yaraScanParser
Table of Contents
About The Project
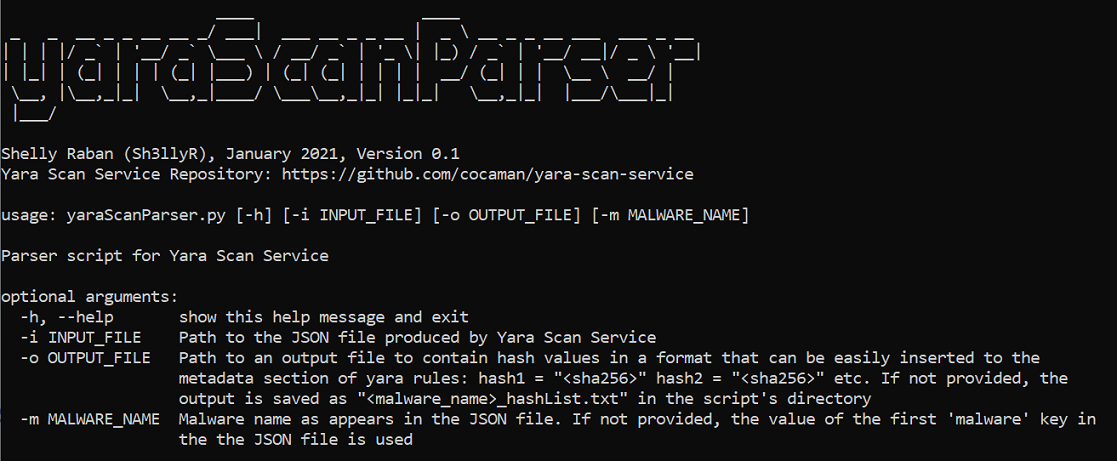
This script is a parsing tool for Yara Scan Service's JSON output file. Yara Scan Service allows to quickly test your YARA rule against a large collection of malicious samples. It helps assure your rule only matches the malware family you are looking for. The output is a JSON file containing all the matched samples. The JSON file contains a lot of information, and yaraScanParser is meant to help you maximize its benefits.
yaraScanParser allows you to:
- Save time by parsing the Yara Scan Service results automatically
- Get information about wanted matches and false positives of your rule
- Get the matched files' hash values in a format that can be easily inserted to your Yara rule's metadata section
Built With
Getting Started
To use this tool, you must have Python installed.
Installation
Clone the repo
git clone https://github.com/Sh3llyR/yaraScanParser.gitUsage
- Parameters -o and -m are OPTIONAL
- When -o parameter is omitted, the output file is saved in the script's directory
- When -m parameter is omitted, the value of the first 'malware' key in the JSON file is used
Usage examples:
- python yaraScanParser.py -i yara_scan_service_results.json -o output.txt -m CobaltStrike
- python3 yaraScanParser.py -i yara_scan_service_results.json
Contact
Project Link: https://github.com/Sh3llyR/yaraScanParser