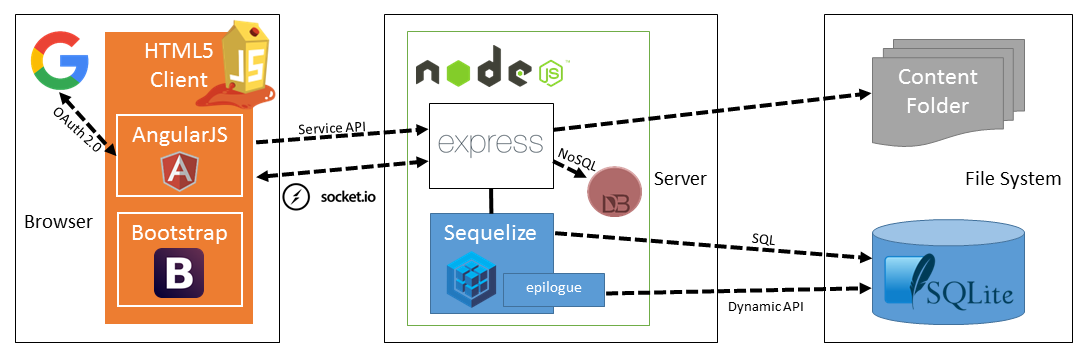
OWASP Juice Shop is an intentionally insecure web app for security trainings written entirely in Javascript which encompasses the entire OWASP Top Ten and other severe security flaws.
Juice Shop is written in Node.js, Express and AngularJS. It was the first application written entirely in JavaScript listed in the OWASP VWA Directory.
The application contains over 30 challenges of varying difficulty where the user is supposed to exploit the underlying vulnerabilities. The hacking progress is tracked on a score board. Finding this score board is actually one of the (easy) challenges!
Apart from the hacker and awareness training use case, pentesting proxies or security scanners can use Juice Shop as a "guinea pig"-application to check how well their tools cope with Javascript-heavy application frontends and REST APIs.
Translating "dump" or "useless outfit" into German yields "Saftladen" which can be reverse-translated word by word into "juice shop". Hence the project name. That the initials "JS" match with those of "Javascript" was purely coincidental!
- Easy-to-install: Choose between node.js, Docker and Vagrant to run on Windows/Mac/Linux
- Self-contained: Additional dependencies are pre-packaged or will be resolved and downloaded automatically
- Self-healing: The simple SQLite database is wiped and regenerated from scratch on every server startup
- Gamification: On a Score Board the application keeps track of successfully exploited vulnerabilities
- Free and Open source: Licensed under the MIT license with no hidden costs or caveats
Feel free to have a look at the latest version of OWASP Juice Shop: https://juice-shop.herokuapp.com
This is a deployment-test and sneak-peek instance only! You are not supposed to use this instance for your own hacking endeavours! No guaranteed uptime! Guaranteed stern looks if you break it!
- Click the button below and follow the instructions
This is the quickest way to get a running instance of Juice Shop! If you have forked this repository, the deploy button will automatically pick up your fork for deployment! As long as you do not perform any DDoS attacks you are free to use any tools or scripts to hack your Juice Shop instance on Heroku!
- Install node.js
- Run
git clone https://github.com/bkimminich/juice-shop.git(or clone your own fork of the repository) - Run
npm install(only has to be done before first start or when you change the source code) - Run
npm start - Browse to http://localhost:3000
- Install Docker
- Run
docker pull bkimminich/juice-shop - Run
docker run -d -p 3000:3000 bkimminich/juice-shop - Browse to http://localhost:3000 (on macOS browse to http://192.168.99.100:3000 instead)
- Install and launch Docker Toolbox
- Search for
juice-shopand click Create to download image and run container - Click on the Open icon next to Web Preview to browse to OWASP Juice Shop
- Install a 64bit node.js on your Windows (or Linux) machine
- Download
juice-shop-<version>_<node-version>_<os>_x64.zip(or.tgz) attached to latest release - Unpack and run
npm startin unpacked folder - Browse to http://localhost:3000
Each packaged distribution includes some binaries for SQLite bound to the OS and node.js version which
npm installwas executed on.
- Setup an Amazon Linux AMI instance
- In Step 3: Configure Instance Details unfold Advanced Details and copy the script below into User Data
- In Step 6: Configure Security Group add a Rule that opens port 80 for HTTP
- Launch instance
- Browse to your instance's public DNS
#!/bin/bash
yum update -y
yum install -y docker
service docker start
docker pull bkimminich/juice-shop
docker run -d -p 80:3000 bkimminich/juice-shop
Technically Amazon could view hacking activity on any EC2 instance as an attack on their AWS infrastructure! We highly discourage aggressive scanning or automated brute force attacks! You have been warned!
- Install Vagrant and Virtualbox
- Run
git clone https://github.com/bkimminich/juice-shop.git(or clone your own fork of the repository) - Run
cd vagrant && vagrant up - Browse to http://juice.sh
OWASP Juice Shop officially supports the following versions of node.js and offers Docker images and packaged distributions accordingly:
| node.js | Docker images | Docker snapshots | Packaged distributions |
|---|---|---|---|
| 4.x | node4 |
node4-snapshot, node4-develop |
juice-shop-<version>_node4_windows_x64.zip, juice-shop-<version>_node4_linux_x64.tgz |
| 6.x | latest, node6 |
snapshot, develop, node6-snapshot, node6-develop |
juice-shop-<version>_node6_windows_x64.zip, juice-shop-<version>_node6_linux_x64.tgz |
| 7.x | node7 |
node7-snapshot, node7-develop |
juice-shop-<version>_node7_windows_x64.zip, juice-shop-<version>_node7_linux_x64.tgz |
The stable Docker images are built from
masterwhile the snapshot images are built fromdevelopbranch. The latter contain unreleased features but cannot be considered stable.
If you need help with the application setup please check the Troubleshooting section below or post your specific problem or question in the official Gitter Chat.
- After changing to a different Node.js version it is a good idea to
delete
npm_modulesand re-install all dependencies from scratch withnpm install - If you are experiencing
Error 128 from some GitHub
repos during
bower installexecution, rungit config --global url."https://".insteadOf git://and trynpm installagain - If using Docker Toolbox on Windows make sure that you also enable port
forwarding from Host
127.0.0.1:3000to0.0.0.0:3000for TCP for thedefaultVM in VirtualBox - If
npm installfails after an update of your local copy duringbower installcomplaining about version issues, delete/app/bower_componentsand try again to remove outdated versions that cause conflicts - If during
npm installthesqlite3no binaries can be downloaded for your system, the setup falls back to building from source withnode-gyp. Check thenode-gypinstallation instructions for additional tools you might need to install (e.g. Python 2.7, GCC, Visual C++ Build Tools etc.) - If
npm installfails on Ubuntu (e.g. while installing PhantomJS) you might have to install a recent version of Node.js and try again. - Using the Vagrant script (on Windows) might not work while your virus scanner is running. This problem was experienced at least with F-Secure Internet Security.
- You may find it easier to find vulnerabilities using a pen test tool. I strongly recommend Zed Attack Proxy which is open source and very powerful, yet beginner friendly.
- If you are missing the 'Login with Google' button and want to test all the challenges out you will want to add your deployed Heroku URL to /app/js/controllers/LoginController.js. Simply update the variable: authorizedRedirectURIs on line 43 to include your URL object, use your URL for both the property name and value. You can just copy line 44 and then paste/modify to include your URL. Once you have this done you will also need to setup oauth on google's end here: https://console.developers.google.com/apis/library, clicking 'Credentials' and clicking 'Create credentials.' Once you have setup your credentials, you will want to update the clientId variable in /app/js/controllers/LoginController.js on line 42 to use your new oauth client id from Google. and re-deploy it to Heroku, once completed you will have the option to login with Google on the login page. One thing to note, make sure that you setup the redirect_uri to match your app's URL, if you for some reason have to modify the redirect_uri this gets cached on Google's end and takes longer than you'll want to wait to reset.
Found a bug? Crashed the app? Broken challenge? Found a vulnerability that is not on the Score Board?
Feel free to create an issue or post your ideas in the chat! Pull requests are also highly welcome - please refer to CONTRIBUTING.md for details.
💡 indicates resources that contain hints for solving challenges of the OWASP Juice Shop. These are supposed to be helpful whenever you get stuck.
indicates resources that spoiler entire challenge solutions so you might not want to view them before tackling these challenges yourself!
This is the official companion guide to the OWASP Juice Shop. It will give you a complete overview of the vulnerabilities found in the application including hints (:bulb:) how to spot and exploit them. In the appendix you will even find complete step-by-step solutions (:trollface:) to every challenge. Pwning OWASP Juice Shop is published with GitBook under CC BY-NC-ND 4.0 and is available for free in HTML, PDF, Kindle and ePub format.
- Introduction Slide Deck in HTML5
- Lightning Talk Slides
for a 10min project introduction runthrough
- What's new in OWASP Juice Shop for a 10min update on the newest features of 2016
- PDF of the Intro Slide Deck on Slideshare
Did you write a blog post, magazine article or do a podcast about or mentioning OWASP Juice Shop? Send a Pull Request so we can add it to the list! The same goes for conference or meetup talks, workshops or trainings you did where you included this project!
- Blog post on IncognitJoe:
Hacking(and automating!) the OWASP Juice Shop

- Automated solving script for the OWASP Juice Shop
written in Python as mentioned in above blog post

- Automated solving script for the OWASP Juice Shop
written in Python as mentioned in above blog post
- 7 Minute Security Podcast:
- Episode #229: 7MS #229: Intro to Docker for Pentesters (Youtube)
- Episode #230:
7MS #230: Pentesting OWASP Juice Shop - Part 1
(Youtube)

- Episode #231:
7MS #231: Pentesting OWASP Juice Shop - Part 2
(Youtube)

- Episode #232:
7MS #232: Pentesting OWASP Juice Shop - Part 3
(Youtube)

- Episode #233:
7MS #233: Pentesting OWASP Juice Shop - Part 4
(Youtube)

- Episode #234:
7MS #234: Pentesting OWASP Juice Shop - Part 5
(Youtube)

- German guest post on Informatik Aktuell: Juice Shop - Der kleine Saftladen für Sicherheitstrainings
- Guest post on The official Sauce Labs Blog: Proving that an application is as broken as intended
- Teaser post on Björn Kimminich's Blog: Juice Shop
- Lightning Talk: What's new in OWASP Juice Shop, German OWASP Day 2016, 29.11.2016
- Gothenburg pwns the OWASP Juice Shop, OWASP Gothenburg Day 2016, 24.11.2016
- Hacking the OWASP Juice Shop, OWASP NL Chapter Meeting, 22.09.2016 (Youtube, :trollface: in last 10min)
- Hacking-Session für Developer (und Pentester), Kieler Open Source und Linux Tage, 16.09.2016
- Security-Auditing aus der Cloud – Softwareentwicklung kontinuierlich auf dem Prüfstand, SeaCon 2016, 12.05.2016
- Hacking the Juice Shop ("So ein Saftladen!"), JavaLand 2016, 08.03.2016
- Hacking the JuiceShop! ("Hackt den Saftladen!"), node.HH Meetup: Security!, 03.02.2016
- Lightning Talk: Hacking the Juice Shop ("So ein Saftladen!"), German OWASP Day 2015, 01.12.2015
- Juice Shop - Hacking an intentionally insecure Javascript Web Application, JS Unconf 2015, 25.04.2015
- So ein Saftladen! - Hacking Session für Developer (und Pentester), 17. OWASP Stammtisch Hamburg, 27.01.2015
- On Spreadshirt.com and Spreadshirt.de you can get some swag (Shirts, Hoodies, Mugs) with the official OWASP Juice Shop logo
- On Stickermule.com you can get four variants of the OWASP Juice Shop logo to decorate your laptop
An alternative way to get stickers (and maybe even a pin-back button) is to somehow contribute to the project by fixing an issue, finding a serious bug or submitting a good idea for a new challenge! We're also happy to send some stickers your way if you organize a meetup or conference talk where you use or mention OWASP Juice Shop! Just contact the project leader to discuss your plans: bjoern.kimminich@owasp.org!
PayPal donations via above button go to the OWASP Foundations and are earmarked for "Juice Shop". This is the preferred way to support the project.
Inspired by the "classic" BodgeIt Store by @psiinon.
Ordered by date of first contribution. Auto-generated on Sun, 18 Dec 2016 18:01:55 GMT.
- Björn Kimminich aka
bkimminich - Aaron Edwards aka
aaron-edwards - Alec Brooks aka
alecbrooks - wurstbrot
- Dinis Cruz aka
DinisCruz - Gorka Vicente aka
gorkavicente - Alvaro Viebrantz aka
alvarowolfx - Johanna A aka
yuhama - Stephen OBrien aka
stephenobrien
This program is free software: you can redistribute it and/or modify it under the terms of the MIT license. OWASP Juice Shop and any contributions are Copyright © by Bjoern Kimminich 2014-2017.