations and security groups to afford your applications' needs.
-
Have an AWS Account.
-
Install HashiCorp Terraform.
-
Have the AWS CLI Installed.
-
Create an AWS IAM User with Admin or Power User Permissions.
- this user will only be used locally
- Configure the AWS CLI with the IAM User from Step 4.
- Terraform will read your credentials via the AWS CLI
- Other Authentication Methods with AWS and Terraform
-
Clone this repo to an empty directory.
-
Run
terraform planto see what resources will be created. -
Run
terraform applyto create the infrastructure on AWS! -
Open your Consul Server's Load Balancer (output as
consul_server_endpoint). -
Run
bash scripts/post-apply.shand follow the instructions OR open your terraform statefile and copy your Consul Bootstrap Token. Use this to Login to the Consul UI.
- It may take a few moments for all of the services to come on line.
- you can also grab this from your Terraform State file, this script is only for convenience.
-
Click on Services in the side navigation and ensure all services are GREEN (denoted by a checkmark).
-
Navigate to your Client Application Load Balancer (output as
client_endpoint) to confirm that everything is working.
- It may take a few moments for the new intentions to be recognized.
- Run
terraform destroywhen you're done to get rid of the infrastructure.
-
Fork this Repository.
-
Create a Workspace in Terraform Cloud. You'll need to reference this workspace name in the CDKTF project if you deploy it.
- optionally change the
workspacestags inmain.tf
ec2_key_pair_nametfc_organizationtfc_workspace_tag
Guarding Your TFC Workspaces With HashiCorp Sentinel
We can also insert an addition step between the terraform plan and terraform apply phases that checks our code, plan, statefile, and run data using HashiCorp Sentinel.
-
Fork the Sentinel Policy Repo
-
Head to Settings in your Terraform Cloud console
-
Click on Policy Sets in the side navigation bar
-
Click on Connect a new policy set in the Policy Sets screen
-
Follow the Connect a Policy Set step-by-step
-
Name the policy set whatever you'd like
-
Under the Workspaces area, select the specific workspaces you'd like this policy to guard.
-
Click Connect policy set
-
Optionally trigger a run in any of your workspaces to view the policy in action.
Reach out to J. Cole Morrison. Also, feel free to leave any issues you run into on this Github Repo!