PoC app to demonstrate how to perform dynamic analysis on apps installed inside a cloning app without root or repackaging the application. This app is based on VirtualApp Changes required to use Virtual App in 9.0 is cloned from VirtualAppEx
Since this app is derived from Virtual app. Please refer to VirtualApp's declaration.
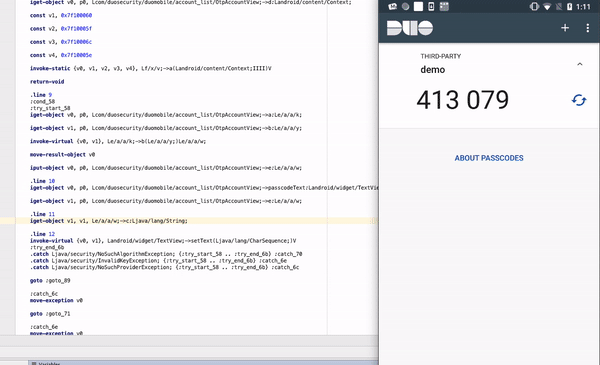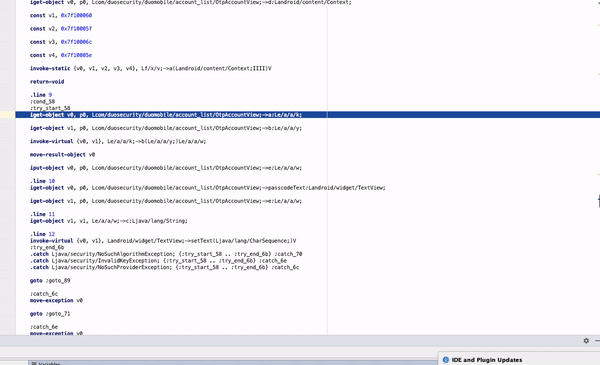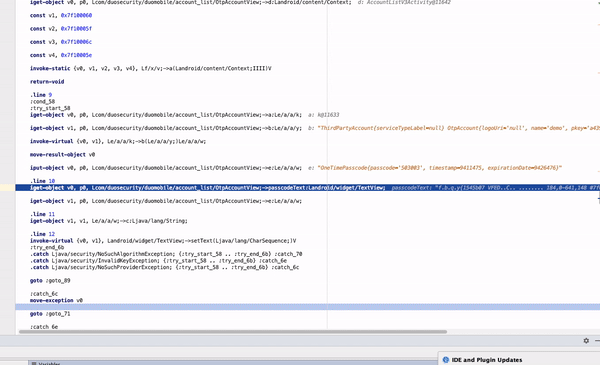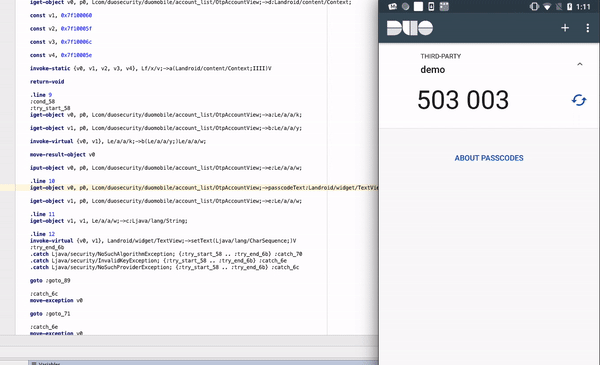
Google Authenticator depends on the default Security Provider. By executing it inside the cloning app OTP seed used in HMAC operation can be fetched from the logcat
The same case with Microsoft Authenticator
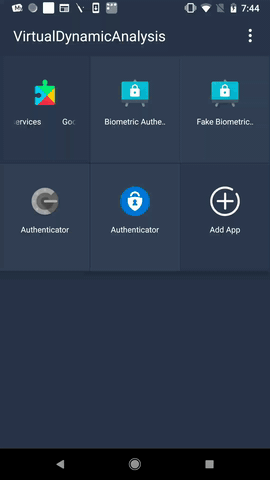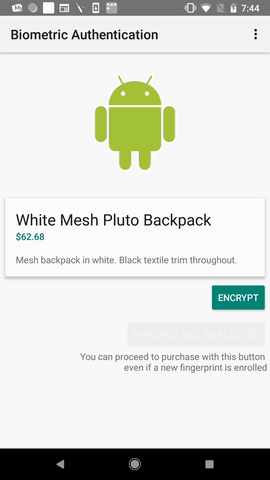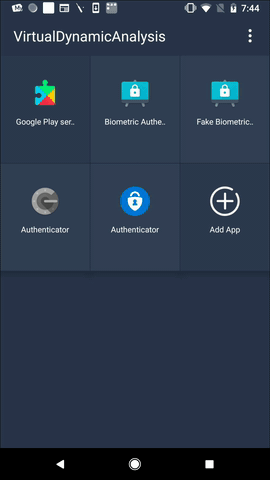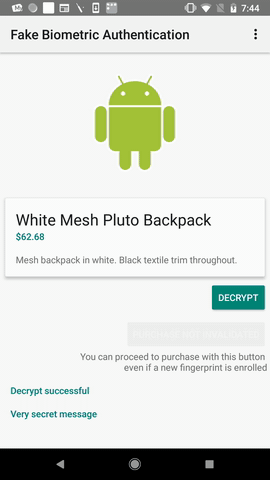
This is to demonstrate how a Fake Biometric Authentication App installed alongside a benign Biometric Authentication app inside cloning app can make use of the AES Key generated inside Android Keystore to decrypt a secret message
This is to demonstrate any guest app can be made debuggable if the host app is debuggable
For more details please visit my blog Part 1 blog Part 2