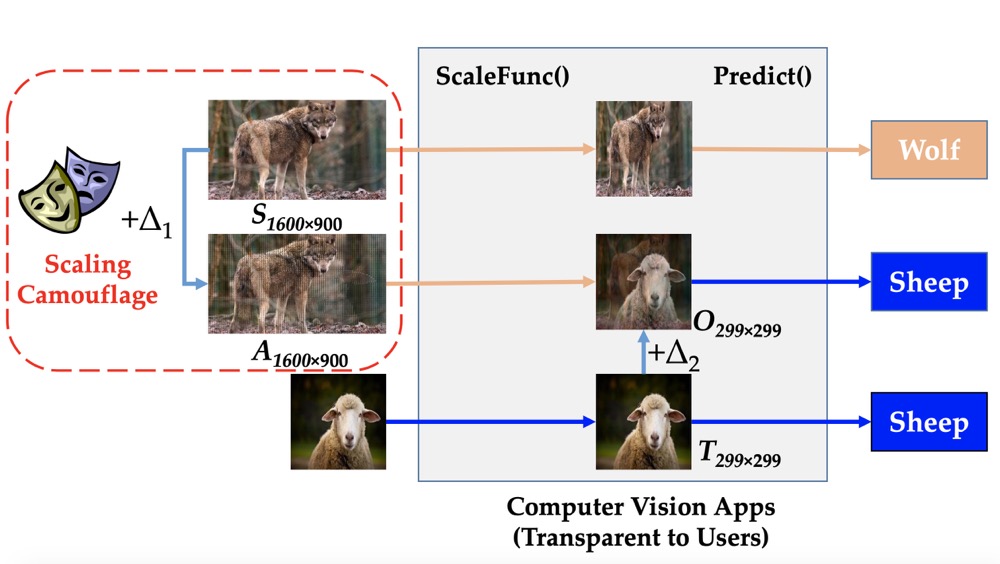
The scaling attack exploits the information loss phenomena in the image down-scaling process. It aims to hide a small target image into a large source image (in our example, we hide a 229*229 wolf image into a 1800*1200 sheep image). After down-scaling, these "sheep" pixels are discarded, while the "wolf" image gets recovered and fed into downstream computer vision applications. As a result, a sheep image to human eyes will be classified as a wolf by computers.
For more details, please refer to our USENIX Security and TDSC paper.
chmod +x setup.sh
./setup.sh
python ./attack.py \
--sourceImg <source image path> \
--targetImg <target image path> \
--attackImg <where to save the attack image> \
--outputImg <output image path> \
--norm <choose $L_p$ attack norm to use> \
[--resizeFunc <resizing function> \]
[--interpolation <interpolation method> \]
[--penalty <constant $c$ set in the attack> \]
[--imageFactor <factor used to scale image pixel value to [0,1]> \]
For example, you can run this:
python ./attack.py --sourceImg sheep.jpg --targetImg wolf.jpg --attackImg attack.jpg --outputImg attack_downscaled.jpg --norm l2 --resizeFunc cv2.resize --interpolation cv2.INTER_LINEAR --penalty 0.01
For more details, you can run:
python ./attack.py --help
- The code is running on Python3
- Supported scaling functions:
| Function | Interpolation methods |
| cv2.resize | cv2.INTER_NEAREST |
| cv2.INTER_LINEAR | |
| cv2.INTER_CUBIC | |
| cv2.INTER_AREA | |
| cv2.INTER_LANCZOS4 | |
| Image.Image.resize | Image.NEAREST |
| Image.LANCZOS | |
| Image.BILINEAR | |
| Image.BICUBIC |
[1] Qixue Xiao*, Yufei Chen*, Chao Shen, Yu Chen, and Kang Li. Seeing is Not Believing: Camouflage Attacks on Image Scaling Algorithms, (USENIX Security '19) (*: co-first author)
[2] Yufei Chen, Chao Shen, Cong Wang, Qixue Xiao, Kang Li, and Yu Chen. Scaling Camouflage: Content Disguising Attack Against Computer Vision Applications (IEEE TDSC)
@inproceedings {xiao2019_usenix,
author = {Qixue Xiao and Yufei Chen and Chao Shen and Yu Chen and Kang Li},
title = {Seeing is Not Believing: Camouflage Attacks on Image Scaling Algorithms},
booktitle = {28th {USENIX} Security Symposium ({USENIX} Security 19)},
year = {2019},
pages = {443--460},
publisher = {{USENIX} Association},
month = aug,
}
@article{chen2020_tdsc,
author={Yufei Chen and Chao Shen and Cong Wang and Qixue Xiao and Kang Li and Yu Chen},
journal={IEEE Transactions on Dependable and Secure Computing},
title={Scaling Camouflage: Content Disguising Attack Against Computer Vision Applications},
year={2021},
volume={18},
number={5},
pages={2017-2028},
doi={10.1109/TDSC.2020.2971601}}