Create temporary AWS security credentials from a SAML authentication response.
- You are using federated login to your AWS account, possibly using Single Sign On and Multi-Factor Authentication.
- Typically you navigate to a enterprise login page.
- This login page will eventually redirect you to the Amazon Web Services Sign-In page.
- From there you select the AWS account and role for which to open the AWS Console.
The assume_role_with_saml project provides a Chrome Extension content script adding an Assume Role button to Amazon Web
Services Sign-In page:
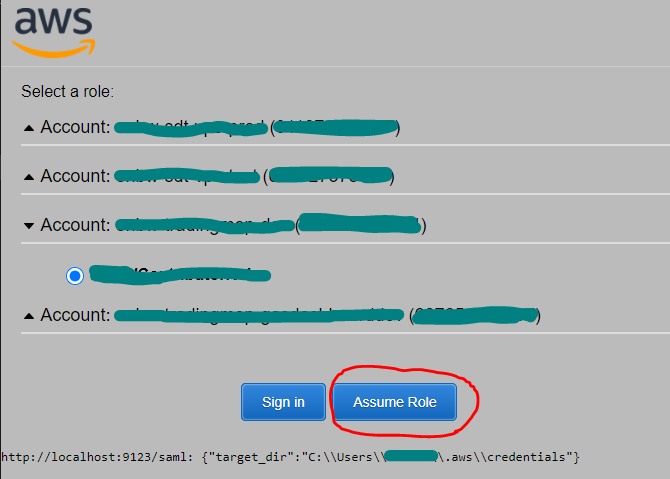
Clicking the Assume Role button calls a small local web server, which writes temporary AWS credentials to the shared
credential file (~/.aws/credentials).
⚠ The Chrome Extension content script is only attached to the page https://signin.aws.amazon.com/saml. If your redirect-page is different, then this project will not work.
You install less than 150 lines of code with no external dependencies except boto3, which you probably need anyway.
- Clone this project.
- Optionally create virtual environment and install boto3.
- Add this Chrome Extension according to Getting started - Chrome Developers:
- Open the Extension Management page by navigating to chrome://extensions.
- Enable Developer Mode by clicking the toggle switch next to Developer mode.
- Click the LOAD UNPACKED button and select the project (=extension) directory.
Provide a starter script (I call it my_assume_role.py) of the form
import webbrowser
import server
# Optionally open sso page
webbrowser.open_new('https://my_enterprise_login_page')
server.run(identity_provider_name='my_identity_provider_name')
You get a list of Identity providers on AWS IAM -> Identity providers or with
import boto3, pprint
pprint.pprint(boto3.client('iam').list_saml_providers())
My prefered way on MS-Windows is a shortcut amounting to
cd c:/ws/projects/assume_role_with_saml
venv/scripts/python.exe my_assume_role.py
Due to its local nature, no attack vectors are added.
However, a user may inadvertently click the Assume Role button. The user will then not realize that the
shared AWS credentials were changed. AWS SDK API calls may now run on an account the user does not expect.
⚠ The Chrome extension is not on the Chrome Web Store, because extensions there are notoriously difficult to audit. Instead, I urge you to install the extension locally after you do a code audit.